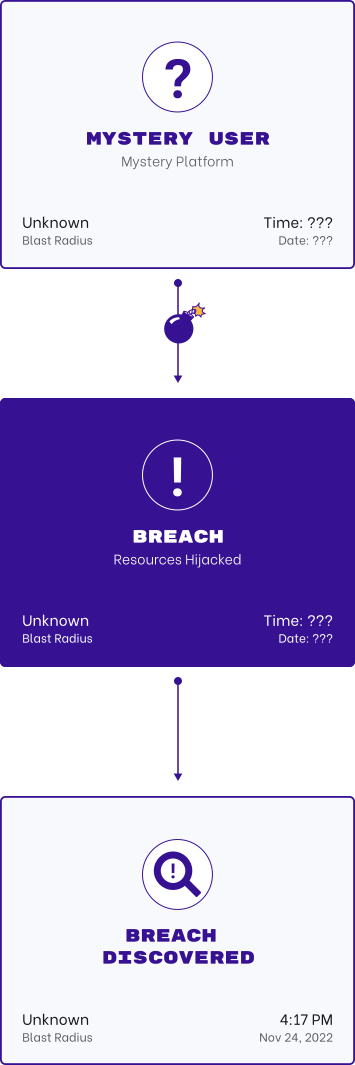
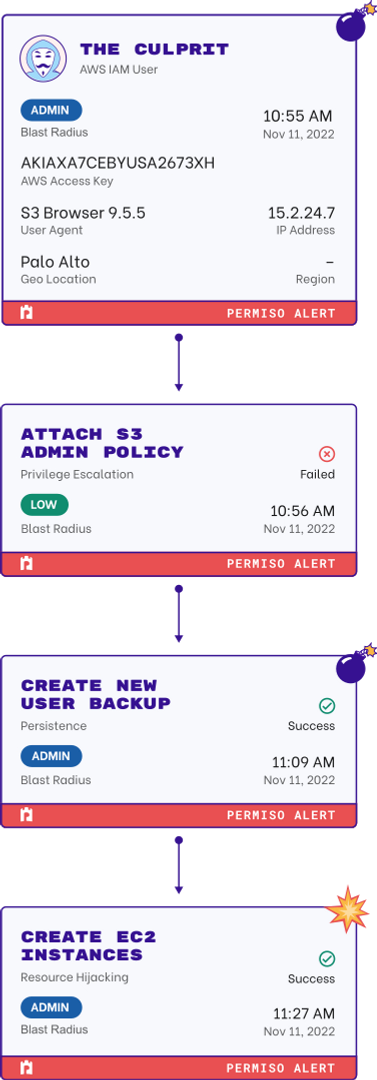
Secure All Identities In All Environments
Permiso inventories all human and non-human identities, assesses exposure risk for those identities, and monitors them for suspicious and malicious activity in your identity providers, cloud service providers and SaaS applications.
Detect identity risk and threats for all of your users in the cloud and on-prem environments to prevent account takeover and reduce identity risk.
