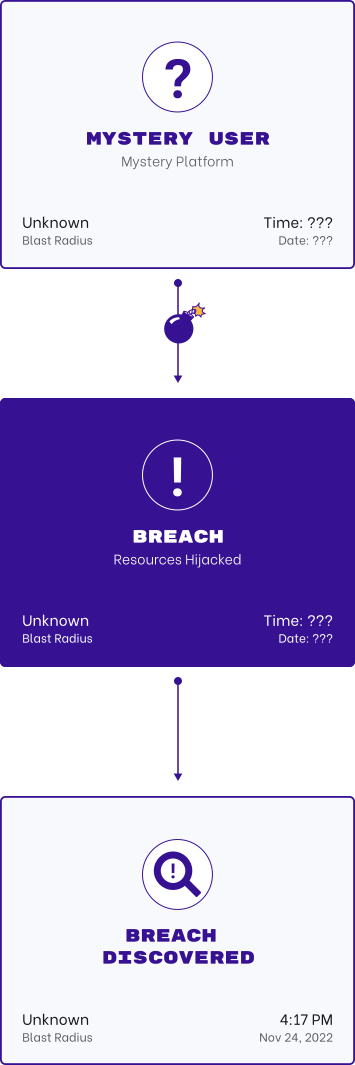
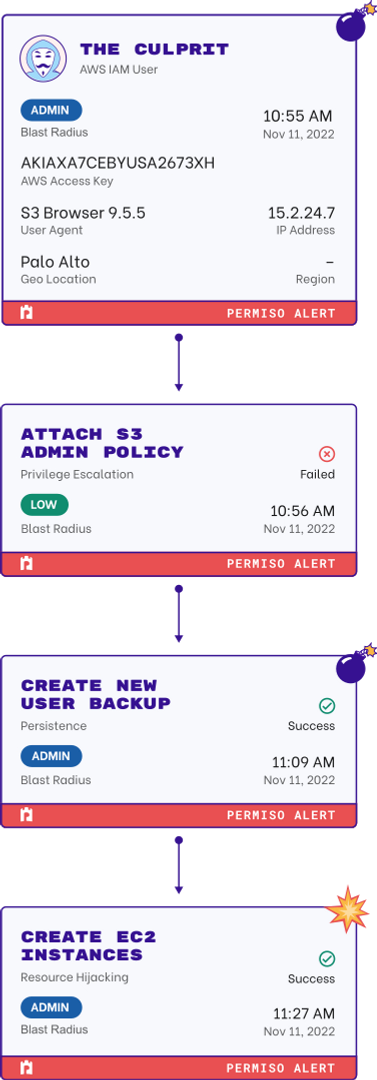
Detect Compromised Credentials
BAD GUYS HAVE THE CREDS
Threat actors have the creds to your kingdom. Being able to track who provisioned credentials, where and how they are being used, and when they’re being shared is a moving target security teams.

DETECT WHEN CREDS GO BAD
Securing your credentials is more than rotating keys. Many solutions that monitor the provisioning, entitlements and the state of secrets, but don’t have visibility into how they’re being used or who has access to them.
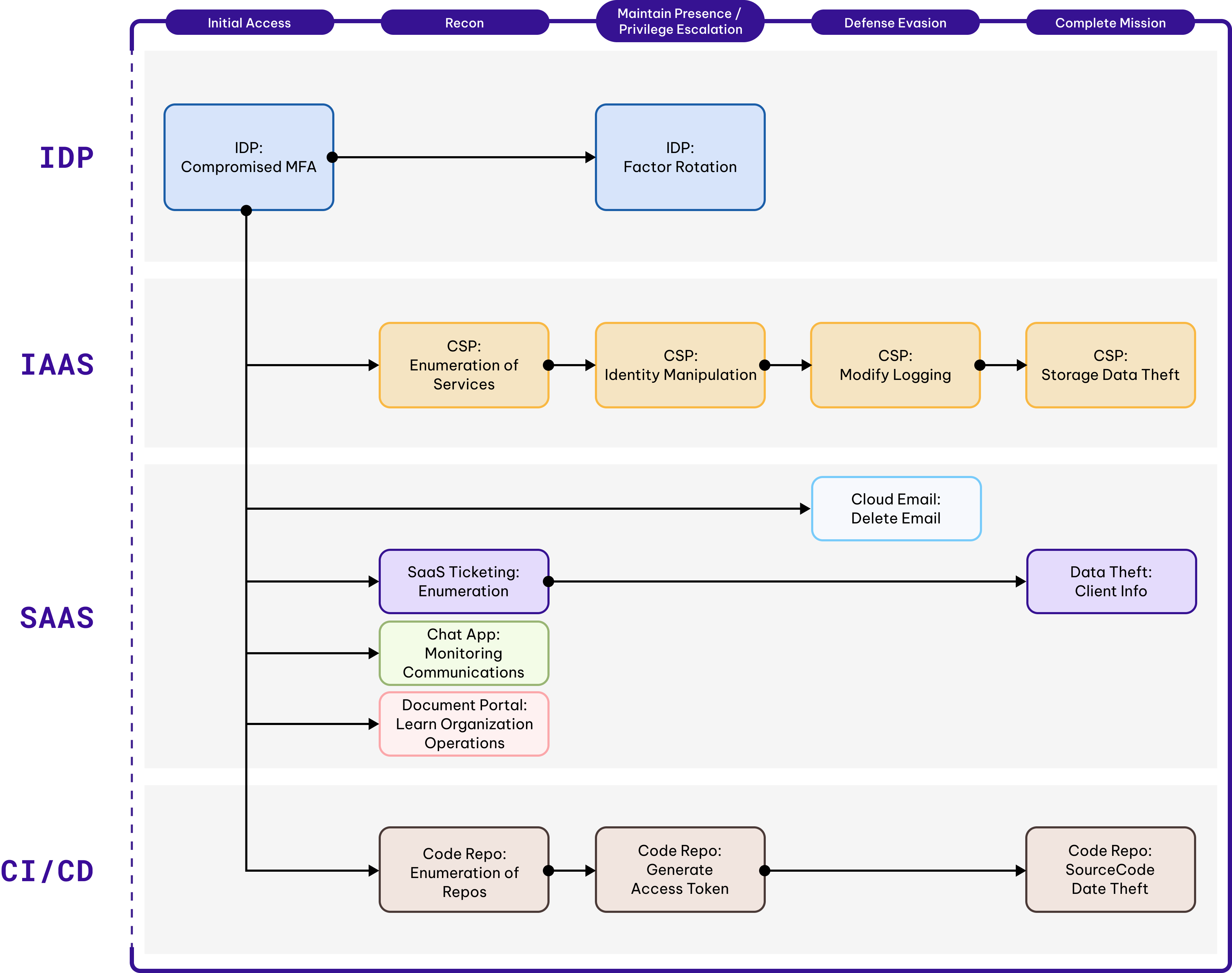



