Assess Identity Risk
SILOED TOOLS CREATE DANGEROUS BLINDSPOTS
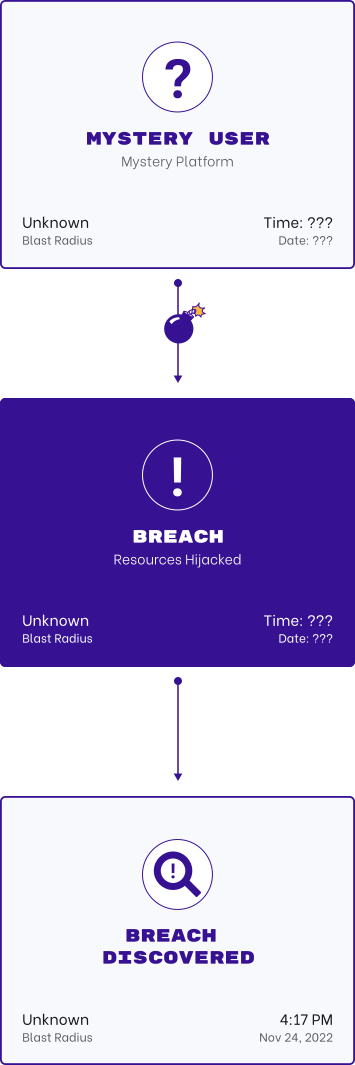
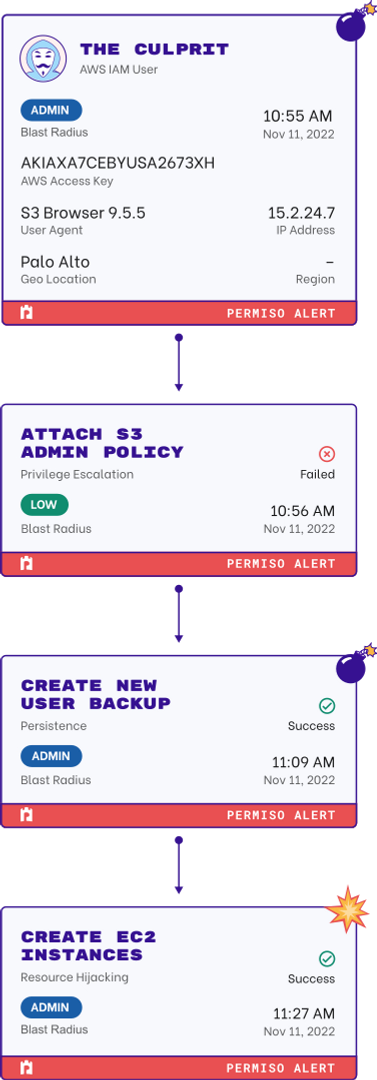
Underestimating the identity attack surface area is the number 1 challenge.
Lack of Risk Visibility
This incomplete visibility creates opportunities for threat actors to go undetected for months or even years at a time.




Universal Identity Risk Visibility
By creating a universal identity comprised of all of your human and non-human identities across all of your environments, Permiso provides unparalleled identity risk visibility and security from a single pane of glass.
-1.png)
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?




.png)