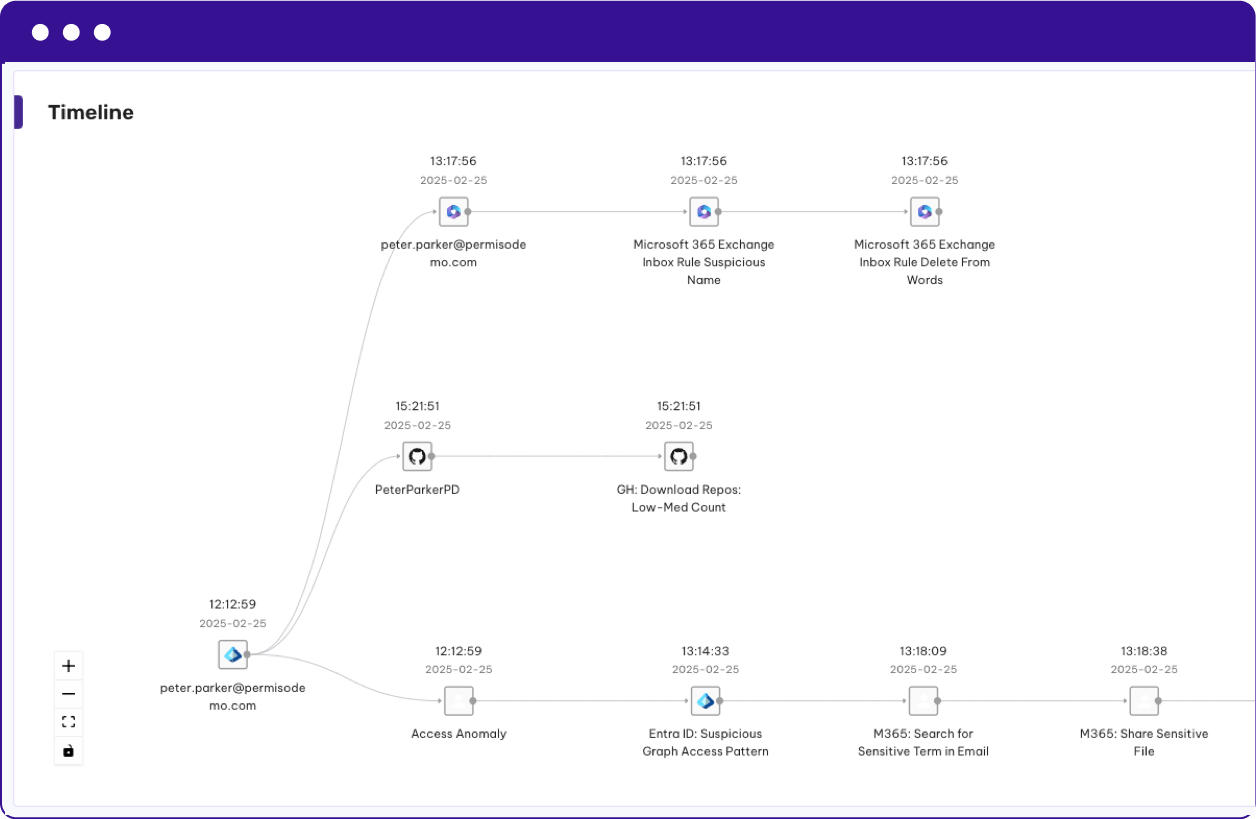
Identity Visibility and Intelligence Platform
Attain a comprehensive understanding of your true identify attack surface by stitching human, non-human, and AI-based identities together. Gain transparency into risk through Permiso’s Universal Identity Graph. Proactively manage all entity identity risk for human, non-human and AI identities, across all environments, from a single pane of glass.
