Identity Security Posture Management (ISPM)
.jpg)
Table of Contents
- Introduction to Identity Security Posture Management (ISPM)
- Core Components of ISPM
- ISPM Architecture and Technical Implementation
- Identity Lifecycle Management (ILM) within ISPM
- Privileged Access Management (PAM) in ISPM
- Identity Governance and Administration (IGA) and ISPM
- Securing Machine and Non-Human Identities
- ISPM in Distributed Cloud Environments
- ISPM and Zero Trust Architecture
- ISPM Implementation Strategies and Roadmap
- Conclusion
- Glossary of Terms
- Frequently Asked Questions (FAQs)
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Section 1
Introduction to Identity Security Posture Management (ISPM)
In today's digital-first landscape, identity has become the new security perimeter. As cyber threats grow increasingly sophisticated, traditional security measures fall short, leaving organizations vulnerable to attacks that exploit identity vulnerabilities. Enter Identity Security Posture Management (ISPM) – a paradigm shift in cybersecurity that transforms how organizations protect their most valuable asset: digital identities and the data that these identities touch.
By implementing ISPM, organizations can:
- Significantly reduce the risk of costly data breaches and insider threats
- Enhance operational efficiency through automated identity management
- Ensure compliance with evolving regulatory requirements
- Enable secure digital transformation initiatives
In an era where identity is the cornerstone of security, ISPM provides the vigilance and adaptability needed to navigate the complexities of the digital world.
Section 2
Core Components of ISPM
Identity Security Posture Management (ISPM) is built on a foundation of interconnected components that work in concert to create a dynamic, responsive system that continuously adapts to emerging threats and evolving business needs.

Identity Inventory
Having solid identity inventory is the cornerstone of ISPM. This catalog should encompass all human and non-human identities – from user accounts, API keys to service accounts. Continuously updated, it provides real-time visibility into access rights across the organization, crucial for identifying security gaps and ensuring policy compliance.
Risk Assessment
Each identity's risk profile should be continuously evaluated using machine learning, considering access levels, behavior patterns, and resource sensitivity. This risk-based approach enables security teams to prioritize high-risk entities, focusing efforts where they matter most.
Policy Framework
At ISPM's core lies a dynamic policy engine, defining and enforcing access rules. It supports fine-grained policies aligned with the principle of least privilege, often incorporating advanced concepts like attribute-based access control (ABAC) for context-aware enforcement.
Continuous Monitoring
Real-time surveillance of identity activities across the organization is vital. By tracking authentication attempts, access patterns, and privilege usage, ISPM establishes behavioral baselines and swiftly flags deviations, enabling rapid threat detection and response.
Automated Response
To counter the speed of modern cyber threats, ISPM leverages automated response mechanisms. These systems can immediately step up authentication, revoke access, or isolate compromised accounts based on predefined policies, significantly reducing threat mitigation time.
Compliance Mapping
ISPM streamlines regulatory compliance by automatically aligning identity practices with relevant standards. It generates audit-ready reports, transforming compliance from periodic scrambles into a continuous, manageable process.
Posture Baseline
ISPM establishes and maintains a "known good" state for identity configurations and permissions. This baseline serves as a reference point, against which current states are continuously compared. Any unauthorized changes or "drift" from this baseline are immediately flagged, enabling proactive maintenance of the organization's identity security posture.
Section 3
ISPM Architecture and Technical Implementation
The effectiveness of ISPM hinges on a robust, scalable, and secure technical architecture. From data collection to analytics and deployment, each element plays a crucial role in creating a comprehensive identity security solution. ecosystems:
Data Collection and Integration
At the foundation of ISPM lies a sophisticated data collection infrastructure. This distributed architecture deploys specialized connectors and agents across various systems, including:
- On-premises directories
- Cloud platforms and SaaS applications
- Security tools and applications
These connectors utilize a combination of methods to gather identity-related data
- API calls for modern, integration-friendly systems
- Log parsing for systems with limited API capabilities
- Direct database queries for legacy systems
The challenge lies in integrating this diverse data without impacting system performance. ISPM platforms address this through:
- Custom connectors for legacy systems
- Data transformation layers to normalize heterogeneous data
- Federation technologies to access identity information from original sources
The Analytics Engine
The analytics engine forms the core of ISPM, processing vast amounts of identity data in real-time. Its multi-tiered architecture typically consists of:
- Data Ingestion Layer: Handles initial processing and normalization of incoming data
- Storage Layer: Leverages big data technologies for efficient data management
- Analytics Layer: Employs both rule-based and machine learning algorithms for:
- Real-time anomaly detection
- Trend-based analyses
- Predictive modeling of potential security risks
Scalability and Performance Optimization
To handle growing data volumes and user bases, ISPM architectures are designed for horizontal scalability:
- Microservices-based components allow for independent scaling
- Distributed processing frameworks (e.g., Apache Kafka, Spark) manage large-scale data streams
Performance optimization techniques include:
- In-memory processing for frequently accessed data
- Intelligent caching mechanisms
- Optimized query processing for large-scale identity repositories
These measures ensure real-time capabilities without impacting business operations.
