Identity Security Posture Management
Inventory all of your human and non-human identities and assess exposure risk
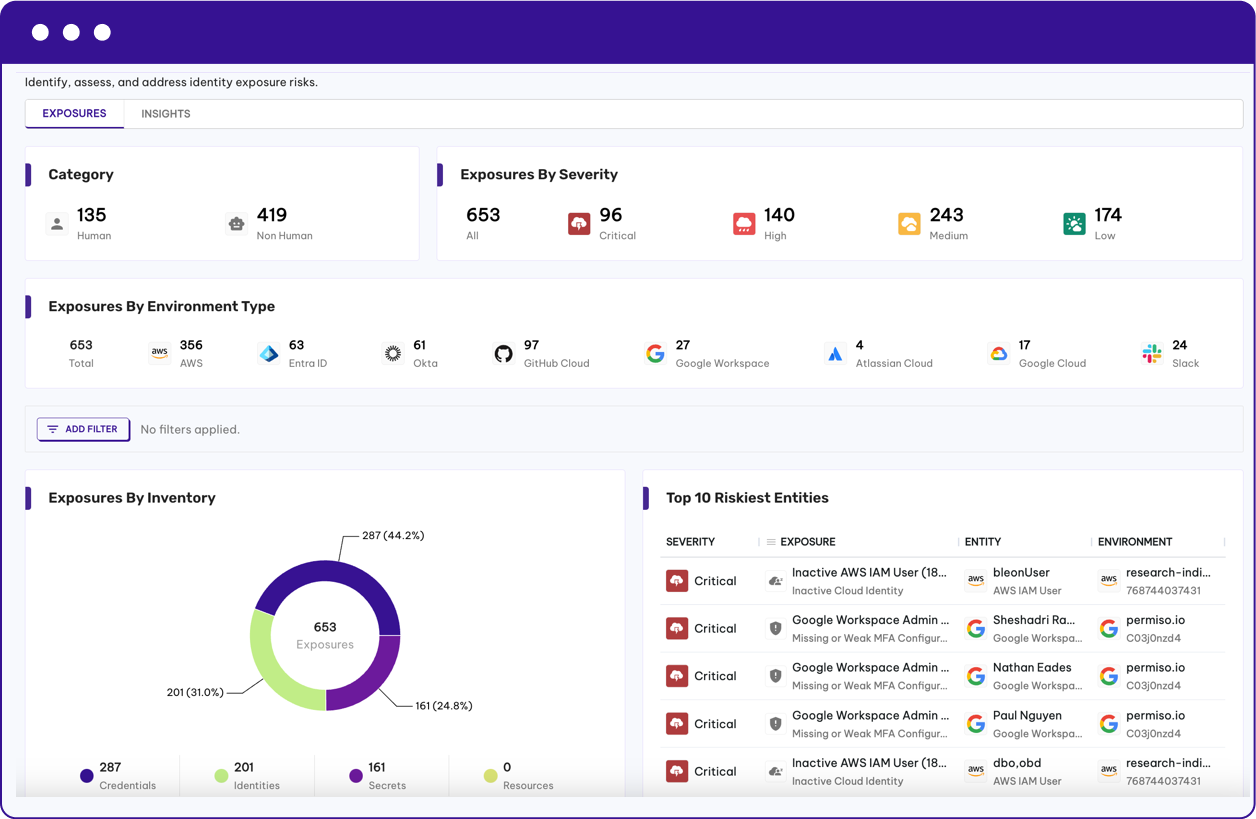
Permiso provides a comprehensive inventory all of your human and non-human identities across all of your cloud environments. Assess exposure risk and identify those identities are most likely to be compromised.
Universal Identity Graph
Comprehensive identity security coverage by stitching all user activity together across identity providers, IaaS, Paas and SaaS environments.
Threat Driven Exposure Analysis
1,500+ detection signals from the P0 labs research team to drive threat informed posture controls that minimize the likelihood of a breach.
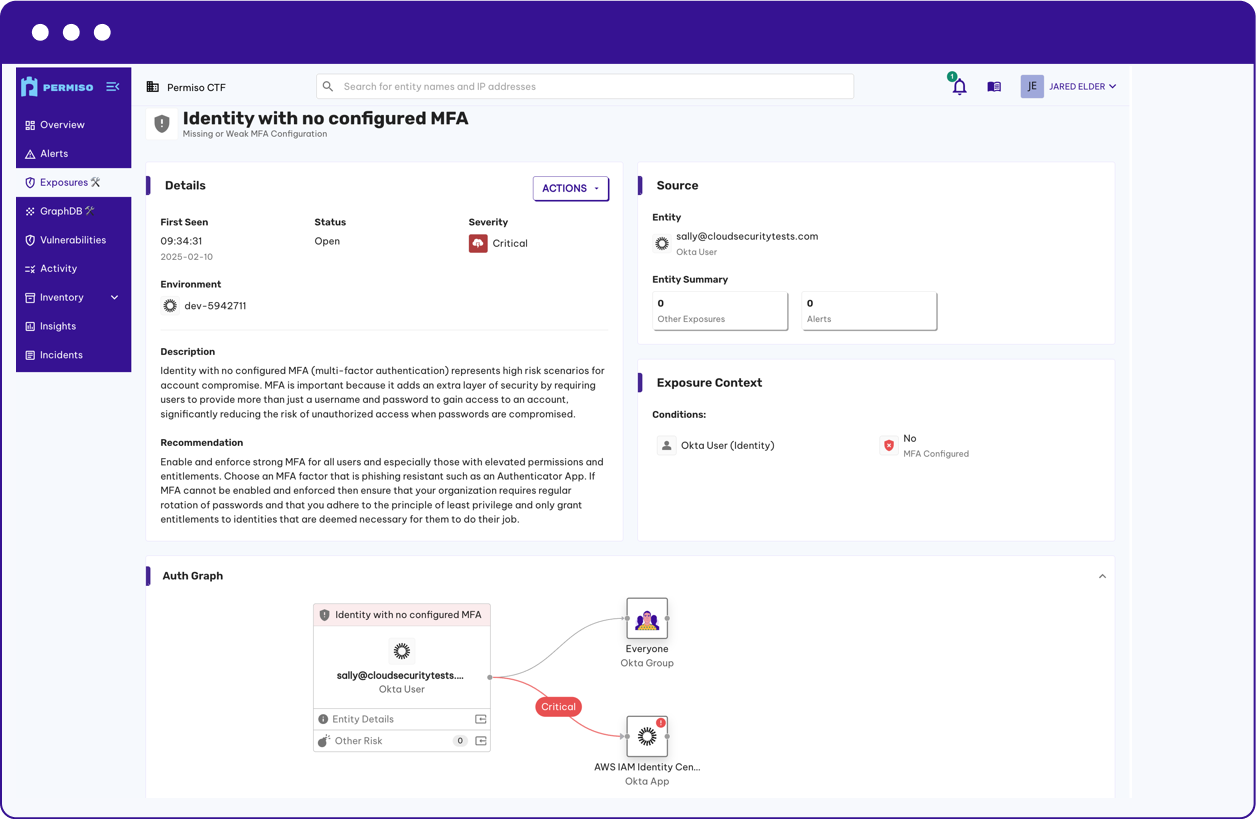
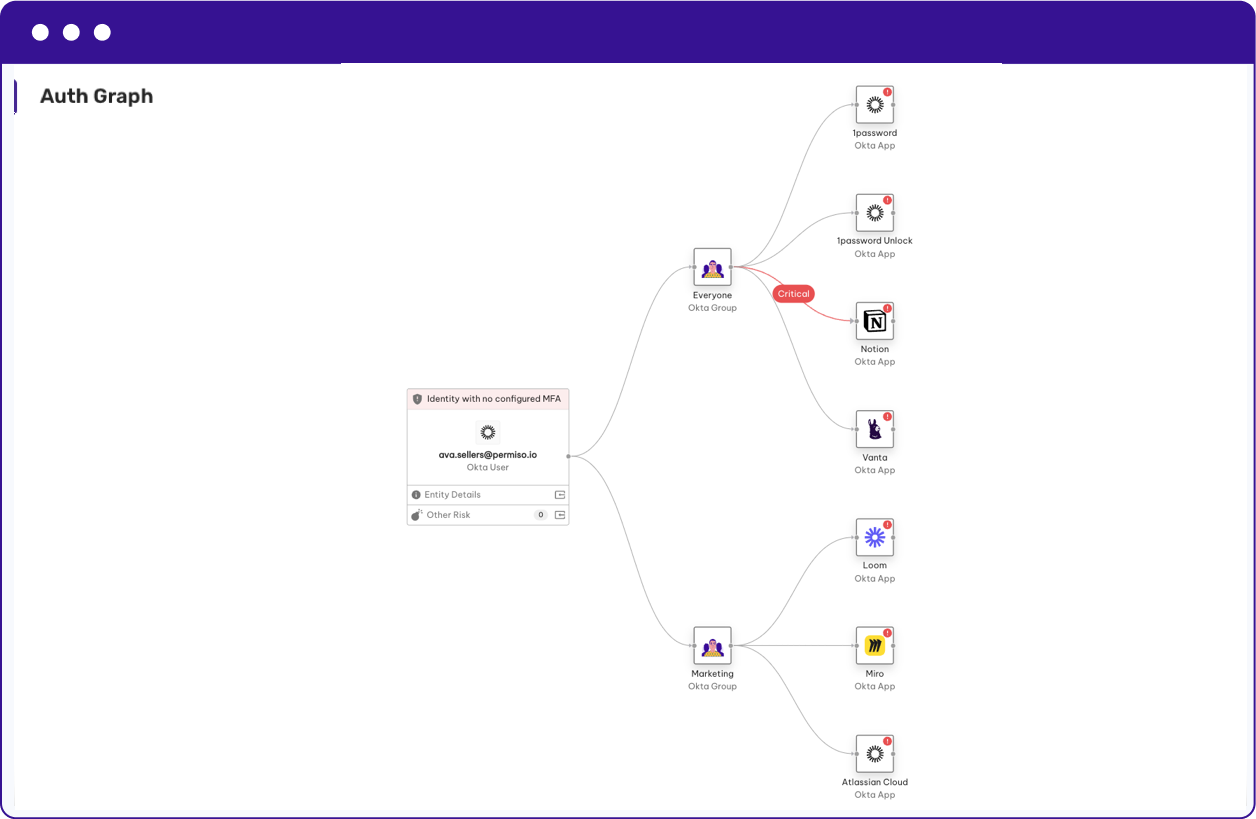
Identity Attack Paths
Visualizations of different ways threat actors could compromise identities in order to move laterally and gain access to sensitive data.
Strengthen Authentication Controls
Prevent the likelihood of compromise of both human and non human identities. Understand where MFA isn't being used, monitor the age and rotation of password and access keys. Get insights into the devices that are being used by your identities.



Reduce Excessive Privileges
Minimize the chances of identity compromise by reducing the privileges of your identities. Minimize the attack surface to prevent credential compromise, thwart insider threat and eliminate privilege creep across identity providers, IaaS, PaaS and SaaS environments - all in one platform.
.png)
Remove Zombie Identities & Accounts
Prevent the likelihood of compromise and limit the blast radius of all of your human and non-human identities in the event they were to be compromised. Remove zombie accounts and identities (including vendors) that are no longer active in your environments.
How Permiso Protects All of Your Identities



Permiso has proven to be indispensable to the way we manage and secure identities across multiple cloud environments.

Permiso's ability to track identities and their activities across Iaas, Saas and identity providers at runtime is unlike any of our existing solutions.

Identity is the silver bullet in the cloud. If you don't get it right, you're dead!



Get in Touch
Request a demo, get more deets, or just say hi.





.png)


