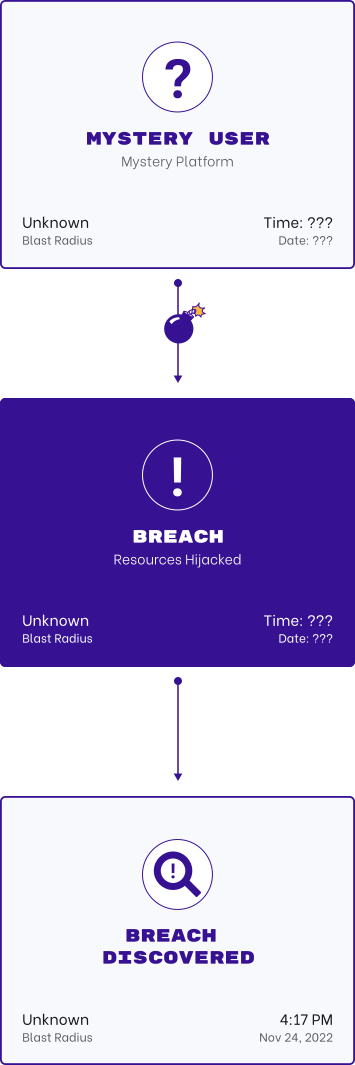
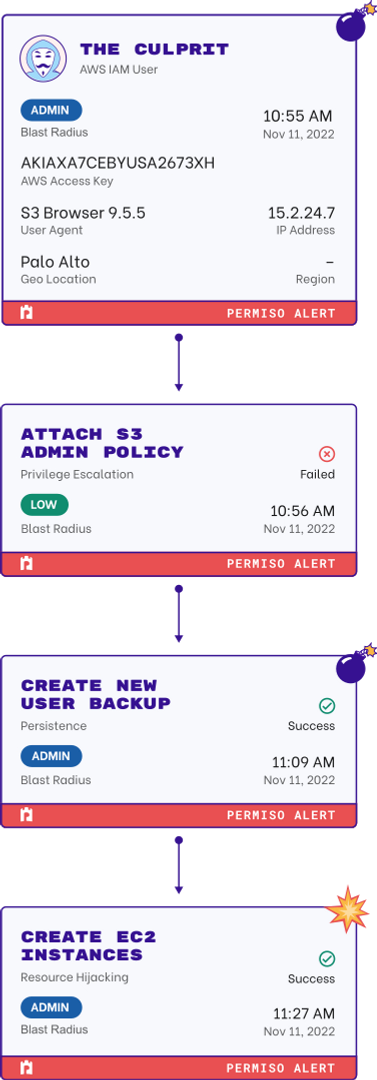
Reduce Excessive Privileges
Achieve least privilege for all users
Employees or guests with excessive privileges or tokens with read and write access permissions connecting into sensitive environments represents a significant threat vector for organizations.

Reducing Privileges Is Hard Work
Staying on top of the privileges for all of the identities across all environments, all the time, is impossible. Siloed tools are not up to the task
%20-%20expanded%20(1).png)



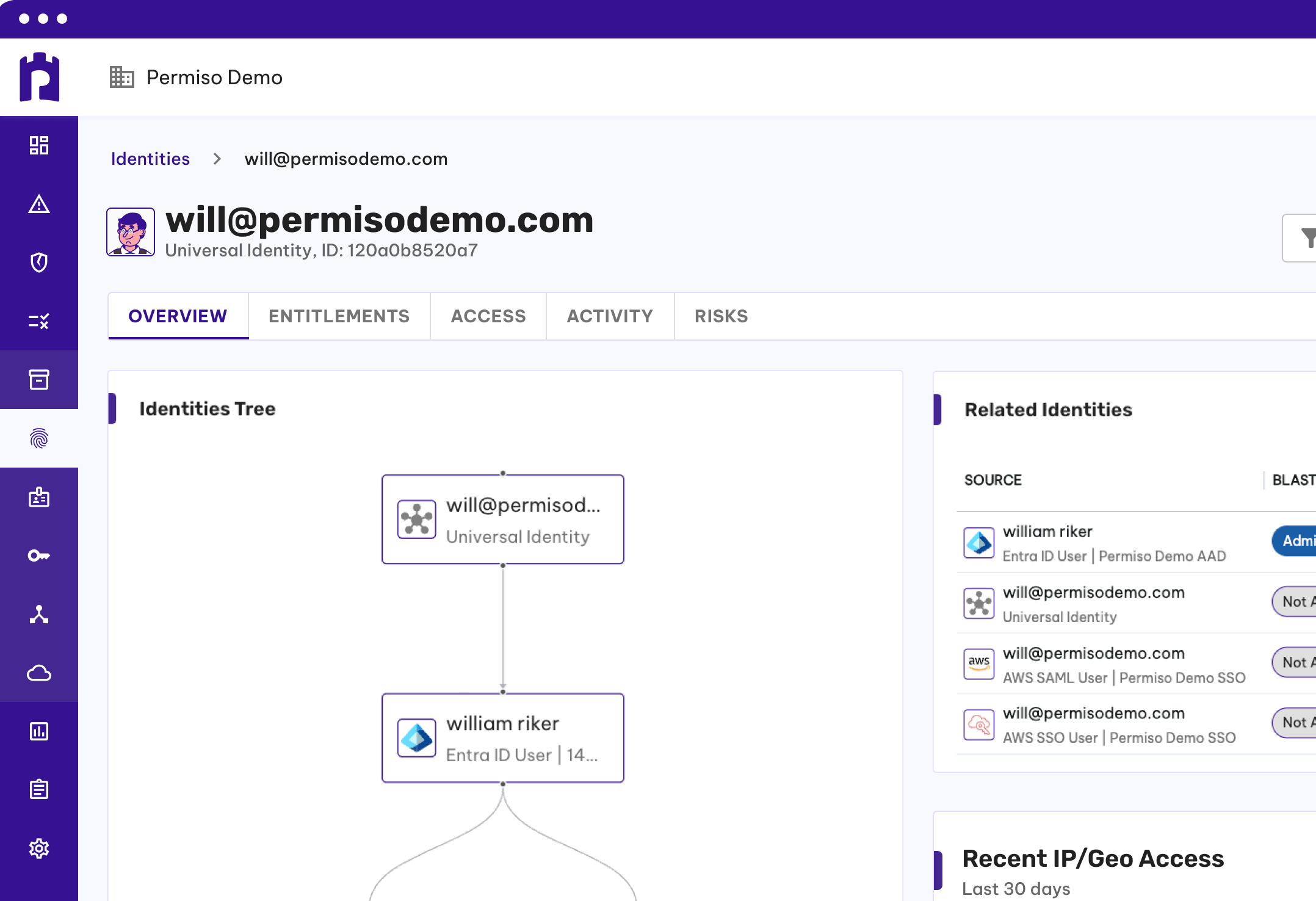
Unified Identity Visibility
Permiso enables you to manage privileges for all identities including human and non-human for all environments from a single pane of glass. It does this by creating a universal identity for all identities and their associated privileges, across all of your environments, enabling you to reduce your attack surface risk.
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?




.png)