Remove Zombie Identities
Find and zap zombies
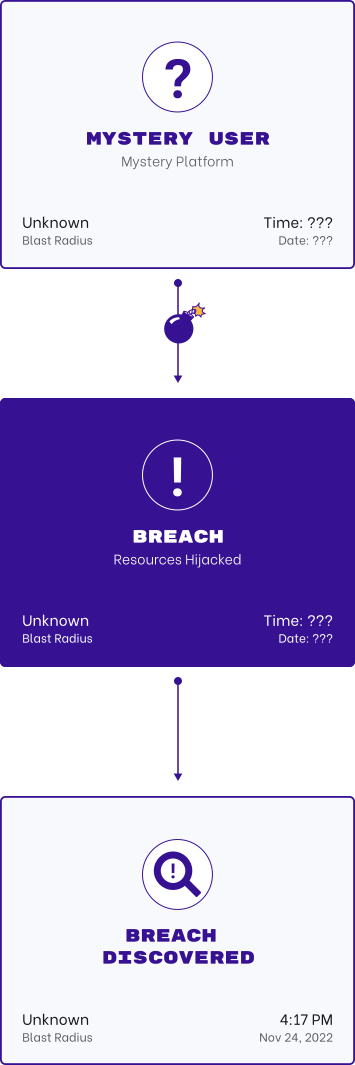
Poor identity hygiene presents opportunities that threat actors can exploit. The most common is not removing zombie accounts. These can be former employees or service accounts.
.png)
Identity Risk Multiplies
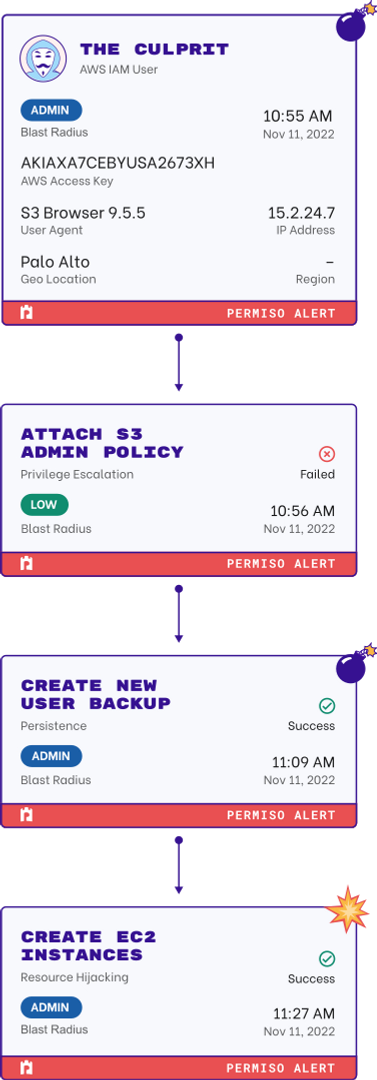
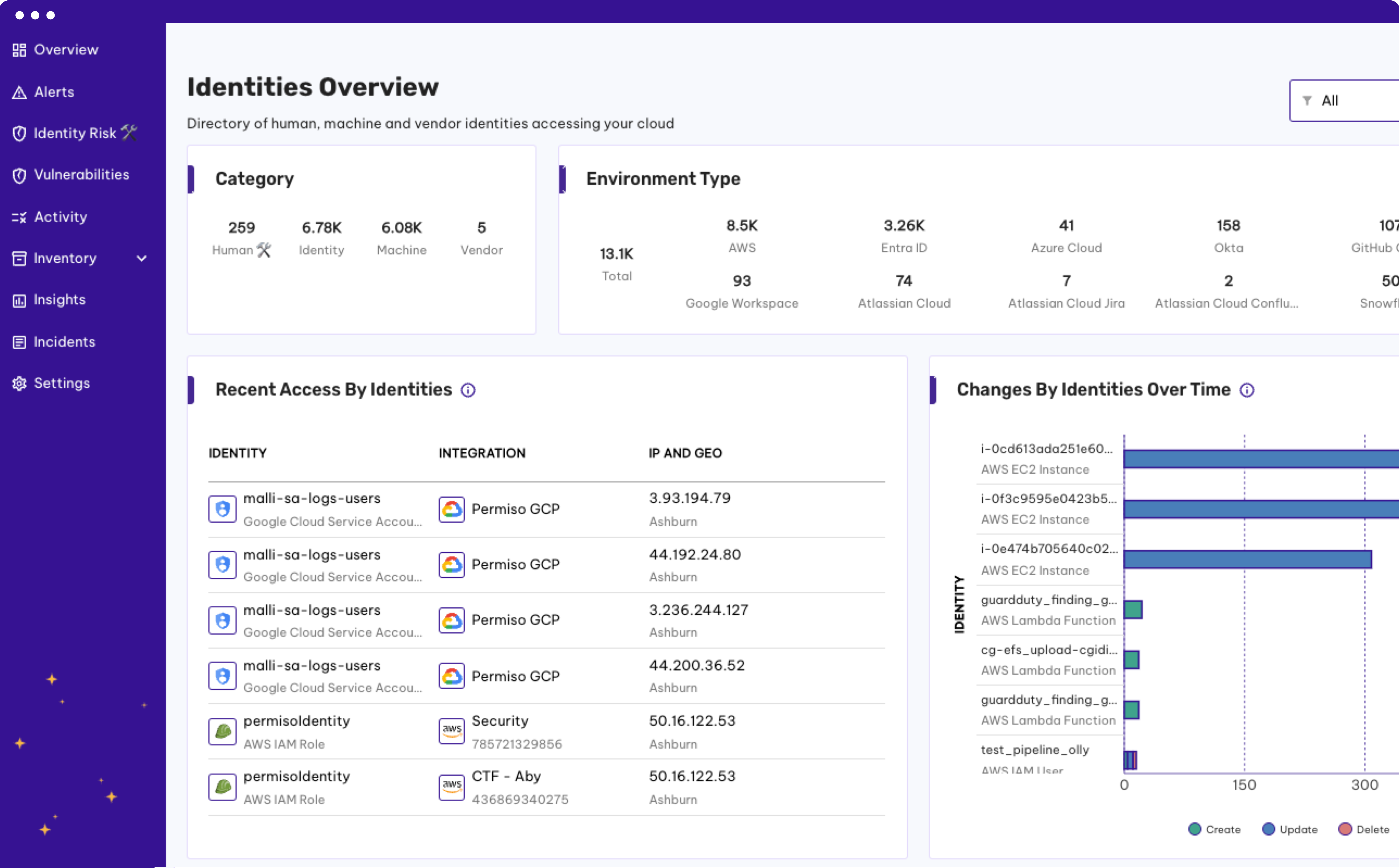
Managing one identity is enough of a challenge, now multiply that by hundreds or thousands of human and non-human identities. And that number only continues to grow!
%20-%20expanded%20(1).png)



Find Them Every Time
By creating a universal identity comprised of all of your human and non-human identities across all of your environments, Permiso enables you to find all zombie identities, significantly improving your identity security posture.
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?




.png)