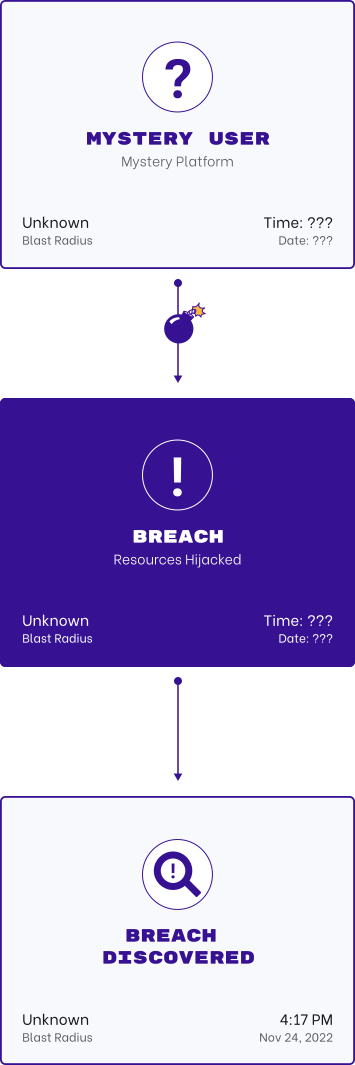
Secure All Non-Human Identities
Inventory non-human identities and monitor them for suspicious and malicious activity
Permiso inventories all of your human AND non-human identities including keys, tokens, service accounts, roles and groups in your Iaas, Paas and Saas environments. Identify orphaned, stale and overly permissive NHIs across cloud environments.
End to End Non-Human Identity Security
Universal Identity Graph
Permiso inventories and monitors all of your API Keys, Access Tokens, and other secrets in your identity providers, IaaS, Paas, SaaS environments via the Universal Identity Graph
NHI Risk Posture