With Permiso you can:
- Comprehensive Identity Visbility
- Identity Classification
- Universal Identity Stitching
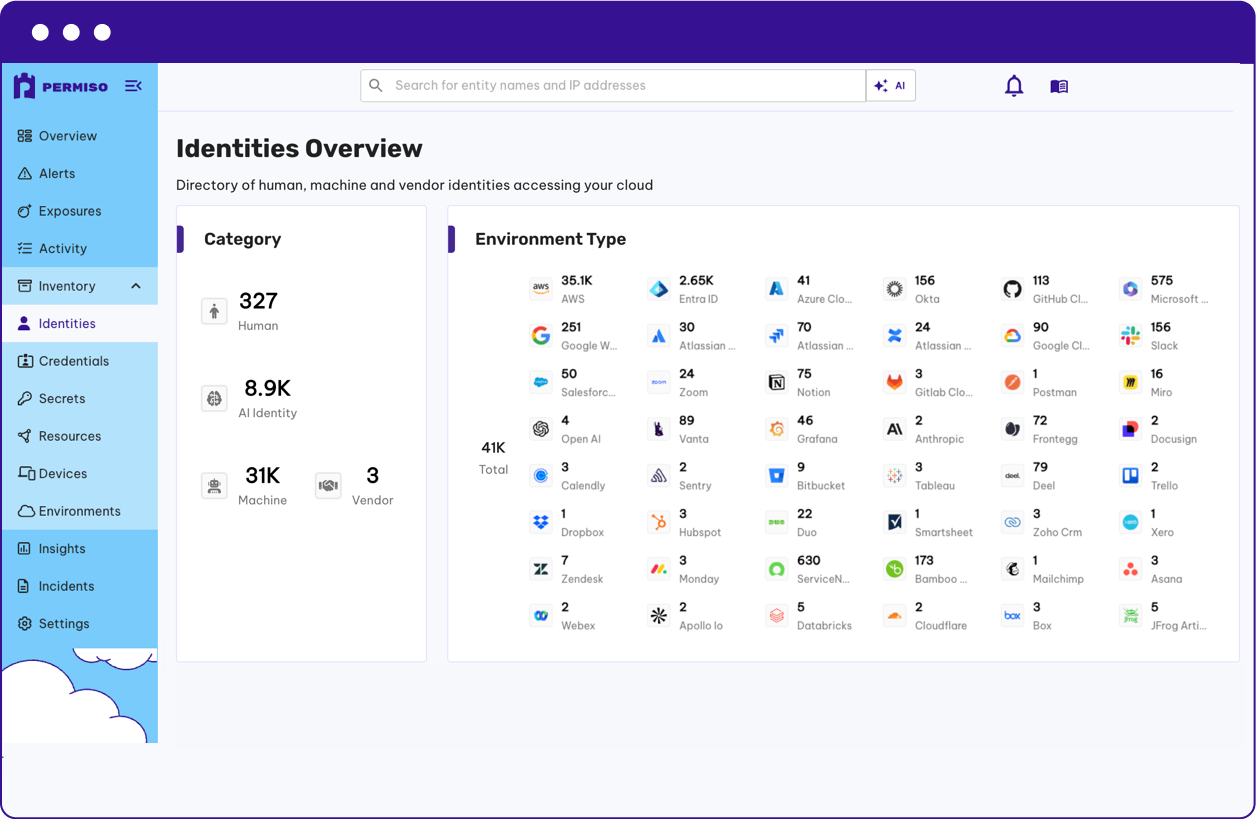
Identity Security Posture Management
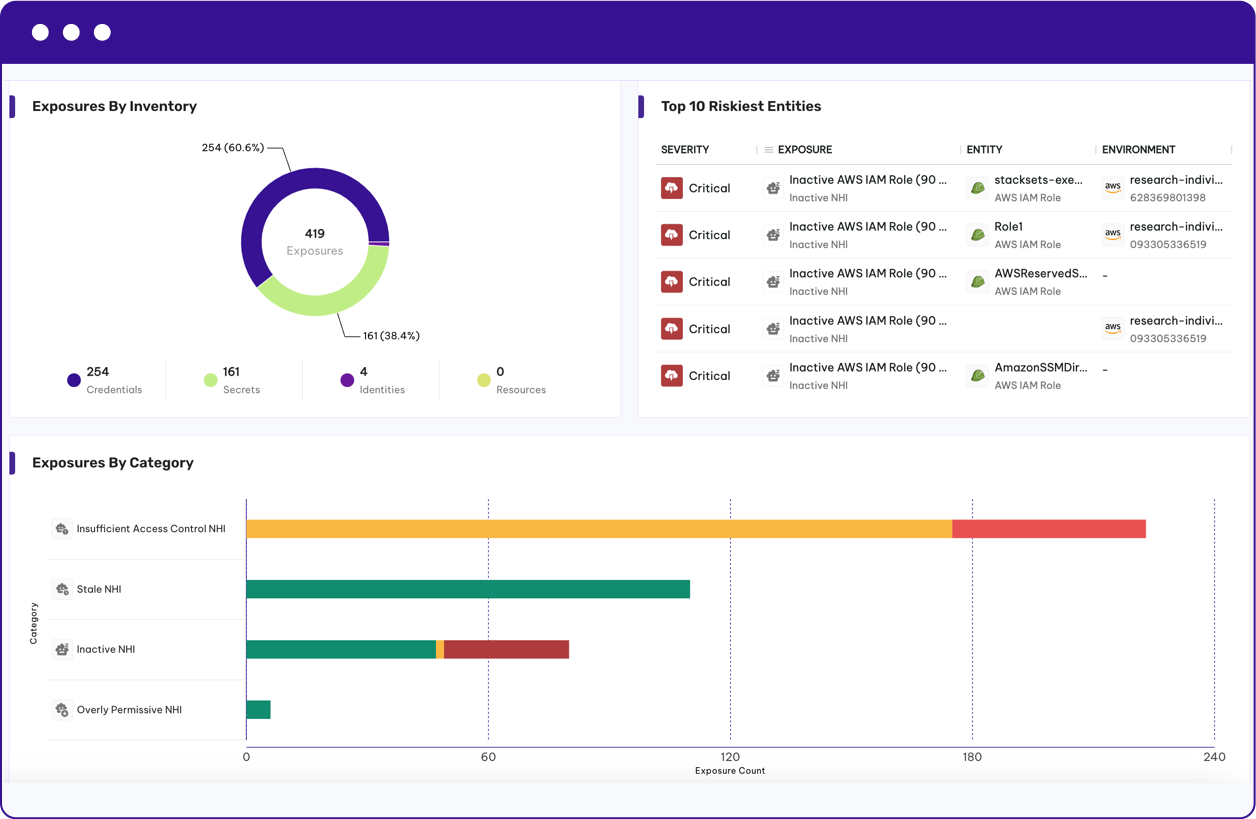
Continuously evaluate the risk posture of identities based on usage patterns, exposure, and entitlements. Surface and quantify high-risk identities, stale access, and toxic combinations across human, vendor, AI, and non-human accounts.*
With Permiso you can detect:
