
8 Critical AI Security Challenges and How Permiso Solves Them
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
AI adoption is accelerating faster than security teams can track it. While organizations rush to deploy AI agents and integrate AI services across their operations, they're creating massive blind spots in their security posture. The problem isn't just technical complexity. It's visibility. Most organizations can't answer basic questions about their AI footprint: Who's using AI? Which services are they accessing? What data are they sharing?
Traditional security tools fail here because they treat AI as a separate problem requiring separate solutions. The reality is simpler and more challenging: AI security is identity security. Every interaction with an AI model, whether by an employee querying ChatGPT or an autonomous agent calling APIs, is an identity-driven event. When you provision an AI agent, you're extending your identity perimeter. When developers grant AI systems access using their own accounts, every compromised agent becomes a pathway to human credentials.
Here are the eight most critical AI security challenges organizations face today, and how Permiso's identity-centric platform addresses each one.
1. Invisible Shadow AI Usage
Challenge: Employees use personal accounts on AI services like ChatGPT, Claude, or DeepSeek, bypassing corporate security policies and creating unmonitored attack surfaces. Organizations lack visibility into 80% of actual AI activity because traditional tools only track licensing and static configurations.
How Permiso Solves It: Runtime intelligence discovers actual AI usage patterns beyond static licensing data. While other tools tell you who has a license, Permiso shows you how that license is being used and what other AI services are being accessed without one. The platform tracks shadow AI usage through personal accounts, monitors AI service access through federated authentication, and flags unauthorized usage in real time. This shifts security from guesswork to data-driven response.
2. Over-Permissioned AI Agents
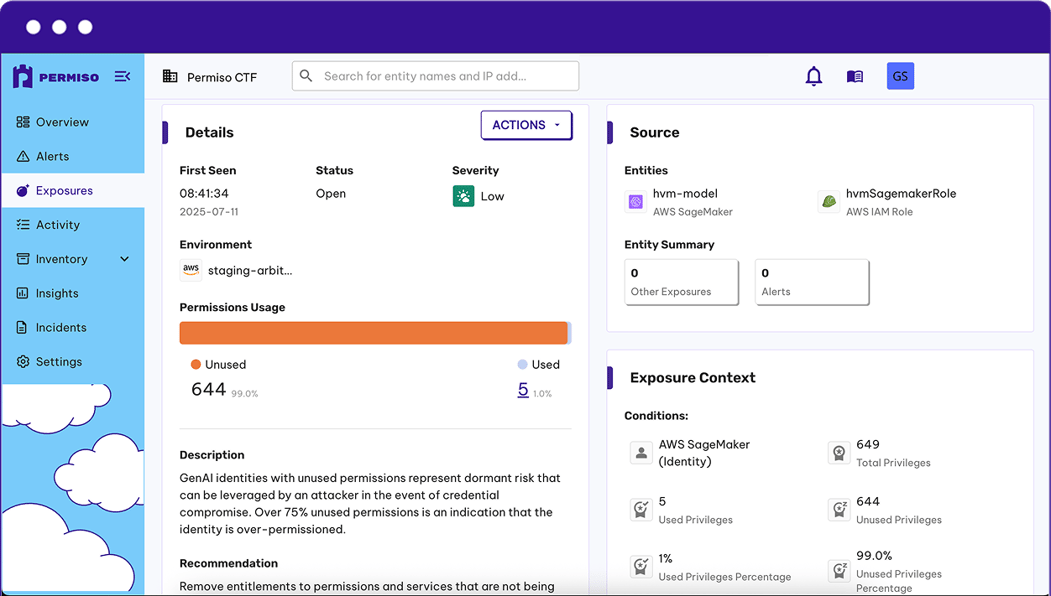
Challenge: AI agents operate with excessive permissions, often having up to 90% unused permissions similar to traditional service accounts. This creates massive unnecessary risk as AI agents require broad API access across multiple domains simultaneously: LLM providers, enterprise APIs, cloud services, and data stores.
How Permiso Solves It: Permiso analyzes AI infrastructure and agents for over-permissioning, identifying unused permissions and enabling least-privilege enforcement without disrupting development workflows. The platform discovers AI agents with excessive permissions and provides concrete recommendations for rightsizing. Our research shows agents operating with 90% unused permissions. This insight allows security teams to shrink the attack surface dramatically while keeping developers productive.
