
How to Choose the Best ITDR Solution for Your Organization

Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
The best ITDR solution for your organization depends on measurable criteria rather than vendor claims: Can it track identities across authentication boundaries from your IdP through cloud infrastructure to SaaS applications? Does it generate high-fidelity alerts that your team actually investigates, or does it add to alert fatigue? Can it attribute activity when multiple users share service accounts? Does it draw on real-world threat intelligence or theoretical attack models? The vendor landscape ranges from established IAM providers adding detection capabilities to purpose-built platforms designed specifically for identity threat response, and choosing wrong means continuing to miss the attack technique behind the majority of successful breaches.
Understanding What ITDR Actually Does
Before evaluating solutions, get clear on what you're buying. ITDR is not the same as Identity and Access Management (IAM), Identity Governance and Administration (IGA), or Cloud Infrastructure Entitlement Management (CIEM). Those tools manage identities and permissions. ITDR assumes attackers will bypass those controls and focuses on detecting when they do.
Effective ITDR monitors identity behavior across your entire environment to spot the signs of compromise: credential misuse, privilege escalation, lateral movement, abnormal access patterns. It answers the question every security team dreads at 2 AM: "Is this legitimate activity or are we being breached?"
The challenge is that identity-based attacks look like normal behavior. An attacker using stolen credentials logs into AWS the same way a legitimate administrator does. The detection happens by understanding context: this person never accesses these resources, they're logging in from an unusual location, their behavior pattern has changed, they're moving laterally in ways that don't match their role.
Critical Capabilities for Effective ITDR
Detection Coverage Across All Environments
Your identities don't stay in one place. An employee authenticates through Okta, accesses AWS infrastructure, uses SaaS applications like Salesforce and Slack, and commits code to GitHub. An attacker who compromises their credentials follows the same path. If your ITDR solution only monitors one layer of this stack, you have a massive blind spot.
The best ITDR solutions track identities across authentication boundaries. They monitor your identity provider (IdP), cloud infrastructure (IaaS), platform services (PaaS), and SaaS applications in a unified view. When evaluating solutions, ask specifically which environments they cover. Be suspicious of vendors who excel at one layer but hand-wave about the others. Integration lists are not enough. You need to see how the solution correlates activity across different platforms to build complete user sessions.
High-Fidelity Detection, Not Just More Alerts
Security teams are drowning in alerts. The average SOC receives thousands of alerts daily, most of them noise. Adding another tool that generates atomic event alerts based on individual suspicious actions (login from new location, MFA reset, permission change) makes the problem worse, not better.
The best ITDR solutions use session-based detection instead of event-based detection. They construct complete user sessions from disparate events across multiple systems, providing context that separates actual threats from benign anomalies. A login from a new country might be suspicious in isolation but perfectly normal when you know the user is traveling for a scheduled business trip, their other behavior is consistent, and they're accessing expected resources.
Look for solutions that explicitly describe how they reduce false positives. Ask for specific metrics: what percentage of their alerts require action versus investigation and dismissal? How do they correlate events into sessions?
Identity Attribution, Even with Shared Credentials
Service accounts and API keys create attribution nightmares. Multiple developers share the same AWS access key. A CI/CD pipeline uses a service account that performs thousands of operations daily. When something goes wrong with these shared credentials, traditional tools can't tell you who actually did what.
Advanced ITDR solutions use behavioral analysis and contextual signals to attribute activity even when credentials are shared. They track patterns like time of day, resources accessed, API call sequences, and operational cadence to fingerprint different users of shared accounts. This capability is essential because non-human identities (service accounts, API keys, secrets) now outnumber human identities in most organizations by 10:1 or more.
Depth of Detection Rules and Threat Intelligence
Some ITDR vendors offer dozens of detection rules. Others offer hundreds or thousands. Numbers matter, but so does source. The best detection rules come from responding to actual breaches, not theoretical threat models.