Permiso helps teams identify inactive, overly permissive, stale and orphaned non-human identities, wherever they live in your cloud or on-prem environments.
Runtime monitoring
Permiso monitors the behavior of the non-human identities and the humans that are using them in order to detect suspicious and malicious activity in minutes.
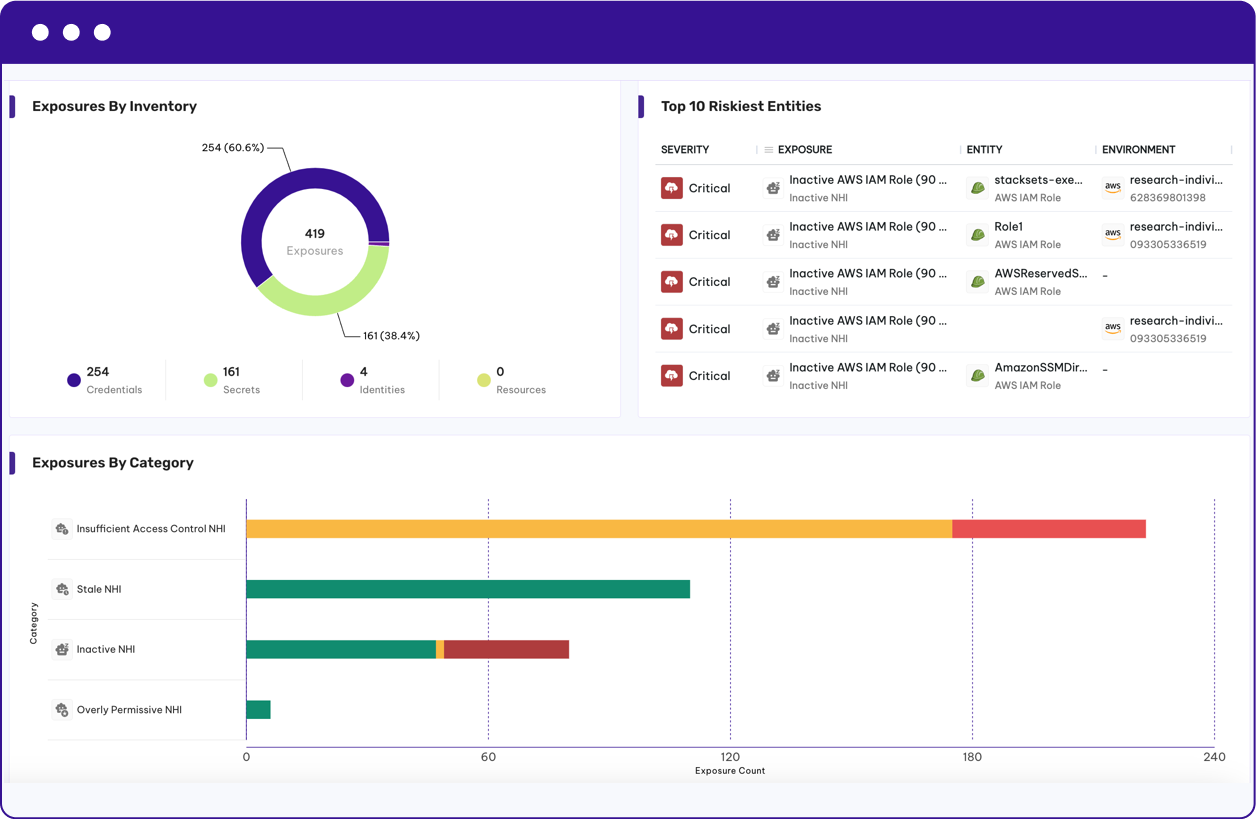
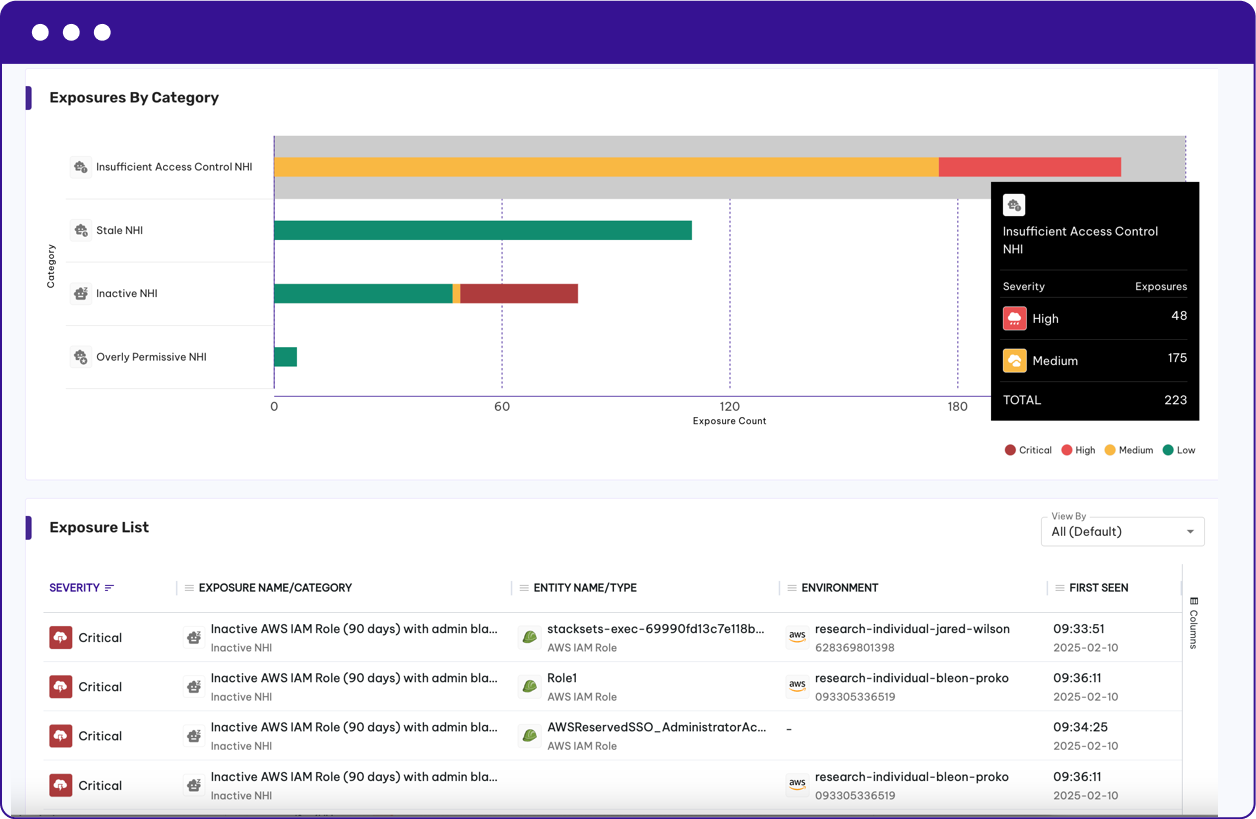
Minimize Risk Exposure for Non-Human Identities
Permiso provides a centralized dashboard to monitor all of your NHIs. Gain quick visibility into the exposures of your non-human identities by identifying:
- Insufficient access control
- Stale secrets, tokens and keys
- Inactive credentials, roles and service accounts
- Overly permissive policies