Security Measures
Given the sensitive nature of identity data, robust security measures are paramount:
- End-to-end encryption for data in transit and at rest
- Strong access controls for the ISPM platform itself
- Comprehensive audit logging of all system activities
- Hardware Security Modules (HSMs) for secure key management
Deployment Models
ISPM solutions offer flexible deployment options to suit various organizational needs:
- On-premises deployment for maximum control
- Cloud-based solutions for scalability and ease of management
- Hybrid models combining both approaches
Each model requires careful consideration of:
- Data residency requirements
- Latency considerations
- Integration complexities with existing systems
Implementation Challenges and Best Practices
Implementing ISPM comes with its own set of challenges:
- Integration with legacy systems lacking modern APIs
- Ensuring data quality and consistency across diverse sources
- Balancing real-time processing with in-depth analytics
Best practices for successful implementation include:
- Phased rollout approach, starting with critical systems
- Continuous monitoring and tuning of the ISPM system
- Regular security assessments and penetration testing
- Ongoing training and awareness programs for IT staff and end-users
By carefully considering these architectural components and implementation strategies, organizations can build a robust ISPM system that provides comprehensive identity security across their entire IT ecosystem. This blueprint for security not only protects against current threats but also lays the foundation for adapting to future challenges in the ever-evolving cybersecurity landscape.
Section 4
Identity Lifecycle Management (ILM) within ISPM
Identity Lifecycle Management (ILM) is the cornerstone of effective Identity Security Posture Management (ISPM). It ensures the secure and efficient handling of identities from creation to retirement, significantly reducing the risk of unauthorized access and potential security breaches.
Key phases include:
Onboarding and Provisioning
The identity lifecycle begins with onboarding, whether for human users during hiring or role changes, or for non-human entities like service accounts and IoT devices during system deployment. ISPM automates this process, ensuring:
- Appropriate access rights based on roles
- Adherence to the principle of least privilege
- Consistent application of security policies
Access Review and Certification 
ISPM Regular access reviews are crucial for maintaining a secure posture. ISPM facilitates this by:
- Automating the review process
- Flagging potentially excessive permissions
- Streamlining certification workflows for managers
Role and Entitlement Management
ISPM systems provide structured approaches to managing roles and entitlements:
- Support for Role-Based Access Control (RBAC) models
- Implementation of Attribute-Based Access Control (ABAC) for granular, context-aware access management
- Ensuring consistency in permission assignments across the organization
Offboarding and Deprovisioning
When an identity is no longer needed, prompt and comprehensive deprovisioning is critical. ISPM ensures:
- Immediate revocation of access rights
- Removal of accounts from all systems
- Prevention of unauthorized access through dormant accounts
Human vs. Non-Human Identity Management
While the lifecycle phases are similar, managing human and non-human identities presents unique challenges:
- Human identities: Require frequent updates due to role changes
- Non-human identities: Need stricter monitoring due to often-elevated privileges and longer lifespans
Human identities demand flexible management to accommodate career progression and organizational changes. ISPM systems must integrate seamlessly with HR processes to ensure timely updates and access adjustments.
Non-human identities, often overlooked in traditional IAM, require automated lifecycle management due to their volume and complexity. ISPM addresses this by implementing continuous monitoring and regular access reviews tailored to these often privileged accounts.
Mitigating Risks of Persistent Authentication
ISPM addresses risks associated with long-lived access keys and OAuth tokens through:
- Regular key rotation
- Token expiration policies
- Continuous monitoring of token usage
Implementing these practices helps organizations balance security with user experience. ISPM automates key rotation processes, ensuring minimal disruption to services while maintaining robust security.
