Introducing Cloud Console Cartographer: An Open-Source Tool To Help Security Teams Easily Understand Log Events Generated by AWS Console Activity
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Introduction
While most cloud CLI tools provide a one-to-one correlation between an API being invoked and a single corresponding API event being generated in cloud log telemetry, browser-based interactive console sessions differ profoundly across cloud providers in ways that obfuscate the original actions taken by the user.
If you’ve spent time digging through cloud logs generated by AWS console sessions, you’ve probably scratched your head quite a few times, trying to distill a long list of log events generated from a single action, such as a click of a button. The noise in these logs not only makes triaging threats difficult, but it makes it very difficult for SOC teams to be able to easily answer the question “What do all of these events mean and what actions did the identity actually take inside of AWS Console?”
In reviewing these logs, you might see events in CloudTrail such as iam:ListMFADevices or iam:ListAccessKeys. This can be confusing, because this user didn’t take any action in the UI to list MFA devices or Access Keys; this user simply clicked on the IAM homepage which triggered these events to populate that information in the console UI. Security professionals are left trying to differentiate API calls specifically invoked by a user from those secondary API invocations that create events to support the behavior or actions being conducted in the console UI. Threat actors have been observed leveraging console and other UIs in a strategic effort knowing how confusing this log data can be to incident responders and blue teamers.
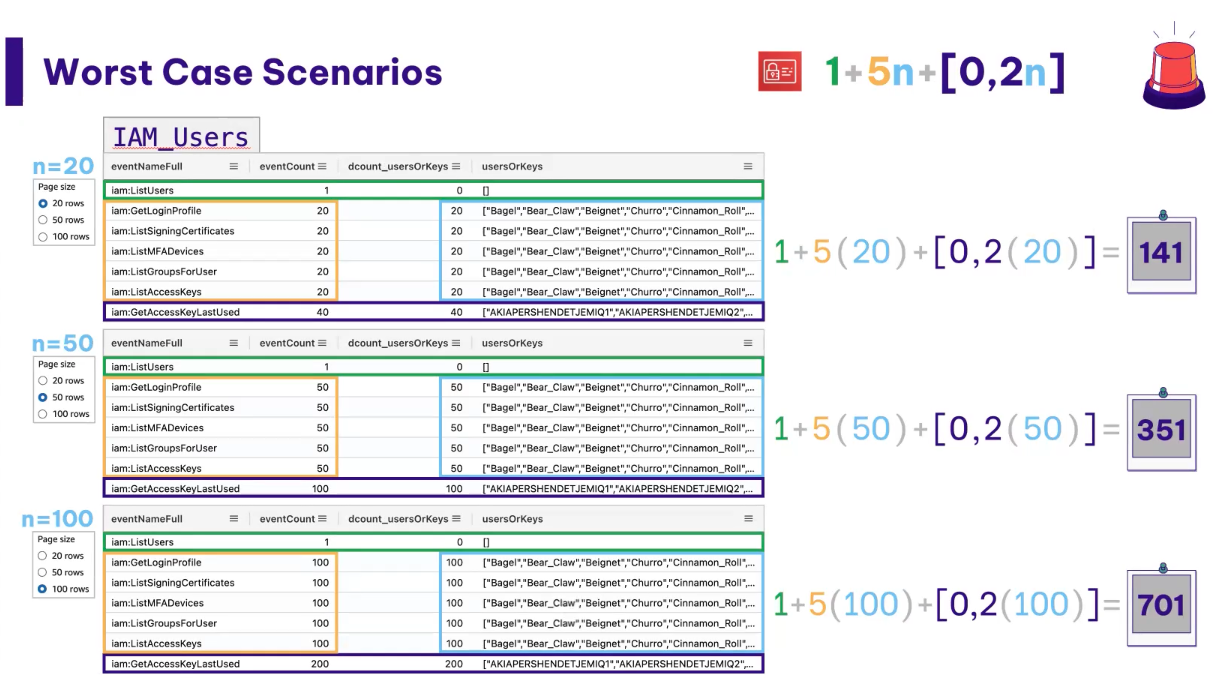
If you click on IAM users in console, and three users are listed, this single click generates 18 events in CloudTrail. If that number increases to 20 users, a total of 141 events will be generated. This number climbs to over 700 events if there are 100 users. A lot of event activity from a single click of a button.