Look for vendors whose threat research teams actively respond to incidents and publish their findings. Ask how many detection rules they have, but also ask where those rules came from. Were they developed by researchers who track real threat actors and analyze actual attack campaigns? A vendor with deep threat intelligence will be able to tell you specific stories: we saw this attack technique used by this threat group, here's how we detected it, here's the rule we built that now protects all our customers.
Integration-First Architecture
Your ITDR solution needs to work with your existing security stack, not replace it. The best solutions integrate seamlessly with SIEMs, SOAR platforms, ticketing systems, and communication tools. They feed high-fidelity alerts into your existing workflows rather than creating yet another console your team has to monitor.
Evaluate the quality of integrations, not just quantity. Some vendors claim hundreds of integrations but provide only basic API connections that require custom development. Look for native integrations that work out of the box, with clear documentation and customer references who actually use them.
Deployment Speed and Operational Overhead
Security teams are understaffed. You don't have time to spend months deploying and tuning a new platform. The best ITDR solutions use agentless architectures that connect to your existing logs and APIs with read-only access. They start providing value within days or weeks, not months.
Be wary of solutions that require agents on every endpoint, complex log forwarding configurations, or extensive professional services engagements before you see any detection capability.
Posture and Runtime Together
Identity threats have two dimensions: misconfigurations that create risk (posture) and active attacks exploiting those risks (runtime). The best ITDR solutions address both. They show you which identities have excessive permissions, stale access, or toxic privilege combinations (posture) and monitor those high-risk identities for suspicious behavior (runtime).
Vendors who only do runtime detection miss the opportunity to prevent attacks by fixing misconfigurations before they're exploited. Vendors who only do posture management can't detect when prevention fails and attackers are active in your environment.
Why Permiso Ranks Among the Best ITDR Solutions
Permiso operates as a unified identity security platform that combines Identity Security Posture Management (ISPM) with Identity Threat Detection and Response (ITDR) to protect human, non-human, and AI identities across cloud and on-premise environments. Rather than retrofitting identity detection onto an existing security product, Permiso was purpose-built to track identities across authentication boundaries and detect the lateral movement techniques that traditional tools miss.
Comprehensive Cross-Boundary Coverage
Permiso monitors identity providers, cloud infrastructure (AWS, Azure, GCP), SaaS applications, and on-premise environments in a unified platform. Their Universal Identity Graph tracks identities wherever they go, correlating activity across authentication boundaries to build complete user sessions. When an attacker compromises credentials and moves from Okta to AWS to Slack, Permiso follows them every step of the way.

1,500+ Detection Rules Built from Real Breaches
The P0 Labs threat research team, composed of former Mandiant Advanced Practices leads, has developed over 1,500 detection signals based on responding to actual attacks. These aren't theoretical rules. They come from tracking threat groups like Scattered Spider (LUCR-3), analyzing their techniques, and building detections that catch those techniques wherever they appear. The team continuously monitors active incidents and updates detection rules based on emerging threats.
Session-Based Detection for High Fidelity
Instead of generating alerts on individual suspicious events, Permiso constructs complete user sessions from runtime activity across all monitored environments. This context-driven approach dramatically reduces false positives. Customers report that Permiso alerts "bring attention to the things that truly matter" compared to the flood of noise from other tools.
