Permiso State of Identity Security Report 2026: From False Confidence to True Visibility
%20(1).png)
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Permiso Security today released its 2026 State of Identity Security Report, the third annual benchmark examining how organizations manage, secure, and gain visibility into identities across cloud environments. Based on responses from over 500 security and identity professionals worldwide, this year's findings reveal a sobering reality: the gap between what organizations believe they can see and what they actually control has never been wider.
The headline finding? Comprehensive identity visibility plummeted from 93% in 2024 to just 46% in 2025. That's a 47-point drop in a single year—the largest confidence correction we've ever recorded in identity security research.
But here's what makes this interesting: the technology didn't get worse. The threats didn't suddenly multiply overnight. Cloud adoption didn't accelerate dramatically compared to prior years.
What changed was the question.
In 2024, we asked if organizations maintained a comprehensive inventory. In 2025, we asked if they had comprehensive visibility. The difference between those two words explains everything that's broken about identity security right now.
An inventory is a list. You generate it, file it away, and check a compliance box. Visibility is dynamic. It's real-time tracking of what identities are doing, where they're going, and what they could access if compromised. Most organizations have the list. Almost none have the visibility.
Testimonials
“Organizations are finally being honest about what they can't see. The 47-point drop isn't a collapse in capability, but rather a lack in having real-time visibility into what identities are actually doing. You can't detect what you can't see, and the answer to this major issue is simple: unified visibility.”
Jason Martin
Co-CEO at Permiso SecurityWhen we followed up with more specific questions, the confidence kept dropping. Only 54% could track identity permissions and activities across all platforms in a unified view. Only 43% could detect identity-based risks before incidents occurred. And when we asked how many could both detect threats quickly and determine blast radius within minutes, the number fell to 23%. This is what we call The Visibility Illusion Cascade.
Identity Is No Longer An Attack Vector. It's THE Attack Vector.
While visibility was collapsing, identity-based attacks were surging. Seventy-seven percent of organizations now report that identity compromise accounts for at least a quarter of all security incidents. For 44%, identity-related incidents represent 26-50% of their total incident volume.
Think about that for a moment. When half of your security incidents stem from compromised identities, you're not primarily fighting network attackers or malware. You're fighting adversaries who bypass your perimeter entirely by logging in with valid credentials.
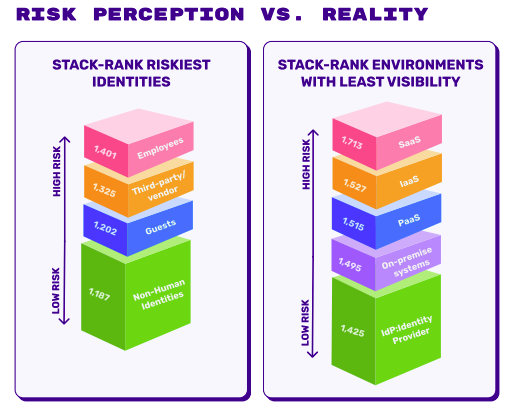
Yet when we asked organizations to rank their riskiest identity types, employees topped the list while SaaS environments (where employees work daily) had the worst visibility of any platform. The highest-risk identities operate in the lowest-visibility environment. That's not a security gap. That's a security chasm.
The most sobering finding? Seventy-one percent of organizations believe better identity visibility could have prevented 26-75% of their security incidents. Up to 75% of security incidents could have been prevented with better identity visibility. That's what 25% of organizations believe. Another 46% say up to half were preventable.
Organizations aren't ignorant about the solution. They know what would fix the problem. They just can't implement it.
The AI Identity Tsunami Has Already Made Landfall
If the visibility crisis represents the present state of identity security, AI represents its immediate future. And that future arrived faster than anyone expected. AI isn't a pilot program anymore. It's not isolated in sandboxes or limited to experimental use cases. AI agents are operating in production environments right now, accessing sensitive data, creating identities autonomously, and fundamentally rewriting how organizations think about identity management. Most security teams deployed AI before they built the frameworks to govern it.
The scale of AI's penetration into enterprise environments is staggering:- 92% already have AI agents accessing production or sensitive data - for 39%, AI systems have access to 26-50% of their sensitive data including customer records, financial information, intellectual property, and trade secrets
- 95% said AI systems could create or modify identities without traditional human oversight - no ticketing system, no approval workflow, no audit trail in the traditional sense
- 91% expect AI-generated identities to increase in 2026 - this is universal, with only 9% expecting no growth
- 25% expect AI identities to double or triple - not incremental growth, but exponential expansion that will overwhelm existing identity management processes
This is the AI Identity Tsunami. Organizations are deploying AI systems faster than they can secure them, granting access faster than they can track it, and generating identities faster than they can manage them. The visibility gap isn't closing. It's accelerating.
Testimonials
“The challenge with AI agents isn't that they're accessing data. The challenge is that most organizations don't have visibility into which AI systems have access, what permissions they hold, or what they're doing with the data. These are non-human identities on steroids, with access patterns that traditional monitoring can't detect.”
Paul Nguyen
Co-CEO at Permiso SecurityThe Hidden Tax Everyone Pays
The operational cost of fragmented identity visibility manifests in what organizations are spending on manual work that unified platforms could automate.
