
Gather Round the Watering Hole, We have a story to tell

Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Summary
Watering hole attacks are an often underrated technique. On January 29th, 2023 Chris Farris reported to members of the “Cloud Security Forum” slack channel that he saw a google ad delivering a malicious AWS console logon phishing page:
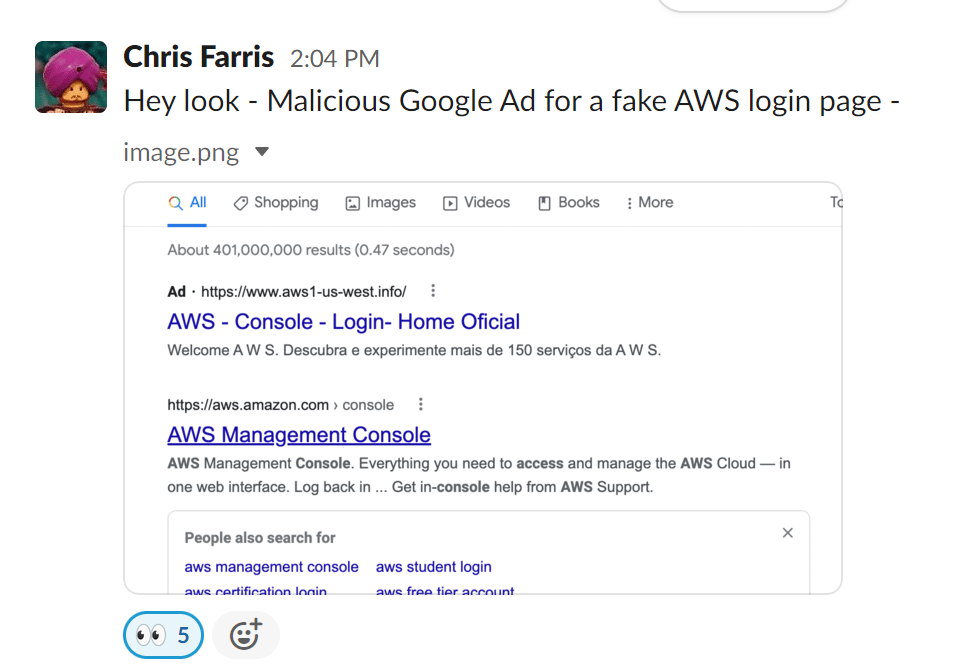
While this is the latest report, there have been others mentioned recently too. The Permiso p0 labs team is always on the lookout for new attacks focused on cloud, and dove in on this.
Attack Flow
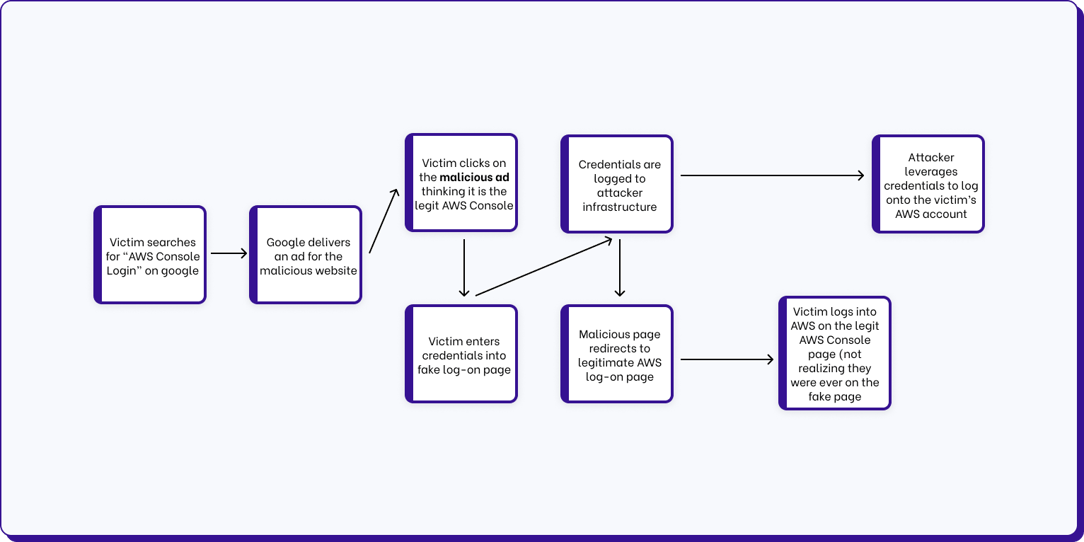
The way this attack works is:
-
The attacker buys ad space for certain search terms in google.