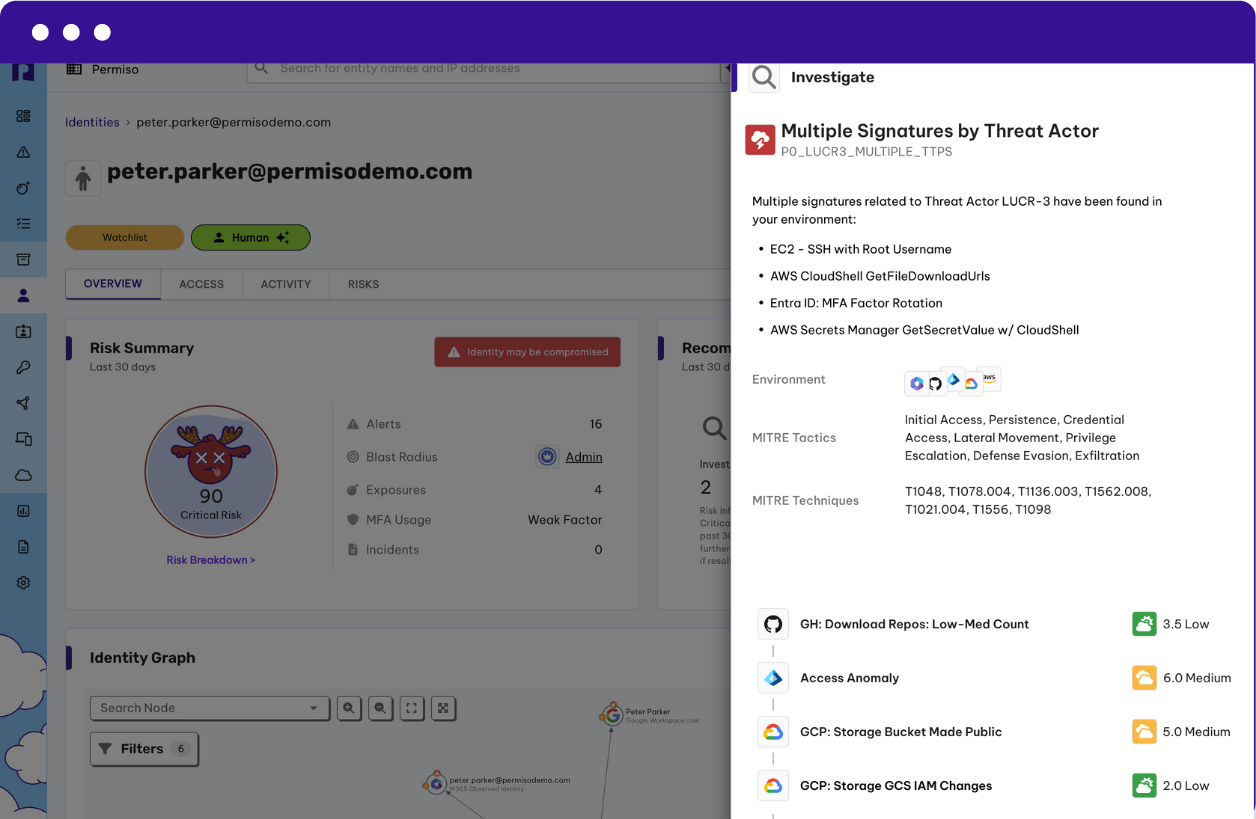
Advanced Identity Attribution
Permiso handles non-human identities as first-class citizens, with specific capabilities for service accounts, API keys, and secrets. The platform can attribute activity even when credentials are shared, using behavioral patterns and contextual signals to identify which user took specific actions.
Unified Posture and Runtime
Permiso combines Identity Security Posture Management (ISPM) with ITDR in a single platform. It identifies high-risk identities with excessive permissions, stale access, or toxic combinations (posture) and monitors those identities for suspicious behavior (runtime). This unified approach eliminates the blind spots created by using separate tools for posture and threat detection.
