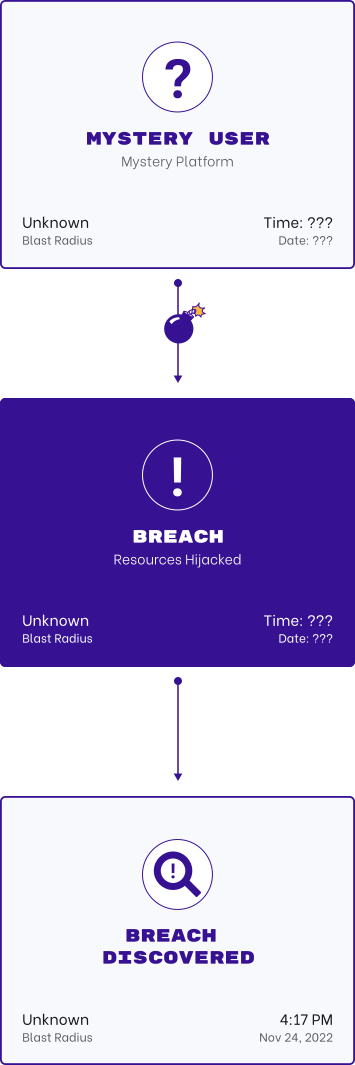
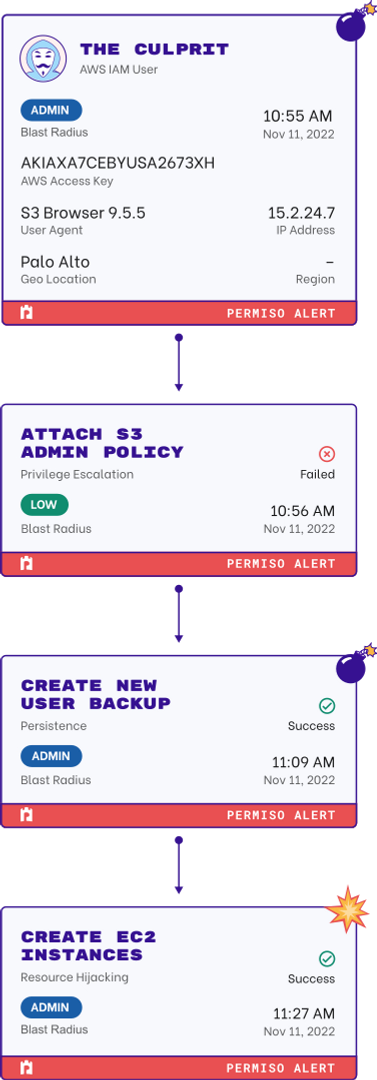
Universal Identity Graph
Permiso's unified identity security platform combines Identity Security Posture Management (ISPM) with Identity Threat Detection and Response (ITDR) to protect all of your human and non-human identities, wherever they go.
Detect identity risk and threats for all of your users in the cloud and on-prem environments to prevent account takeover and reduce identity risk. Employees, guests and vendors - and all of the credentials, access keys, secrets and service accounts they're using.

Identity Security Posture Management
We’ve built the industry’s first universal identity graph to proactively manage all entity identity risk for humans and non-human identities, across all environments, from a single pane of glass.
With Permiso you can:
- Assess your identity attack surface risk
- Remove zombie identities and accounts
- Reduce unnecessary privileges
.png)



Identity Threat Detection and Response
Permiso monitors activity and correlates user behavior across those environments to produce incredibly high-fidelity identity security alerts across AWS, Azure, Okta, M365, and more, significantly improving Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR).
With Permiso you can detect:
- Credential Compromise
- Account Takeover
- Insider Threat
.png)
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?

Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!