Introducing Cloud Console Cartographer
Cloud Console Cartographer is an open-source tool that is built to help security teams distill the noise of events generated in cloud logs by activity in AWS console. Could Console Cartographer maps the myriad of events generated in cloud logs to a consolidated list of succinct events that quickly tell defenders what actions an identity actually conducted while using AWS’s console UI. While much of cloud infrastructure is spun up as-code today, a lot of activity is still taking place in AWS console. Even today, some features, capabilities or information is only available within the console.
In the example below, a user performs the single action of selecting IAM → Users in the console. That singular click generates nearly 500 CloudTrail events. These events represent what is loading in the user interface of AWS console and what the user is seeing when they screen loads. This could include dashboards, a list of users or keys, etc. From the perspective of someone reviewing these logs, there’s a flood of events that look like a slew of activity being conducted by the user, but isn’t actually reflective of what the user actually did.
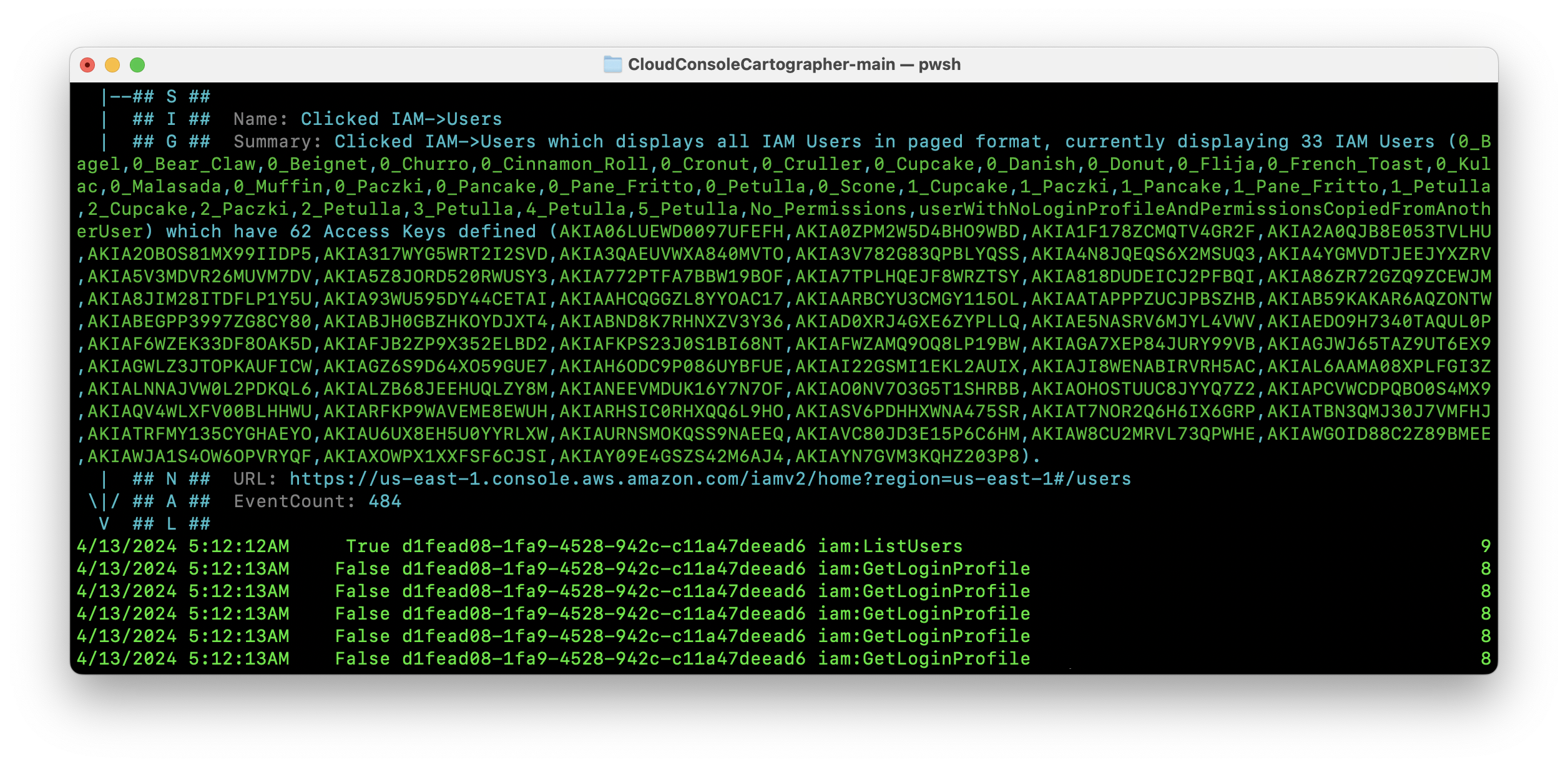
Example # 1 - Running The Tool With Local CloudTrail Logs and Event-Level CLI Summary
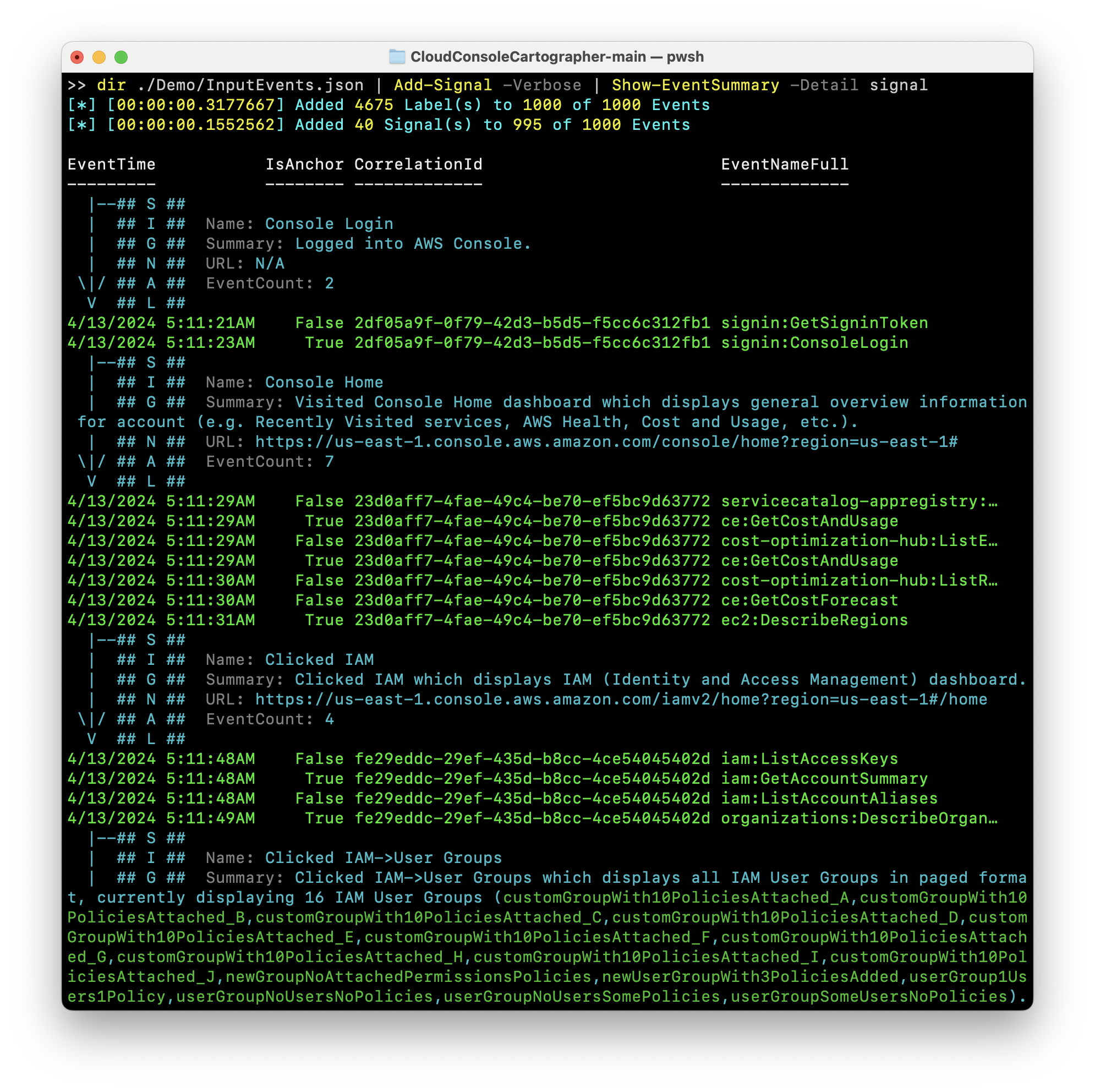
You can use the demo CloudTrail session that is stored in ./Demo to observe how the framework is able to aggregate the log data and provide a succinct explanation summary of the events. In a later example below, we will showcase how logs can be piped into the framework’s functions wtihout requiring anything to be written to disk before calling any of the available aggregation or visualization functions. .