Seventy-one percent of organizations use between 3 and 10 separate tools just to achieve identity visibility. Your IdP shows authentication. Your CSPM shows cloud identities. Your SIEM shows access logs. But no single tool shows the complete picture.
The result: 60% of organizations spend 10-40 hours per week manually correlating identity data from different sources. Another 20% spend 41-80 hours weekly. That's not a rounding error. That's $31,000 to $250,000+ annually per organization in direct labor costs.
But the real cost isn't the money. It's the opportunity cost. Every hour spent manually correlating identity data is an hour not spent hunting threats, improving defenses, or responding to incidents. Security teams didn't sign up to be data janitors. Yet that's what fragmented tooling has made them.
The detection-response gap tells the same story. While 79% of organizations can now detect identity-based threats within 24 hours (up from 61% in 2024, an encouraging 18-point improvement), only 29% can determine blast radius within minutes. The math is brutal: only 23% possess both rapid detection and rapid response capability.
The remaining 77% face critical delays during the exact moments when speed matters most. They know something is wrong. They know credentials were compromised. But while analysts spend hours reconstructing attack paths and mapping lateral movement possibilities, attackers are already three steps ahead.
The Credential Graveyard Keeps Growing
Non-human identities represent one of the starkest examples of the gap between confidence and capability. Organizations express 95% confidence in their inventory of non-human identities with access to critical systems. Yet when we examined the processes supporting that confidence, only 27% had achieved full automation for both discovering new non-human identities and managing their lifecycles.
The other 73%? They're managing thousands of service accounts, API keys, and access tokens with immature processes while expressing near-universal confidence in the results.
Half the industry discovers new non-human identities only through periodic audits or during incidents rather than through real-time automated discovery. By the time they find them, those identities have been active for weeks or months.
The consequences appear in what we call The Credential Graveyard Problem. Sixty-nine percent of organizations admit that 11-50% of their credentials are expired or unused but still active in production environments. These are service accounts from decommissioned applications, API keys for tools no longer in use, and certificates that expired months ago but still authenticate successfully.
For an organization managing 10,000 non-human identities, that's potentially 2,000 to 5,000 zombie credentials waiting to be discovered by attackers. Each one represents a skeleton key to infrastructure that no one is actively monitoring.
The Market Is Responding
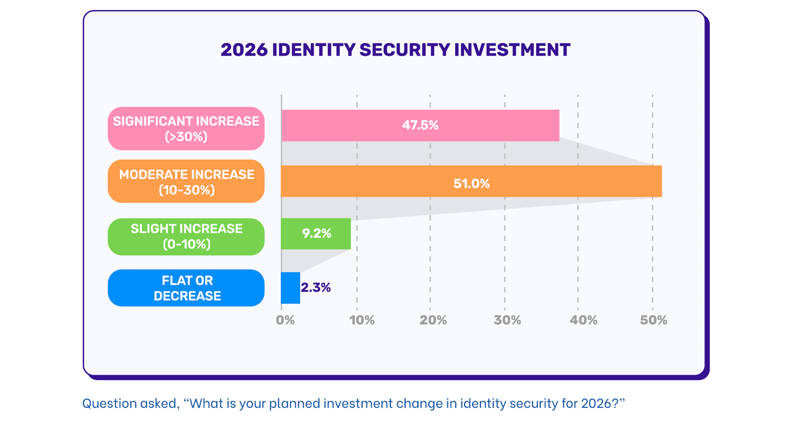
Despite the sobering findings, hope emerges in the investment data. Eighty-nine percent of organizations plan to increase identity security investment in 2026. Thirty-eight percent are planning significant increases over 30%. This represents one of the strongest investment signals we've ever seen in identity security.
The spending surge makes sense. When 77% of incidents are identity-related, when 71% believe better visibility could prevent up to three-quarters of those incidents, and when AI is generating thousands of new identities that existing tools can't track, CFOs can't argue against investment.
When we asked what capabilities would most improve security posture, organizations didn't ask for more tools. They asked for real-time threat detection (65%) and unified cross-platform visibility (43%). The emphasis on unified visibility makes it clear that the next frontier of identity security isn't more alerts or more dashboards. It's building a foundation where teams can actually see what's happening with every identity, in real time, across every platform.
What Comes Next
The 2026 State of Identity Security Report documents an industry at an inflection point. The visibility organizations thought they had doesn't exist. The AI-generated identities they're deploying are multiplying faster than legacy tools can track. The manual processes propping up false confidence are burning hundreds of thousands of dollars annually while leaving critical security gaps.
But the investment surge suggests the market has recognized the problem. The 18-point improvement in detection speeds shows that when organizations commit resources to identity security, measurable progress follows.
The organizations that will thrive in 2026 aren't the ones with the most tools or the longest feature lists. They're the ones that achieve unified visibility, automate what can be automated, and close the gap between detection and response before attackers exploit it.
The full report includes detailed analysis across 28 questions, year-over-year trend comparisons, and analytical frameworks for measuring your organization's identity security maturity. Download it to see where your organization stands.
The visibility gap won't close itself. But now we know exactly how wide it is.



.png)




.png?width=2184&height=270&name=State%20of%20Identity%20Security%20Survey%202026%20Yeti%20(728x90).png)
.png?width=1090&height=281&name=State%20of%20Identity%20Security%20Survey%202026%20Yeti(970x250).png)