-
The Victim searches for a term like “AWS Console Login” in google. Google returns a list of results that include the malicious Google ad at the top.
-
The Victim clicks on the ad, thinking it is the legitimate AWS Console Login site. The fake site looks exactly like the normal AWS Console Login page, so the victim enters their credentials to logon.
-
These credentials are saved to the attacker infrastructure, and the victim is redirected to the the legitimate AWS Console Logon page.
-
Now at the legitimate AWS Console Logon page, the victim suspects they must have entered their username and password incorrectly, types in again, and now enters the legitimate AWS Console, not realizing they gave their credentials to attackers along the way.
-
The attacker now has the username and password, and assuming the victim doesn’t have MFA enabled they can immediately use the credentials. Also, since often users reuse passwords, they may try to logon to other services with the victims credentials such as their email or VPN.
Attacker Infrastructure
In this attack, the threat actor is using the domain aws1-us-west.info , to masquerade as a legitimate AWS website. The domain was registered on January 24, 2023, last updated on January 29. 2023 and was registered via the registrar SAV.
This domain currently resolves to a Cloudflare IP Address 104.21.39.144. Before the Cloudflare IP Address though, it resolved to its true IP Address, 5.8.33.175 . The true address is hosted in the ASN 202422 (Ghost LU). The system it is hosted on is a Ubuntu 2.17 box running Apache/2.4.41 with PHP on TCP/80. The system also has TCP/22 (SSH) enabled and TCP/25 (STMP) returning a banner of 220 vm6.template ESMTP Postfix (Ubuntu).
The domain and this system were created recently. The domain on January 24, 2023 and the system 5.8.33.175 first had internet exposed services starting on January 26, 2023.
Attacker Files
The attacker appears to be hosting a few campaigns off this one system. For this blog we will focus on the AWS targeting. The image below is what the attacker version of the logon page looks like. This is a direct copy of the legitimate AWS Console site visually. Now obviously this is in Portuguese (Brazilian Portuguese), we will touch more on that in a later section on targeting.
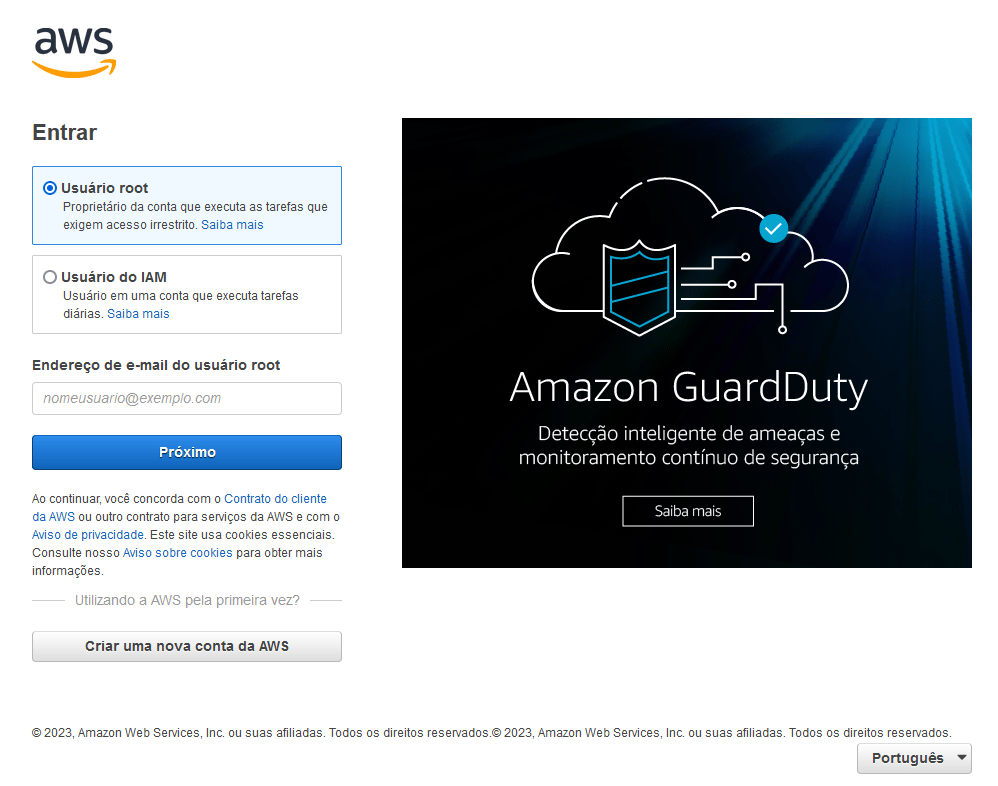
Outside of the copied images and other assets from the legitimate AWS site, the attacker has six (6) main files that are used in the credential stealing attack:
|
File |
MD5 |
SHA1 |
|---|---|---|
|
erro.php |
3b716d9f3e2e772907aae066d4d0f1a8 |
3bb3675499ba5c65f4315ddc382352c1366e87b6 |
|
idconta.html |
338b3177e56cabdf43a6019dd04d2725 |
e128fc62ec9ac913606ae25b749f7f4dc5f327d0 |
|
index.php |
30da6c683deabf32eb9d4877bdad2f06 |
2bd744241613ffade44614e43b68f75e18894c0a |
|
login.php |
8e8b10174ce4515892b05ac61709bff4 |
d2d249cfe7727dd05a3a1e5e93bcec98967cff25 |
|
loginjsf.php |
09afb958e39ffc05b5abd42b335a00db |
734852654d89a9012d8b384ce61d421a8a313bf0 |
|
rondomico.php |
27ce3722396a2516008c927f01973e82 |
5687e7689ed076ae5354b25bb21c14615155133c |
Below I’ll show snippets from a couple of the files the attacker leveraged.