Token policies are dynamically adjusted based on risk assessments, with shorter lifespans for high-privilege access. Continuous monitoring enables ISPM to detect and respond to anomalous token usage, providing an additional layer of security against potential breaches.
By integrating these ILM practices, ISPM creates a robust framework for managing identities throughout their lifecycle. This comprehensive approach not only enhances security but also improves operational efficiency, ensuring that the right identities have the right access at the right time, and only for as long as necessary.
Section 5
Privileged Access Management (PAM) in ISPM
Privileged Access Management (PAM) is a critical component of ISPM, focusing on securing the most powerful accounts within an organization. These accounts, if compromised, can lead to catastrophic data breaches or system-wide failures. Key aspects of PAM in ISPM:
Discovery and Inventorying
ISPM employs continuous scanning techniques to identify privileged accounts across diverse IT environments. This process uncovers not just obvious admin accounts, but also hidden privileges in applications and systems. The result is a dynamic inventory that updates in real-time, ensuring no privileged account escapes scrutiny.
Credential Management
- Vaulting: Secure storage of privileged credentials in encrypted vaults, accessible only through stringent authentication methods.
- Rotation: Automated changing of passwords at regular intervals or after each use, significantly reducing the risk of credential theft or misuse.
Just-in-Time (JIT) Access
ISPM implements JIT protocols, granting privileged access only when needed and for a limited duration. This approach minimizes the attack surface by ensuring privileged accounts are not always active. JIT access typically involves:
- On-demand privilege elevation
- Time-bound access grants
- Automated de-provisioning post-task completion
Session Monitoring
ISPM platforms provide robust session monitoring capabilities for privileged accounts. This includes:
- Real-time activity logging
- Video-like recording of sessions
- Keystroke logging for forensic analysis
These features not only deter malicious activities but also provide crucial audit trails for compliance and incident response.
Cloud-Specific Strategies
Managing privileged access in cloud environments presents unique challenges. ISPM addresses these through:
- Integration with cloud-native IAM tools
- Federated identity management for consistent policies across multi-cloud setups
- Automated discovery of new cloud resources and associated privileged accounts
- Adaptive policies that account for the dynamic nature of cloud environments
By integrating these PAM capabilities, ISPM provides a comprehensive approach to managing the most critical access points in an organization's IT infrastructure. This not only bolsters security but also streamlines operations and ensures compliance with various regulatory standards.

Section 6
Identity Governance and Administration (IGA) and ISPM
As organizations navigate the complexities of digital transformation, they face a critical challenge: how to govern identities effectively in dynamic, hybrid environments. Traditional approaches to Identity Governance and Administration (IGA) often fall short, leaving businesses vulnerable to risks and compliance issues.
When combined with ISPM, IGA becomes more than just a set of policies—it turns into a powerful tool for aligning identity management with an organization's security goals and risk management practices.
ISPM enhances IGA through several key mechanisms:
Separation of Duties (SoD)
As a cornerstone of effective IGA, SoD prevents any single identity from having excessive privileges. ISPM platforms elevate SoD implementation through sophisticated engines that analyze complex role combinations across disparate systems. These engines provide real-time conflict detection and resolution, offering intelligent role adjustment suggestions that balance security with operational efficiency.
Context-Aware Access Management
ISPM-driven IGA leverages contextual information to enhance access request and approval processes. By integrating with business systems, it considers factors like project deadlines and client needs. This approach enables risk-based approval workflows that expedite low-risk requests while scrutinizing high-risk ones. Adaptive policies adjust to changing market conditions and organizational priorities, ensuring agile yet secure access management.
Continuous Compliance Monitoring (CCM)
Maintaining compliance in dynamic environments poses significant challenges. ISPM addresses this through Continuous Controls Monitoring (CCM), which provides real-time evaluation of identity-related controls. This proactive approach enables predictive compliance drift detection based on observed patterns and offers recommendations for maintaining compliance posture.
AI-Driven Governance Models
Advanced ISPM solutions are revolutionizing IGA through AI-driven governance. Machine learning algorithms analyze historical access patterns and policy decisions, offering automated policy refinement suggestions based on risk assessments. This intelligent automation of routine governance tasks frees human administrators to focus on strategic decision-making.
By transforming IGA from a set of static rules to an adaptive, intelligence-driven function, ISPM ensures that identity governance remains effective and efficient in the face of rapidly changing IT landscapes and business needs.