First, you will need to invoke Add-Signal to apply Labels and perform the Signal mapping evaluation. Second, pass these results to one of the multiple output functions.
dir ./Demo/InputEvents.json | Add-Signal -Verbose | Show-EventSummary -Detail signal
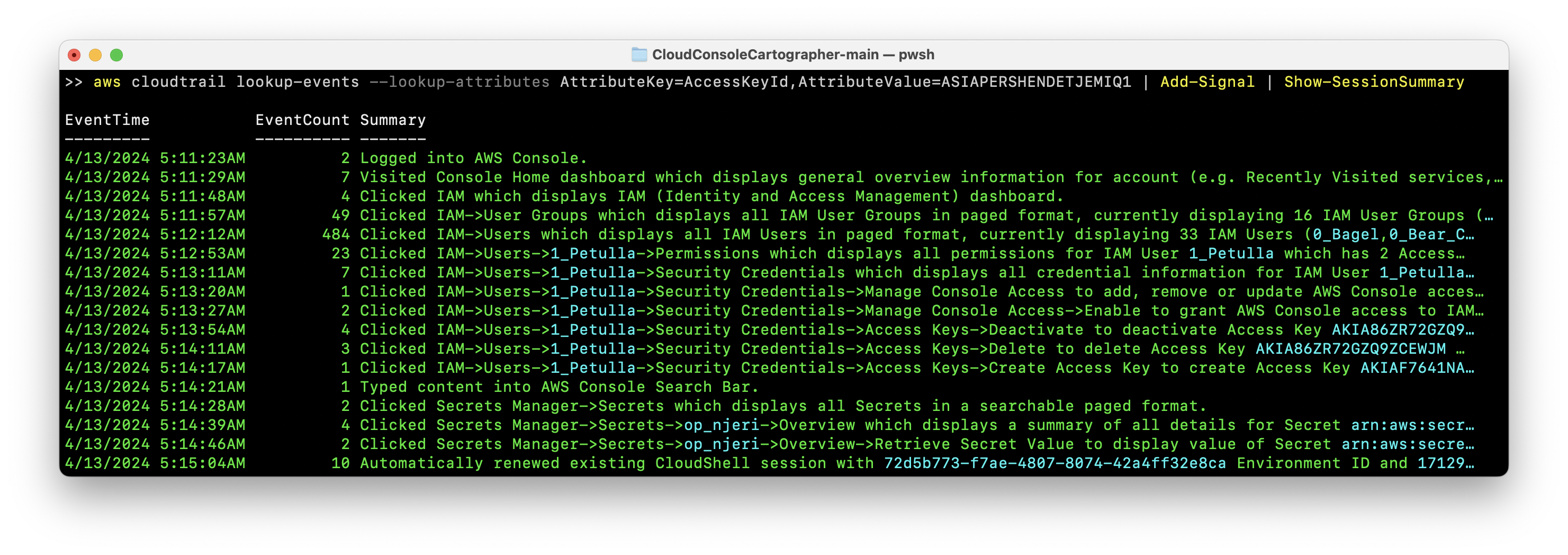
Example #2 - Running the tool with CloudTrail logs queried directly from CloudTrail API and session-level CLI Summary
aws cloudtrail lookup-events —lookup-attributes AttributeKey=AccessKeyID, AttributeValue=ASIAPERSHENDETJEMIQ1 | Add-Signal | Show-SessionSummary