Erro.php
The files does most of the work for the attacker. It takes the credentials inputted into the logon form and logs them to a text file that starts with DESKTOP-- and then redirects the victim to the legitimate AWS console.
<?php
session_start();
$sessionav1 = $_SESSION['sessao'];
if(isset($_POST['password'])):
$password = addslashes(htmlspecialchars_decode($_POST['password']));
$myFile = "./loginsamazon2023/" . "DESKTOP"."--"."$sessionav1" . ".txt";
$fh = fopen($myFile, 'a') or die("Impossaivel abrir arquivo.");
$stringData =
"SENHA: $password
";
fwrite($fh, $stringData);
fclose($fh);
sleep(1);
?>randomico.php
This file assigns a random number to act as a session id, while also logging the IP Address:
<?php
session_start();
$tempocoderphp = time();
$rondomicocoderphp = rand(1000, 100000);
$ta = "$tempocoderphp.$rondomicocoderphp";
$ip_usuario = $_SERVER['REMOTE_ADDR'];
$_SESSION['sessao'] = md5($ta);
?>Targeting
Based on many attributes; to include the attacker source, language of files, the victims of this campaign as well as the victims of other campaigns also perpetrated from this attacker infrastructure, we highly suspect that the attacker is Brazilian and is also targeting Brazilian AWS users. We suspect that the ads are likely targeted to Brazilian language users as well.
Indicators
|
Indicator |
Type |
Notes |
|---|---|---|
|
3b716d9f3e2e772907aae066d4d0f1a8 |
MD5 |
erro.php |
|
3bb3675499ba5c65f4315ddc382352c1366e87b6 |
SHA1 |
erro.php |
|
338b3177e56cabdf43a6019dd04d2725 |
MD5 |
idconta.html |
|
e128fc62ec9ac913606ae25b749f7f4dc5f327d0 |
SHA1 |
idconta.html |
|
30da6c683deabf32eb9d4877bdad2f06 |
MD5 |
index.php |
|
2bd744241613ffade44614e43b68f75e18894c0a |
SHA1 |
index.php |
|
8e8b10174ce4515892b05ac61709bff4 |
MD5 |
login.php |
|
d2d249cfe7727dd05a3a1e5e93bcec98967cff25 |
SHA1 |
login.php |
|
09afb958e39ffc05b5abd42b335a00db |
MD5 |
loginjsf.php |
|
734852654d89a9012d8b384ce61d421a8a313bf0 |
SHA1 |
loginjsf.php |
|
27ce3722396a2516008c927f01973e82 |
MD5 |
rondomico.php |
|
5687e7689ed076ae5354b25bb21c14615155133c |
SHA1 |
rondomico.php |
|
aws1-us-west[.]info |
Domain |
Hosting of the watering hole phish |
|
104.21.39[.]144 |
IPv4 |
CloudFlare IP |
|
5.8.33[.]175 |
IPv4 |
Attacker web server |
|
pontos-itau[.]cloud |
Domain |
Also owned by this attacker though not part of this specific campaign. Currently resolves to 104.21.3.105 (CloudFlare) but is hosted on 5.8.33[.]175 |
|
190.83.43[.]37 |
IPv4 |
Attacker source address |



.png)





.png?width=767&name=image%20(9).png)