How Permiso Detects Credential Compromise
If you want to secure non-human identities, you need to understand the human identities that provisioning and using them. Permiso tracks the entire lifecycle of credentials, their privileges and posture, as well as all of the sessions those credentials were used in and by what identity. We even provide impact and suspicion scores for all of their behavior along the way for all of your environments in the cloud and on-prem.
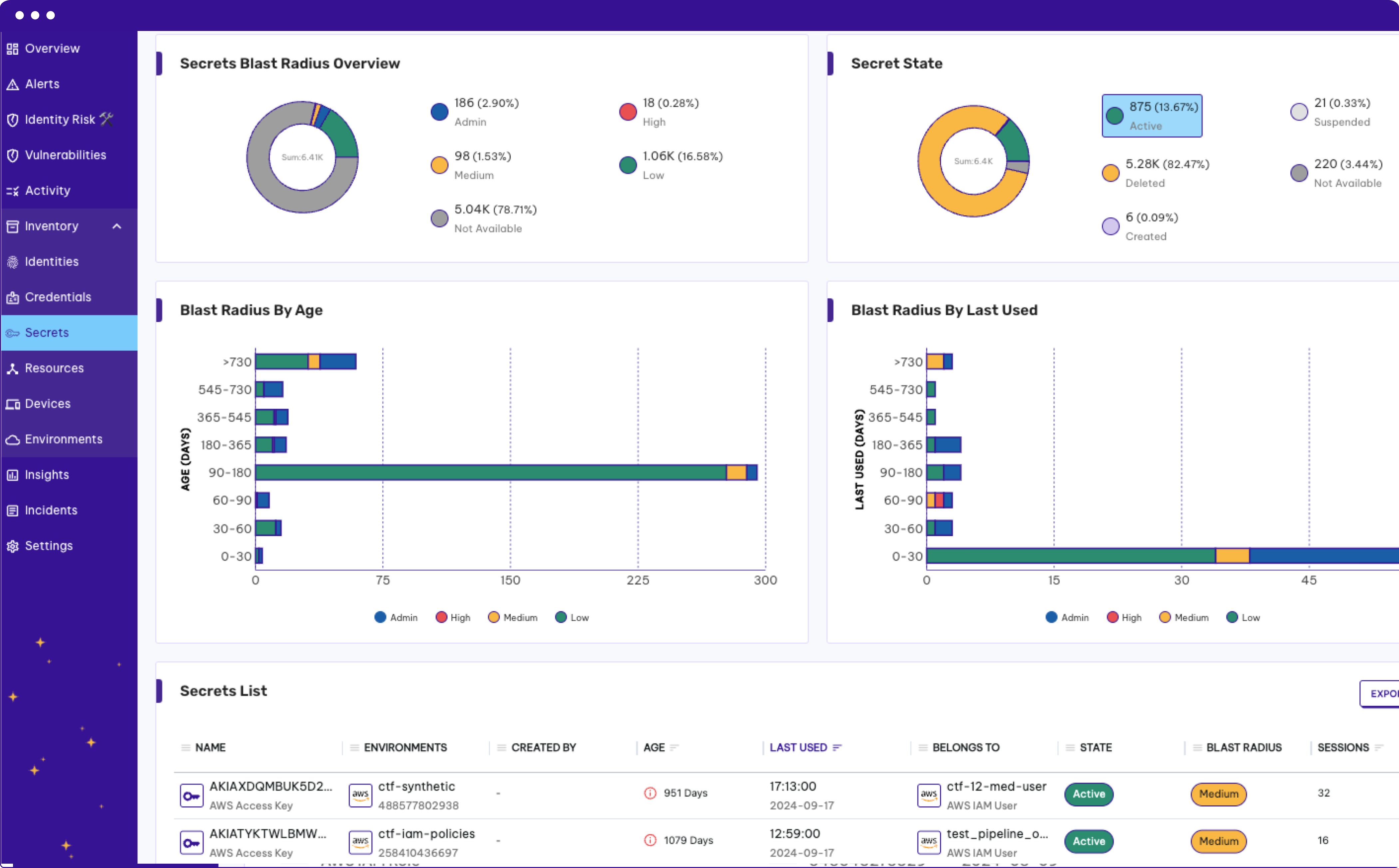
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?




.png)