Section 7
Securing Machine and Non-Human Identities
The proliferation of machine and non-human identities in modern IT ecosystems presents unique challenges for ISPM. These identities, including service accounts, IoT devices, and application-to-application (A2A) connections, operate at scales and speeds that demand specialized security approaches within ISPM frameworks.
Service Account Management
SPM focuses on minimizing risk of service accounts through dynamic provisioning. Instead of maintaining standing privileges, ISPM implement just-in-time access, granting the minimum necessary permissions for only as long as necessary
Key aspects of machine identity management in ISPM include:
- Automated lifecycle management for service accounts, including creation, modification, and deletion
- Regular credential rotation to reduce the risk of compromised accounts
- Continuous monitoring of machine identity behavior and access patterns
- Integration with endpoint detection and response (EDR) systems for comprehensive security
Application-to-Application (A2A) Authentication
A2A Authentication presents its own set of challenges as applications increasingly need to communicate directly with each other. ISPM addresses this through robust API security measures, including the implementation of OAuth 2.0 and OpenID Connect protocols. These ensure that application identities are properly authenticated and authorized, maintaining the principle of least privilege across complex application ecosystems.
Device and IoT Security
For device and endpoint identities, particularly in IoT scenarios, ISPM extends security to the network edge through:
- Automated onboarding processes leveraging device attestation mechanisms
- Real-time monitoring of device behavior and access patterns
- Integration with existing security infrastructure for comprehensive threat detection
The unique security challenges of non-human identities stem from their potential for rapid proliferation and often elevated access rights. ISPM addresses these challenges through continuous monitoring and adaptive policies. Machine learning algorithms analyze behavior patterns, quickly identifying anomalies that could indicate compromise or misuse.
By applying these specialized approaches, ISPM ensures comprehensive security for both human and non-human identities, adapting to the unique requirements of each identity type while maintaining a consistent security posture across the organization's entire digital ecosystem.
Section 8
ISPM in Distributed Cloud Environments
Cloud and hybrid infrastructures present unique identity security challenges. ISPM adapts to multi-cloud and hybrid architectures, ensuring consistent identity protection across diverse digital environments.
The Challenge of Distributed Architectures
Implementing ISPM in cloud and hybrid environments addresses the challenges of distributed, dynamic infrastructures. As organizations adopt multi-cloud and hybrid architectures, maintaining a consistent identity security posture becomes critical.
Identity Federation: The Foundation of Cloud ISPM
Identity federation forms the backbone of ISPM in cloud environments. By implementing standards like SAML and OIDC, ISPM enables seamless and secure authentication across multiple cloud providers and on-premises systems. This not only enhances user experience but also centralizes identity control, reducing the risk of inconsistent security policies.
Key Components for Cloud and Hybrid ISPM
ISPM in cloud and hybrid environments relies on several key components:
- Cloud Identity Governance: Extends traditional governance models to accommodate dynamic cloud resources
- Multi-cloud and Hybrid Identity Management: Provides a unified control plane for consistent policy enforcement across environments
- SaaS Application Integration: Utilizes standard protocols and pre-built connectors for rapid onboarding of new SaaS applications
Addressing Policy Consistency Challenges
One of the primary challenges in cloud and hybrid environments is maintaining consistent security policies across diverse infrastructures. ISPM addresses this through a policy abstraction layer, allowing organizations to define high-level security intentions that are automatically translated into environment-specific configurations.
SPM platforms leverage cloud-native APIs and services to extend their reach, ensuring comprehensive coverage without sacrificing the benefits of individual cloud platforms. This approach enables:
- Real-time monitoring of cloud identity permissions across platforms
- Detection and remediation of over-privileged accounts in cloud environments
- Adaptive governance policies that adjust to the ephemeral nature of cloud resources
The ISPM Advantage in Multi-Cloud and Hybrid Environments
By implementing these strategies, ISPM provides a comprehensive approach to identity security in complex, multi-cloud, and hybrid environments. It enables organizations to maintain a strong security posture while leveraging the full benefits of cloud technologies, ensuring that identity remains a consistent and robust security control regardless of where resources are hosted or accessed.
Section 9
ISPM and Zero Trust Architecture
As traditional network boundaries dissolve, Zero Trust has emerged as a critical security model. ISPM and Zero Trust converge to create a resilient, identity-centric security framework for modern enterprises.