- Assess your identity attack surface risk
- Remove zombie identities and accounts
- Reduce unnecessary privileges
Identity Threat Detection and Response
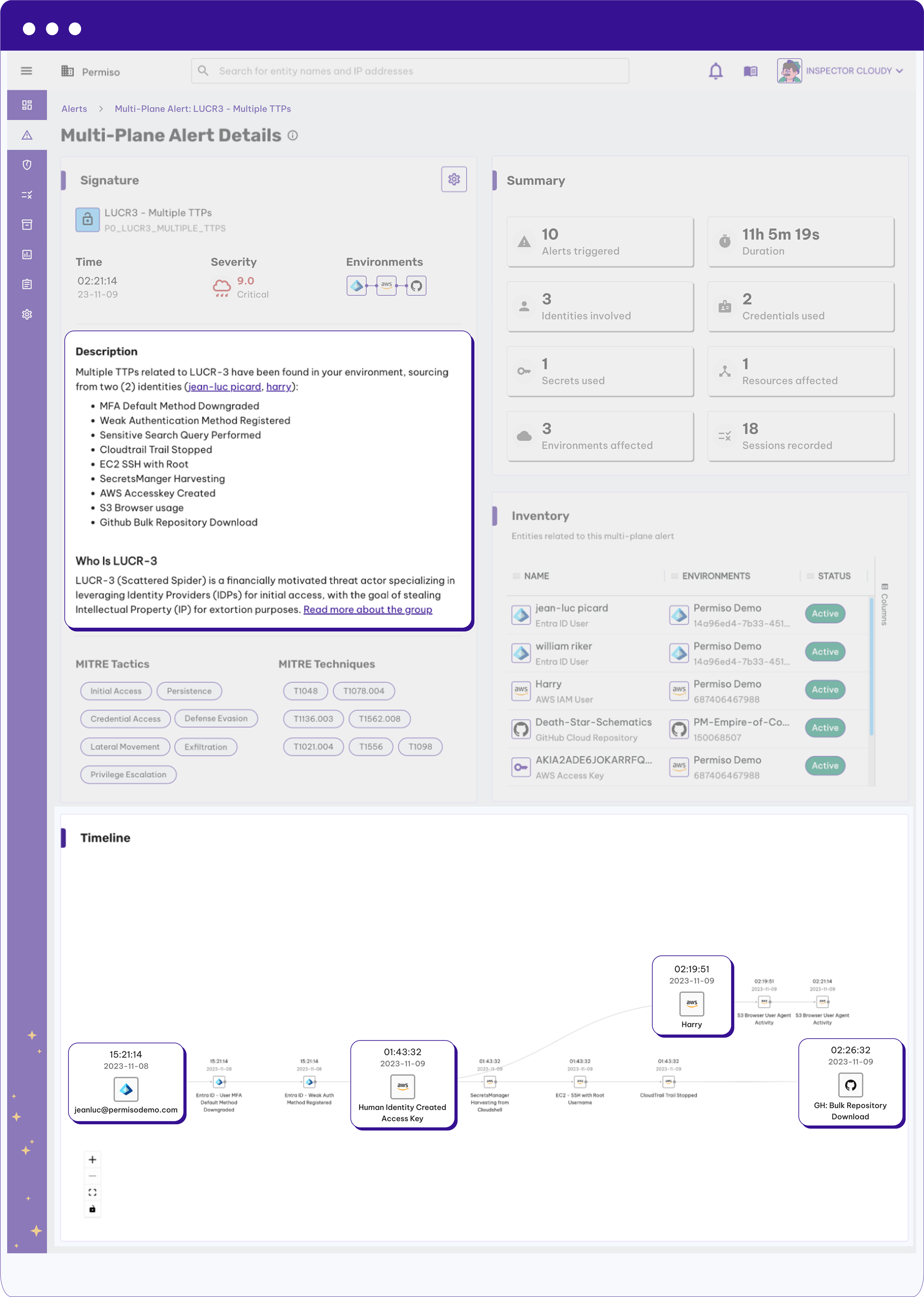
Permiso monitors activity and correlates user behavior across those environments to produce incredibly high-fidelity identity security alerts across AWS, Azure, Okta, M365, and more, significantly improving Mean Time To Detect (MTTD) and Mean Time To Respond (MTTR).