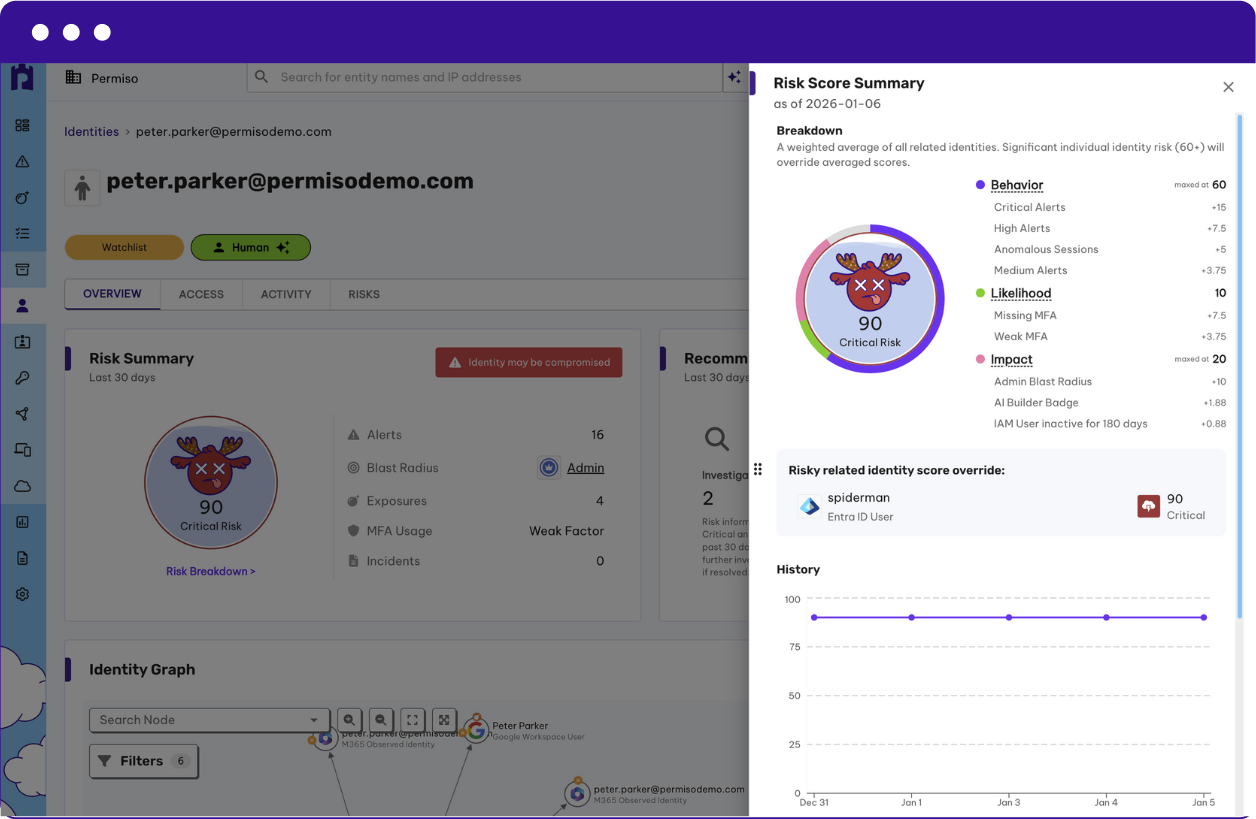
Agentless Deployment with Immediate Value
Permiso connects to existing logs and APIs with read-only access. No agents to deploy, no complex infrastructure changes. Customers typically see value within days or weeks, not months.
