
Permiso Releases Suite of Open-Source Tools to Bolster Detection Capabilities for Past,Present and Future Attacks
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Release Marks Ten Open-Source Tools the Startup Has Launched So Far This Year
PALO ALTO, CA – November 7, 2024 - Permiso, the leader in real-time identity security, has released a suite of three open-source tools that help security teams bolster their detection capabilities for a variety of different attacks. The P0 Labs team -- the threat research arm of Permiso -- has launched a total of ten open-source tools to date, developed from their ongoing threat research and observations from real-world attacks.
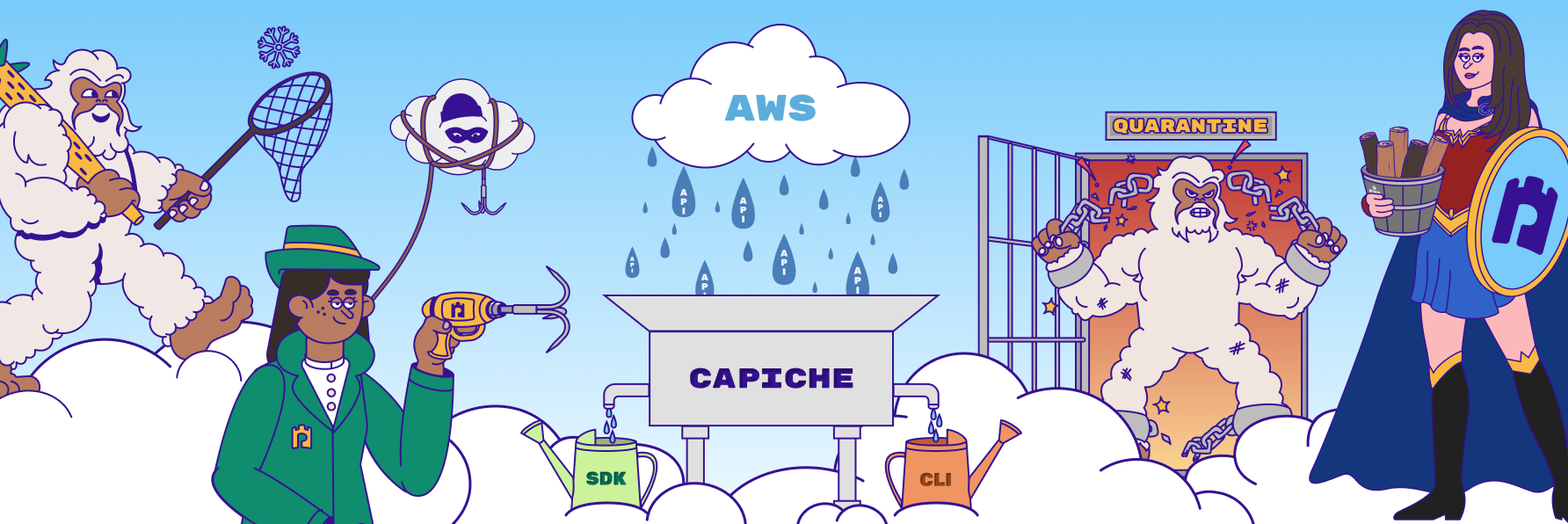
Earlier this year, Permiso launched YetiHunter, an open-source tool that detects indicators of compromise in Snowflake environments. They also released CloudGrappler which queries high-fidelity and single-event detections related to well-known threat actors in popular cloud environments such as AWS and Azure. Permiso, composed of former FireEye/Mandiant staff, has developed over 1,400 detection rules in their product as a result of their ongoing threat research. A subset of these rules has been incorporated into a multitude of open-source projects that allow security teams to uplevel their detection capabilities in a variety of different environments.
“The learning curve for detection in the cloud is steep, and our goal is to help security teams bolster their detections across their cloud environments without having to purchase commercial software solutions like a SIEM,” said Permiso Co-founder and Co-CEO Jason Martin. “We are committed to providing resources that can help the broader security community defend against the TTPs of modern threat actors.”
In the suite of projects is DetentionDodger which finds identities with leaked credentials and their potential impact. DetentionDodger will list all the identities with a Quarantine Policy (version 1-3) and look for failed policy attachments of a Quarantine Policy in CloudTrail Logs to generate a list of users with leaked credentials. It also lists all the inline and attached policies of the user and each group it is part of to determine the impact based on privileges.
BucketShield is a monitoring and alerting system built for AWS S3 buckets and CloudTrail logs. It ensures the consistent flow of logs from AWS services into S3 buckets and mitigates potential misconfigurations that could interrupt log collection. With real-time tracking of IAM roles, KMS configurations, and S3 log flows, BucketShield ensures that every critical event is recorded, and your cloud remains audit-ready.
Finally, CAPICHE Detection Framework (Cloud API Conversion Helper Express) is an open-source tool designed to simplify each step of the cloud API detection translation pipeline. It enables any defender to instantly create a multitude of different detection rules from groupings of APIs, even if the complete API names are unknown.
“The collection of these three tools help security teams immediately hone their detections and bolster their defenses against a variety of cloud-based attacks,” said Principal Threat Researcher Daniel Bohannon. “This isn’t just to help better defend against future attacks but addresses key attack vectors in their environments that could be indicative of past or present compromise.”
ABOUT PERMISO
Permiso Security is dedicated to reimagining identity security for the modern, cloud-first enterprise. We provide real-time identity security across all environments, addressing the complex challenges of securing both human and non-human identities in today's distributed IT landscapes. By offering the industry’s first combined Identity Security Posture Management (ISPM) with Identity Threat Detection and Response (ITDR) solution across the IdP, IaaS, PaaS and SaaS layers, we bridge the security gap of siloed cloud security tools. Our unique approach enables organizations to track the full identity footprint across multiple authentication boundaries, providing unrivaled identity security defense.
.



.png)





%20(2).png?width=767&name=Blog%20Image%20(892%20x%20298)%20(2).png)
.png?width=767&name=(970x250).png)