The Convergence of ISPM and Zero Trust
The integration of ISPM with Zero Trust Architecture represents a powerful convergence in modern cybersecurity strategies. Zero Trust, based on the principle of "never trust, always verify," aligns seamlessly with ISPM's continuous assessment and risk-based approach to identity security.
At its core, Zero Trust Architecture eliminates the concept of a trusted network perimeter, instead treating every access request as if it originates from an untrusted network. This principle dovetails with ISPM's recognition of identity as the new security perimeter.
Key Components of ISPM in Zero Trust Models
By integrating ISPM into Zero Trust models, organizations can enhance their security posture through several key components:
Dynamic Trust Evaluation
- Leverages ISPM's continuous monitoring and risk assessment capabilities
- Provides real-time data for Zero Trust's dynamic access decisions
- Evaluates each access attempt based on current identity risk scores, behavior patterns, and environmental factors
Contextual Access Control
- Utilizes rich identity context provided by ISPM
- Enables nuanced access decisions in a Zero Trust framework
- Considers factors such as device health, location, and time of access alongside identity risk assessments
Enforcing Zero Trust Principles with ISPM
ISPM plays a crucial role in enforcing core Zero Trust principles:
Least Privilege Enforcement
- Utilizes ISPM's granular policy management and continuous monitoring
- Supports Zero Trust's principle of least privilege
- Dynamically adjusts access rights based on ongoing risk assessments
- Ensures users have only the minimum necessary permissions at any given time
Continuous Authentication and Authorization
- Implements adaptive multi-factor authentication and step-up authentication
- Adjusts verification requirements in real-time as risk levels change
- Maintains a secure state without unduly burdening users
The ISPM Advantage in Zero Trust Environments
By serving as a key enabler of Zero Trust, ISPM helps organizations move beyond static, perimeter-based security models. This integration creates a dynamic, identity-centric security ecosystem that is more resilient to modern threats and adaptable to complex, distributed IT environments.
The synergy between ISPM and Zero Trust allows organizations to:
- Implement more robust and flexible security policies
- Respond rapidly to changing threat landscapes
- Maintain security in increasingly complex and distributed IT environments
Section 10
ISPM Implementation Strategies and Roadmap
Implementing ISMP requires a structured approach tailored to an organization's unique needs and maturity level. This section outlines a comprehensive strategy for ISPM adoption, focusing on three key areas: assessing organizational maturity, phased implementation, and integration with existing security infrastructure.
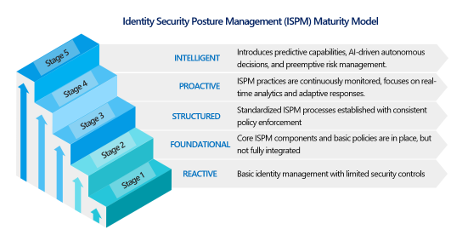
ISPM Maturity Model
The ISPM Maturity Model provides a framework for organizations to assess their current state and plan for future improvements. It consists of five stages:
STAGE 1: REACTIVE
Basic identity management with limited security controls. Identity-related incidents are addressed reactively, with minimal proactive measures.
To advance:
- Conduct identity inventory
- Implement fundamental access controls and basic password policies
- Establish initial governance structures
STAGE 2: FOUNDATIONAL
Core ISPM components and basic policies are in place, but not fully integrated. Basic identity risk assessment tools implemented, lacking real-time monitoring.
To advance:
- Implement continuous monitoring,
- Develop and enforce standardized identity lifecycle management processes
- Integrate ISPM components for a more cohesive security approach
STAGE 3: STRUCTURED
Standardized ISPM processes established with consistent policy enforcement. Automated access controls and continuous monitoring implemented.
To advance:
- Implement advanced analytics for identity risk assessment
- Develop and integrate comprehensive incident response plans
- Begin integration of ISPM data with broader security ecosystems
STAGE 4: PROACTIVE
ISPM practices continuously monitored and improved. Focuses on real-time analytics and adaptive responses.
To advance:
- Implement AI-driven anomaly detection and risk assessment
- Establish predictive risk management capabilities
- Develop fully context-aware access control systems
STAGE 5: INTELLIGENT
Proactive identity security enabled by advanced analytics and automation. AI-driven autonomous decisions and preemptive risk management in place.