Example #3 - Using Python-based UI Visualizer
cat ./Demo/InputEvents.json | Add-Signal | Show-SessionSummary UI
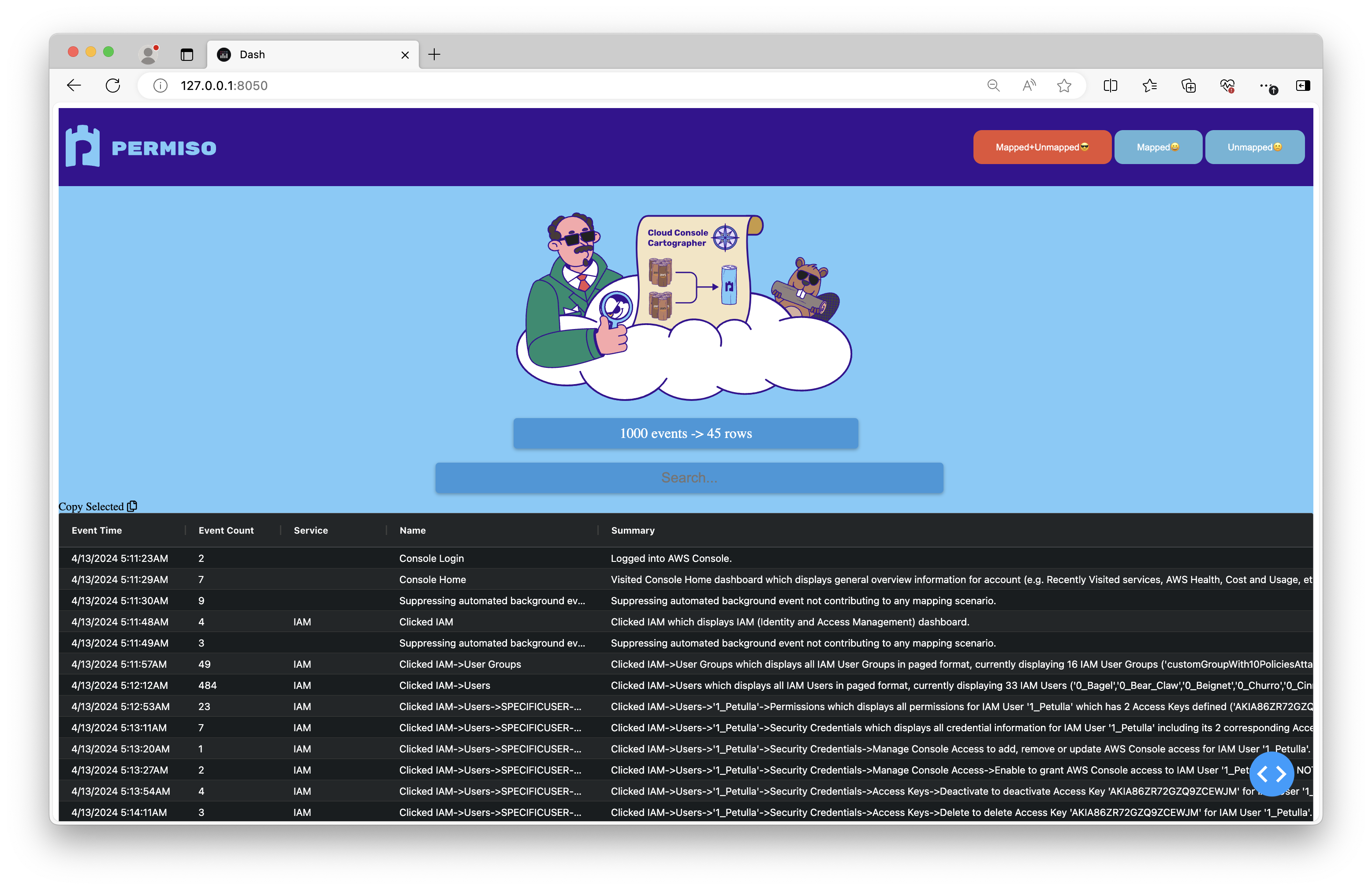
We’re here to help security teams reduce the time they spend trying to put pieces together to make sense of noisy events in cloud logs. You can access Cloud Console Cartographer on GitHub: https://github.com/Permiso-io-tools/CloudConsoleCartographer



.png)





.png?width=767&name=image%20(9).png)