With Permiso you can detect:
- Credential Compromise
- Account Takeover
- Insider Threat



Secure AI Identities
Permiso delivers world-class identity security for AI users, builders, and, agents in a single platform, allowing organizations to manage risk while leveraging powerful new technologies. As agentic AI drives innovation and productivity gains, it's essential that this emerging technology serves as a business enabler without introducing disproportionate risk.
With Permiso you can:
- Gain comprehensive visibility into the AI users, builders and agents that are operating in your environment
- Answer the question Who is using AI? Who's building it? Which agents are operating? What exactly are they doing?"
- Future-proof coverage against evolving AI adoption patterns and attack methods.
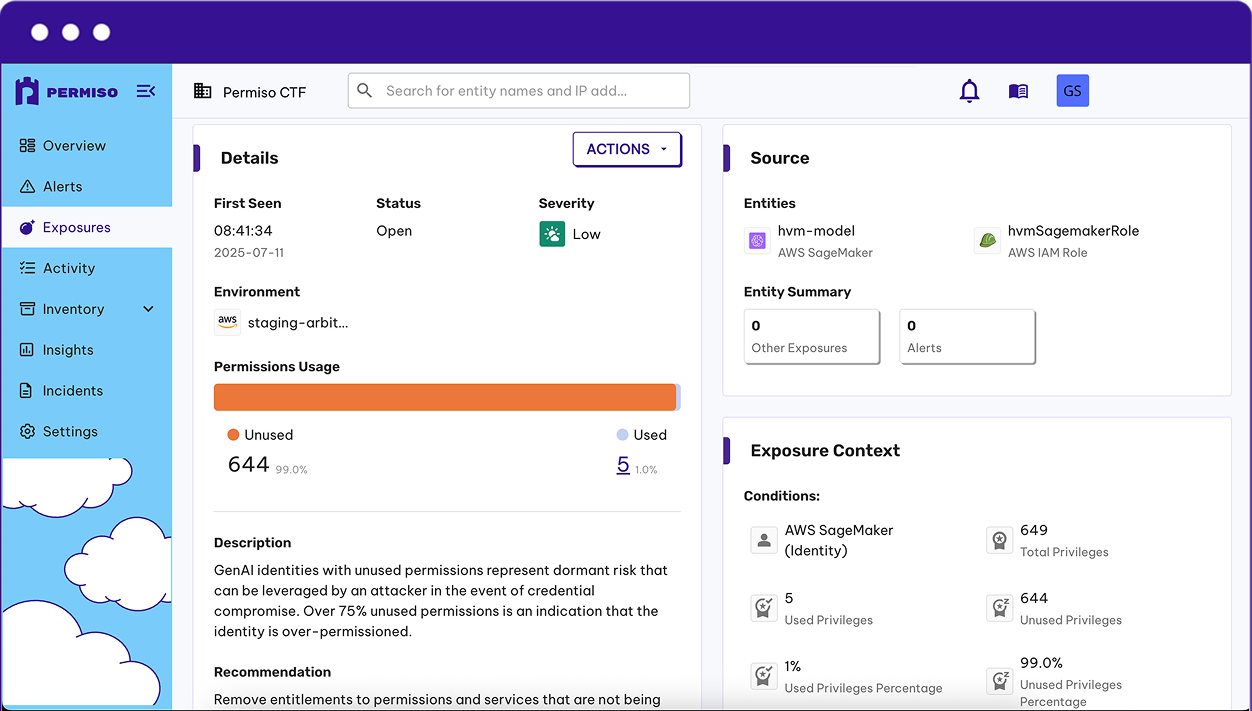
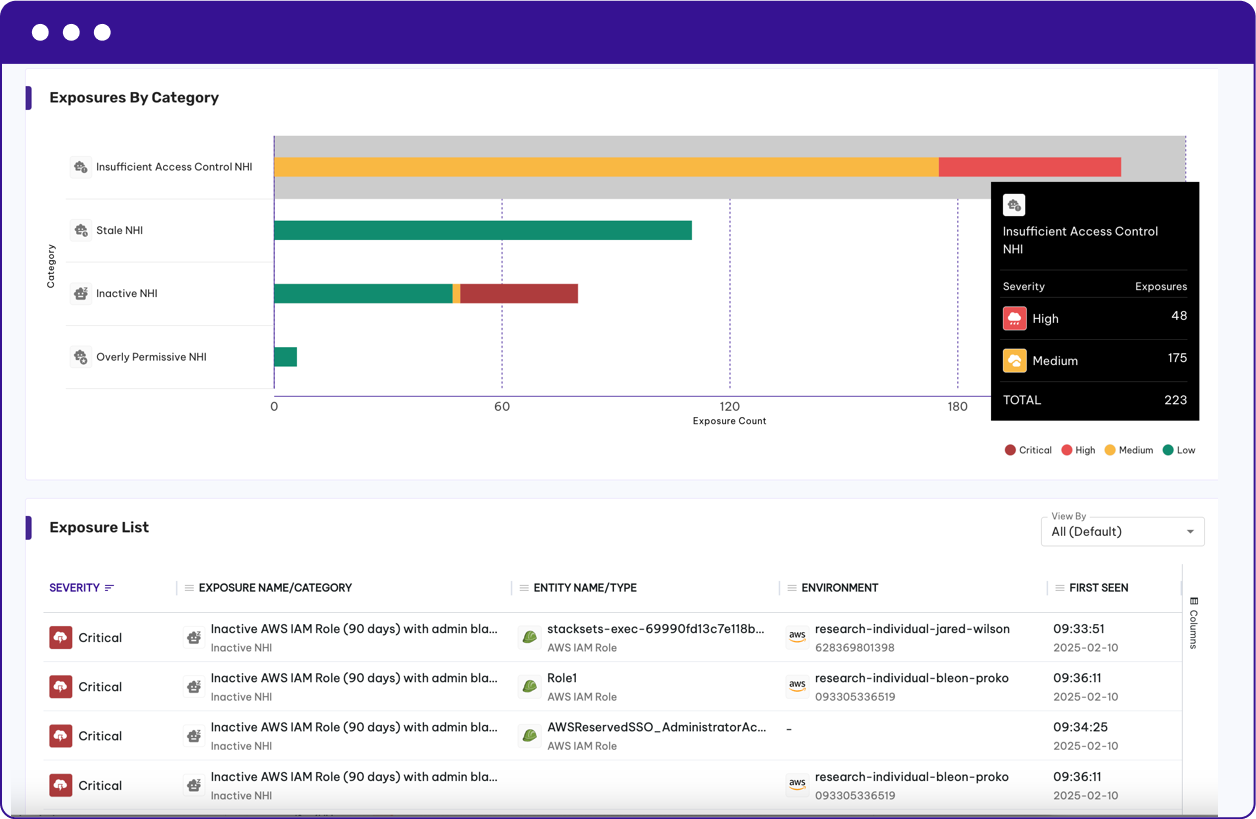
Secure Non-Human Identities
Permiso monitors all of your keys, tokens, roles, groups and service accounts by inventoring them, and monitoring them for supsicious and malicious behavior
With Permiso you can:
- Inventory all of your NHIs in your identity providers, Iaas, PaaS and SaaS environments
- Quickly identify orphaned, stale or overprivleged NHIs
- Monitor the use of your non-human identities at runtime to detect anomalous behavior
Why Traditional Tools Fail Against Modern Attacks
Security teams have attempted to leverage a combination of existing technologies like SIEM, CNAPP and CWP to try and solve the cloud threat detection problem. These tools weren't built to solve the modern attacks observed today where attackers hop between cloud environments and mask themselves with valid credentials.
Traditional tools have siloed focus (IaaS only), are event driven (noisy and high volume), and lack identity attribution context to expedite investigation time.


Want to see more?




.png)