3. Lack of AI Identity Lifecycle Management
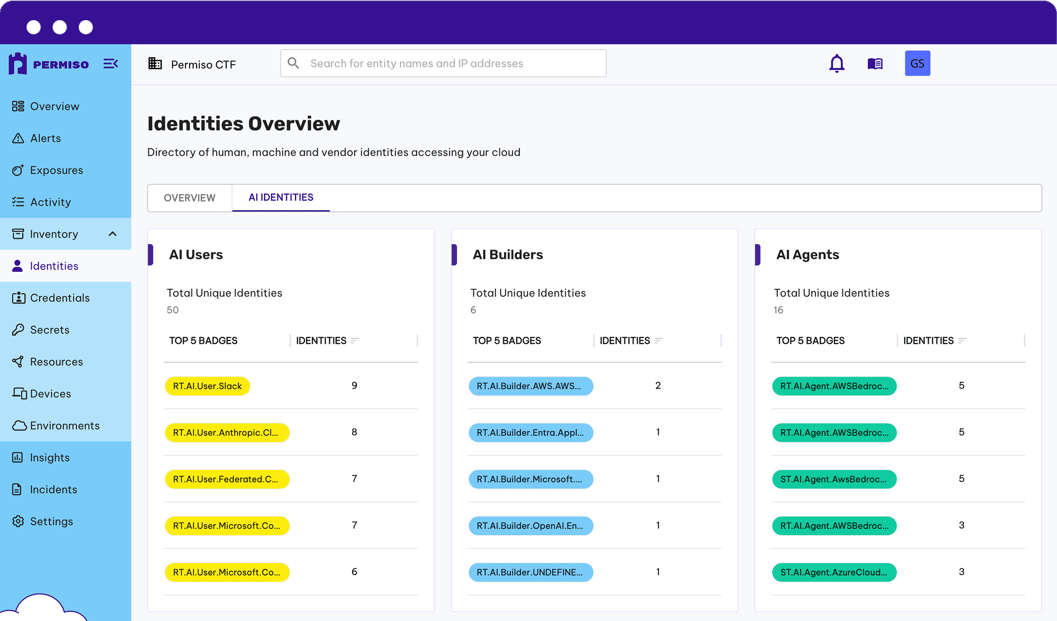
Challenge: There's no parallel process for AI agent lifecycle management. Organizations struggle to maintain an accurate inventory of their AI identities as agents proliferate. Fewer than 40% of organizations currently govern AI agents even as they multiply across development teams and business units. Without visibility into which agents exist, which are active, and which should be decommissioned, governance becomes impossible.
How Permiso Solves It: Permiso's Universal Identity Graph provides complete inventory of AI users, builders, and agents with continuous tracking throughout their lifecycle. The platform categorizes AI identities into three distinct groups (users, builders, agents) and maintains visibility from creation through modification to usage patterns. Security teams gain the foundational visibility needed to enforce policies, identify stale agents, and maintain control as AI deployments scale.
4. Multi-Protocol Identity Confusion
Challenge: AI agents interact with multiple authentication providers and protocols simultaneously: enterprise APIs via OAuth, LLM services via API keys, cloud resources via managed identities. Permission scopes, token formats, and validation requirements differ across each interaction, making consistent access control nearly impossible. Each protocol boundary introduces potential misconfigurations and security gaps.
How Permiso Solves It: Permiso treats AI security as an extension of identity security, applying the same comprehensive framework used for human and non-human identities. The platform provides unified visibility across all authentication protocols and federated access paths, mapping exposures across different AI service boundaries. Instead of managing each protocol separately, security teams get a single view of how identities authenticate and what access they hold, regardless of the underlying protocol.
5. Autonomous Identity Modification and Privilege Escalation
Challenge: AI agents request permission escalation based on task analysis without human authorization. Agents modify their own identity claims mid-execution and spawn sub-agents without parent identity verification, creating ungovernable trust relationships. Traditional security controls designed for static identities fail when identities can modify themselves autonomously.