To maintain and further improve:
- Continuously refine AI and machine learning models for enhanced prediction
- Implement fully automated, risk-based access control across all systems
- Achieve complete integration of ISPM with the broader security ecosystem
Organizations should use this model to identify their current stage and implement necessary steps for progression.
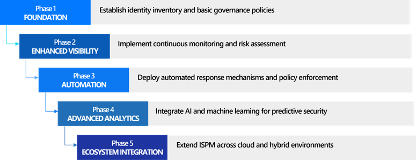
Phased Implementation Approach
A phased approach to ISPM implementation helps manage complexity and demonstrate incremental value. Each phase builds upon the previous one:
PHASE 1: FOUNDATION
- Conduct identity inventory across all systems and environments
- Implement centralized identity management
- Develop initial set of identity governance policies
PHASE 2: ENHANCED VISIBILITY
- Deploy identity analytics tools for real-time visibility
- Establish baseline behavior patterns for all identity types
- Implement initial risk scoring mechanisms
PHASE 3: AUTOMATION
- Implement automated policy enforcement for access requests
- Deploy automated de-provisioning workflows
- Establish automated alert mechanisms for high-risk activities
PHASE 4: ADVANCED ANALYTICS
- Integrate AI and machine learning
- Implement anomaly detection algorithms
- Deploy predictive analytics for proactive risk mitigation
PHASE 5: ECOSYSTEM INTEGRATION
- Implement federated identity management across all environments
- Establish unified policy enforcement across environments
- Integrate ISPM data with other security tools for comprehensive security posture management
Integration with Existing Security Infrastructure
For ISPM to be effective, it must complement and enhance existing security investments. Best practices for integration include:
Mapping ISPM capabilities to current security tools
- Identify gaps and overlaps in functionality
- Ensure comprehensive coverage without redundancy
Leveraging APIs and standard protocols
- Enable seamless data exchange between systems
- Facilitate automated workflows and responses
Aligning ISPM policies with existing frameworks
- Ensure consistency with established standards (e.g., NIST, ISO)
- Streamline compliance efforts across the organization
Integrating with SIEM systems
- Provide context-rich identity data for threat detection
- Enable holistic security monitoring and response
By following this structured approach - assessing maturity, implementing in phases, and integrating with existing systems - organizations can build a resilient ISPM framework that evolves with their security needs and technological landscape.
Section 11
Conclusion
Identity Security Posture Management has emerged as a critical component of modern cybersecurity strategies. It’s comprehensive approach to managing and securing identities across complex digital landscapes provides organizations with powerful tools to enhance their security posture.
The key aspects of ISPM underscore its strategic importance:
- Continuous monitoring and risk assessment of all identities
- Automated response to identity-related threats
- Adaptive policies that evolve with the threat landscape
- Integration with zero trust architectures for enhanced security
As ISPM continues to evolve, its role in cybersecurity is likely to become even more central. By adopting robust ISPM strategies, businesses can navigate the complexities of the digital world with greater confidence, positioning identity as a cornerstone of their security posture and competitive advantage rather than a vulnerability.
Section 12
Glossary of Terms
1. Attribute-Based Access Control (ABAC): Access control model using rules based on attributes of users, resources, actions, and context.
2. Just-in-Time (JIT) Access: Temporary provision of privileged access rights only when needed, automatically revoked after use.
3. Continuous Controls Monitoring (CCM): Automated, real-time assessment of internal control effectiveness, providing real-time insights for risk management and compliance.
4. Identity Federation: Trust framework enabling cross-domain authentication and authorization using a single set of credentials.
5. Zero Trust Architecture: Security model assuming no implicit trust, requiring continuous verification of every user, device, and network connection before granting access to resources.
6. Least Privilege Enforcement: Principle of restricting user account privileges to the minimum permissions necessary for their role, reducing potential security breach impact.
7. Separation of Duties (SoD): Distributing critical tasks among multiple users to prevent fraud, errors, and conflicts of interest in business processes.
8. Adaptive Authentication: Risk-based authentication system adjusting requirements based on contextual factors such as user behavior, device, location, and access patterns.
9. Identity Drift: Gradual, unintended deviation of user access rights from their intended state due to poor lifecycle management or policy enforcement.
10. Credential Vaulting: Secure storage and management of privileged account credentials using encryption and strict access controls



.png)








.png?width=767&name=image%20(9).png)