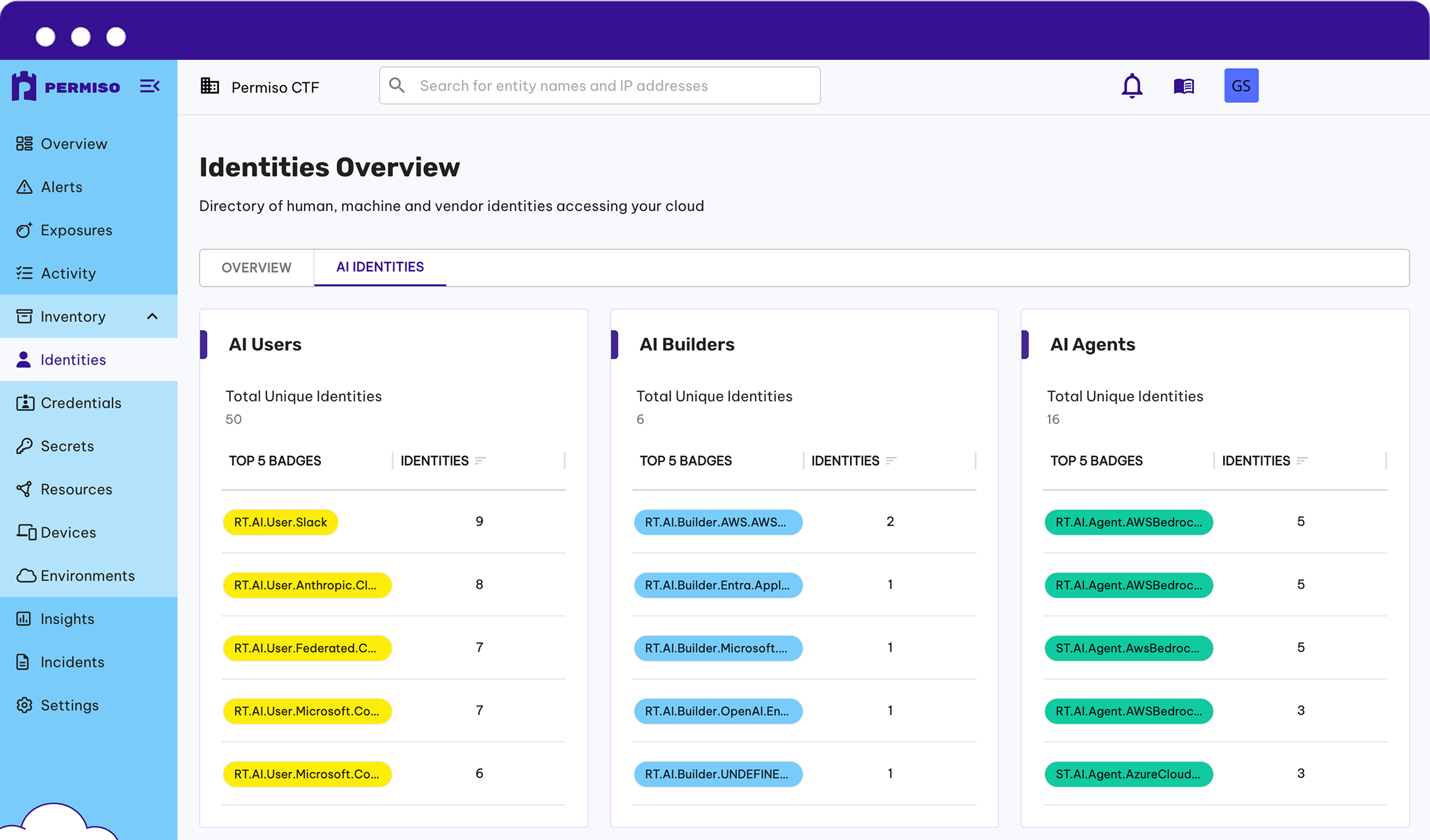
AI Identity Security Built In
As organizations adopt AI, they're creating new identity risks with AI users, AI builders, and autonomous AI agents. Permiso extends its identity security framework to cover these AI identities, providing the same comprehensive protection for AI that it delivers for human and non-human identities.
Independent Recognition
GigaOm's 2025 ITDR Radar Report recognized Permiso as both a Challenger (competing effectively with established players) and a Fast Mover (rapidly expanding capabilities). This independent validation confirms what customers already know: Permiso sets the standard for identity threat detection and response.
The question isn't whether you need ITDR. The question is which solution will actually detect threats in your specific environment rather than adding to your alert fatigue. Permiso was built from the ground up to answer that question, by a team that has spent decades in the trenches responding to the exact attacks you're trying to prevent.



.png)




.png?width=2184&height=270&name=ITDR%20Cheat%20Sheet%20(728x90).png)

%20(1).png?width=767&name=Blog%20Image%20(892%20x%20298)%20(1).png)

.png?width=767&name=Looking%20at%20AI%20Security%20Through%20the%20Identity%20Lens%20(1).png)