How Permiso Solves It: Behavioral anomaly detection continuously monitors runtime behavior of every AI identity, establishing baselines of normal activity and triggering alerts when AI agents operate outside intended scope. Integration with the MITRE ATLAS framework enables AI-specific threat detection for escalation attempts. If a developer's account that normally works on a specific project suddenly attempts privilege escalation or spawns unexpected sub-agents, the system flags the behavior immediately.
6. Sensitive Data Leakage to External AI Models
Challenge: 80% of organizations have encountered risky behaviors from AI agents including improper data exposure. Autonomous agents exchange data without oversight, obscuring leaks and evading audits. Employees and AI agents share sensitive documents, proprietary data, and personally identifiable information with external AI models, often without realizing the security implications.
How Permiso Solves It: DLP (Data Loss Prevention) integrations flag and prevent sharing of sensitive documents with external AI models, whether initiated by human workers or autonomous AI agents. Runtime intelligence tracks what data is being accessed and shared across AI service boundaries. In one recent deployment, Permiso helped a customer identify several employees sharing sensitive financial documents with external AI models through a critical DLP integration, preventing potential data exposure before it escalated.
7. Chained Vulnerabilities Across AI Agent Networks
Challenge: A flaw in one agent cascades across tasks to other agents, amplifying risks. Cross-agent task escalation allows malicious agents to exploit trust mechanisms and gain unauthorized privileges. Agent-to-agent authentication flows lack standard audit trails, creating identity accountability gaps. When agents call other agents, the chain of custody becomes opaque.
How Permiso Solves It: The Universal Identity Graph stitches together all AI identities (users, builders, agents) with human and non-human identities, revealing relationship chains that could be exploited. Session-level evidence and runtime data provide forensic trails for understanding how identities interact across agent networks. Security teams can trace the complete path of authentication and authorization, seeing not just individual actions but how those actions connect across the entire agent ecosystem.
8. Lack of Attribution and Accountability
Challenge: When AI agents run using human credentials or shared service accounts, attribution becomes impossible. Organizations cannot answer fundamental questions: Who is using AI? Who's building it? Which agents are operating? What exactly are they doing? Without clear attribution, incident response and forensic investigation become guessing games.
How Permiso Solves It: Detailed attribution shows exactly how each AI identity earned its classification, backed by session-level evidence and runtime data. Security teams can see not just that a developer is using an AI model, but which project they were working on, what data they accessed, and what actions they took. Granular visibility extends from specific AI services accessed to the precise types of activities performed, providing a robust forensic trail for any incident investigation.
Permiso's Unified Approach to AI Security
These eight challenges share a common thread: they're all identity problems. The fragmented approach of deploying separate tools for AI monitoring, agent management, and user activity creates the blind spots that attackers exploit. Permiso rejects this model entirely.
We treat AI security as identity security rather than a separate silo, applying proven identity security principles to AI. This fundamental shift means you're not learning a new security paradigm or deploying yet another disconnected tool. You're extending your existing identity security framework to cover AI users, builders, and agents with the same rigor you apply to human and non-human identities.
Critically, Permiso combines runtime intelligence with static configuration tracking to capture the 80% of AI activity that static tools miss. While traditional tools only see licensing and configuration data, our platform monitors actual usage patterns, federated authentication flows, and real-time behavior. This is the difference between knowing who has access and knowing what they're actually doing with it.
Our platform applies a proven three-pillar framework to the AI identity ecosystem. First, Discover: complete inventory of all AI identities with detailed attribution and runtime evidence. Second, Protect: enforce least privilege at scale by identifying over-permissioned agents and unused access rights. Third, Defend: behavioral anomaly detection that monitors every AI identity continuously and triggers alerts when behavior deviates from established baselines.
Whether an employee is using ChatGPT, a developer is building with GitHub Copilot, or an autonomous agent is executing tasks across your infrastructure, Permiso provides the visibility and control you need. Organizations running hundreds or thousands of AI agents need a platform that eliminates blind spots and provides full coverage against identity-driven threats. That's what Permiso delivers.
Ready to secure your AI identities? Contact us to see how Permiso can provide complete visibility into your AI security posture, or request a demo to see the platform in action.



.png)





.png?width=767&name=Permiso%20Discover%20-%20Blog%20Image%20(892x298).png)