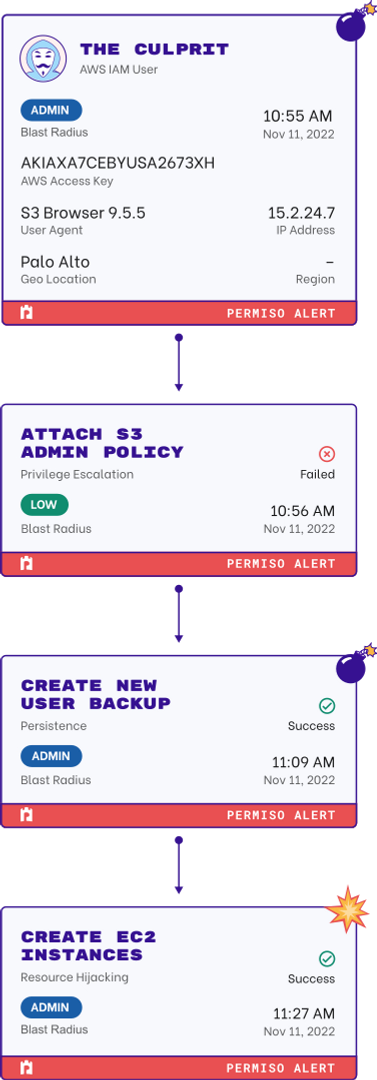
Runtime Monitoring for All NHIs
Monitor all of your non-human identities in real-time. Permiso tracks all of your keys, tokens, credentials and service accounts across identity providers, IaaS environments, PaaS services and SaaS applications.
We'll tell you who is using what non-human identities in those environments, and quickly identify anomalous activity of those NHIs to detect suspicious and malicious behavior.
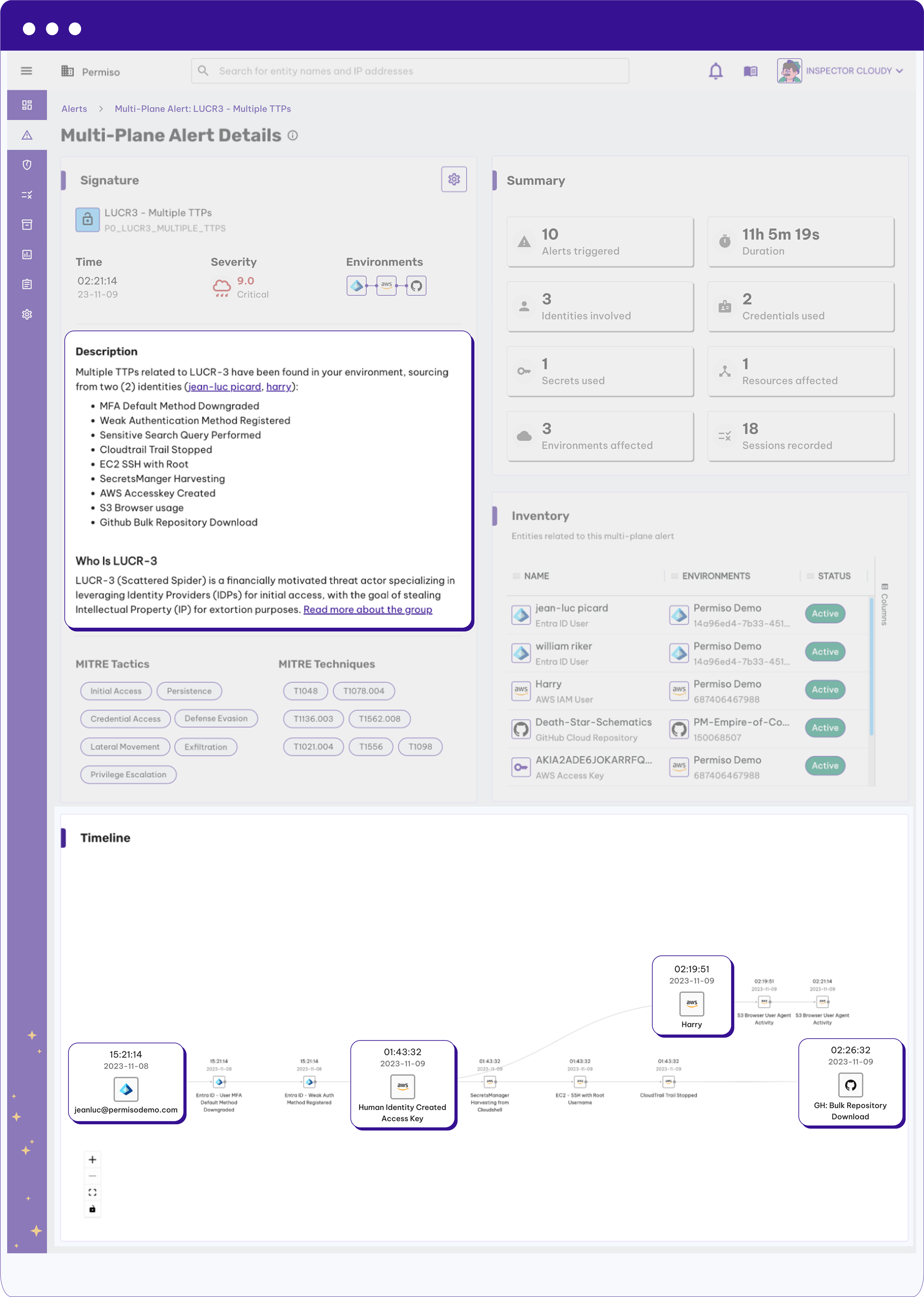
How Permiso Protects All of Your Non-Human Identities




Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWPP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.



Permiso has proven to be indispensable to the way we manage and secure identities across multiple cloud environments.

Permiso's ability to track identities and their activities across Iaas, Saas and identity providers at runtime is unlike any of our existing solutions.

Identity is the silver bullet in the cloud. If you don't get it right, you're dead!



Get in Touch
Request a demo, get more deets, or just say hi.



.png)