Detect Insider Risk
Detect anomalous insider activity
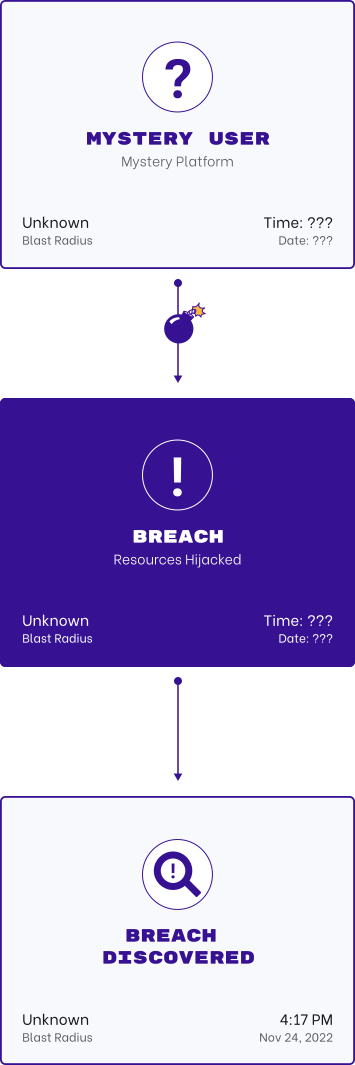
Insider risk can manifest in the form of disgruntled employees or contractors wanting to steal sensitive data or cause harm. It also occurs months before they leave the organization or are detected.
Insider Risk Often Goes Unnoticed
Existing security tools do a poor job of detecting and preventing insider threats, because these tools often lack the necessary context across multiple environments.




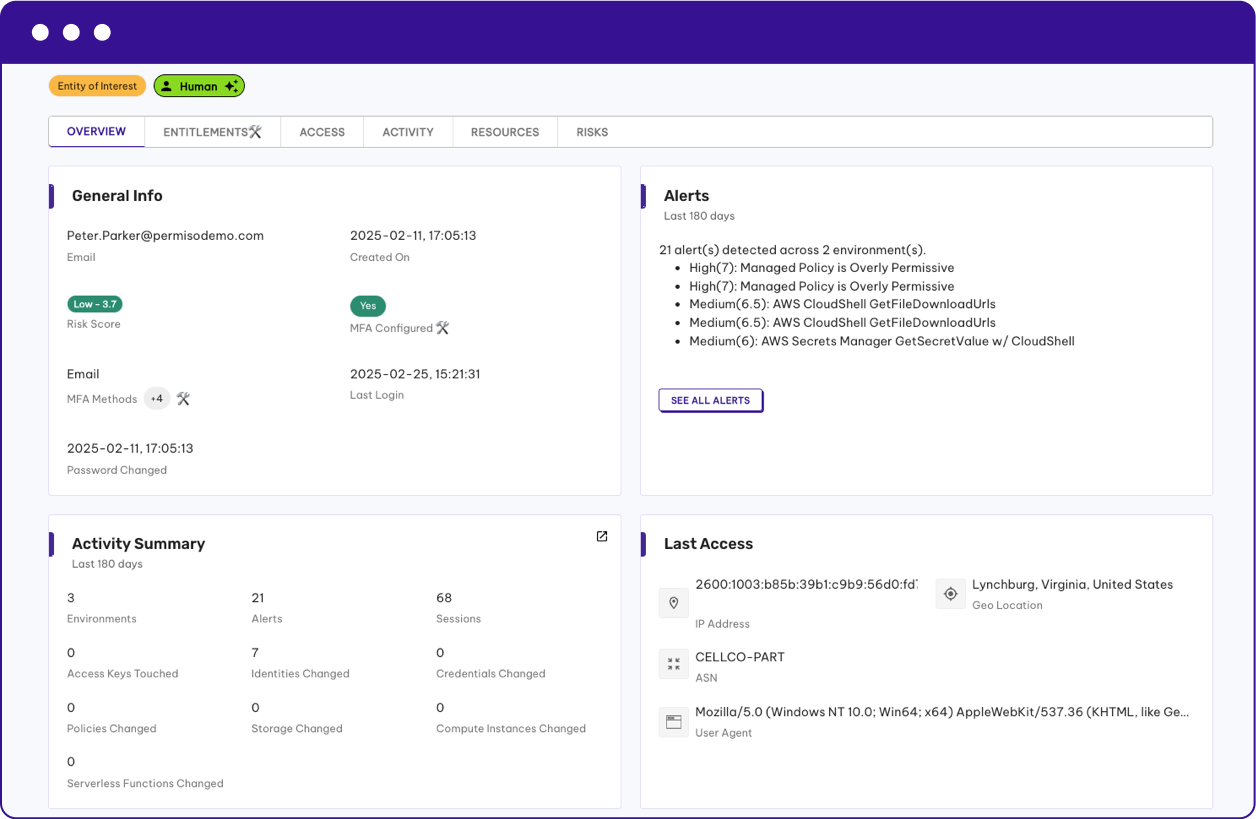
Detect Insider Risk As It Happens
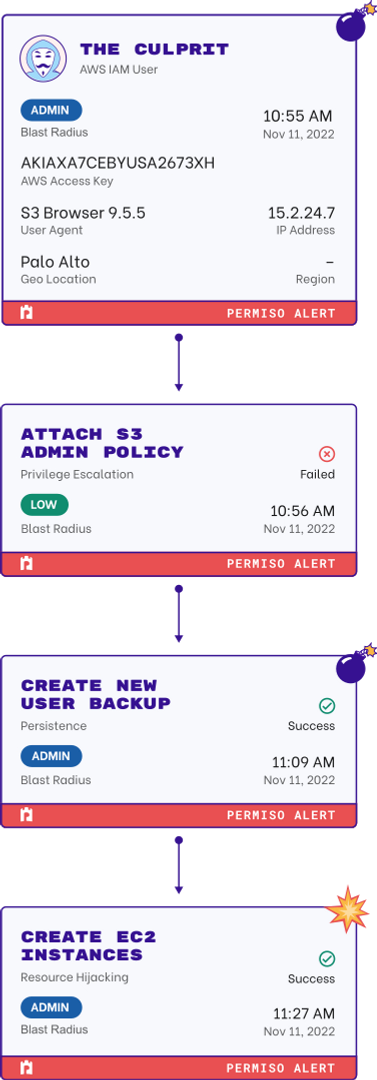
Through the power of Permiso’s universal identity graph you now have the ability to track the full identity lineage across multiple environments from a single pane of glass. Combined with watchlists for risky identities means that any malicious insider activity is detected immediately and across all environments.
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?




.png)